Winja usage checks the safety of data
One of the reasons leading to the situation of computers infected with viruses and malicious code is that users download software and applications from floating sources, but not in official websites with high reliability. However, there are many cases where you download software with attached data sent from e-mail of acquaintances, or download certain files from the Internet, and it is difficult to confirm that the email address has been hijacked by hackers. to distribute malicious code or not. If so, you can use programs that check the safety of files, such as the Winja tool.
Winja is Phrozen Software's free security software, which checks the security of data on your computer or scans the system to check if there is any danger. Especially, Winja software will send test data to 58 famous security firms such as Bitdefender, Kaspersky, Avast, BKAV, . to be sure of the safety of any file. The following article of Network Administrator will guide you how to use Winja to conduct file checking, access path and system.
Step 1:
You can access the link below to access Phrozen Software's page and download the software.
- https://www.phrozen.io/download/1
Winja's capacity is quite dull, doesn't take up a lot of system resources like many other software. Click on the software's .exe file to proceed with the installation. In the first interface, click Next to continue.
Step 2:
Go to the Winja user interface, click on I accept the agreement , then click the Next button below.
Step 3:
The next step is to click Next . then click Install to proceed to install Winja on the computer.
Finally, the user waits for the software installation process to be successful and then press Finish to finish.
Step 4:
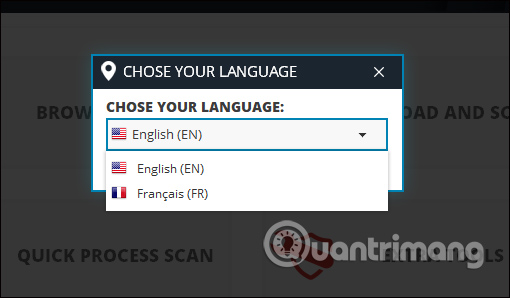
Launch the application and in the first interface, the software will give you the choice of language, in two languages, English and French. Here we will use English.
Step 5:
The main interface of the software is relatively simple with 4 options equivalent to 4 features to use in checking files and systems. To proceed to check the safety of the downloaded file on your computer, click on the Browse for file option .

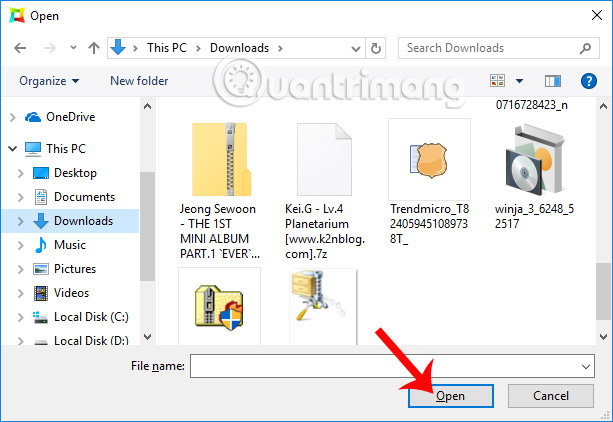
Access the folder on your computer, click on the file you want to check and click Open .
Step 6:
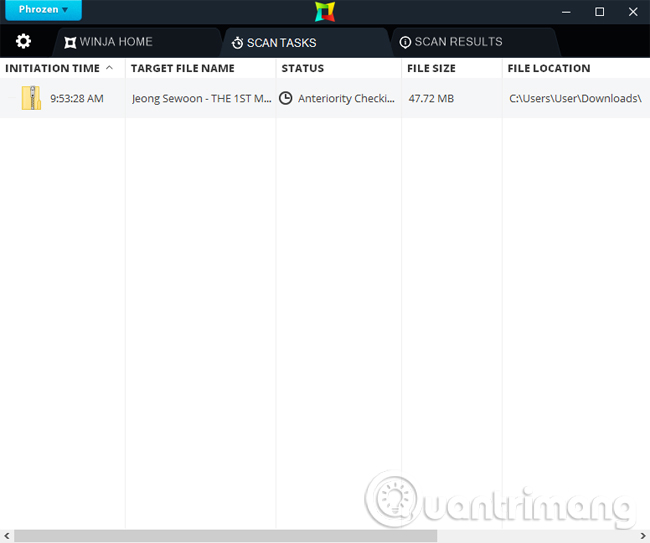
We wait for the Winja process to upload the data to the system and then process it. This process requires a computer to connect to the Internet to connect to the server system.
Step 7:
When the checkout process is completed, a message board appears at the bottom right of the screen interface.
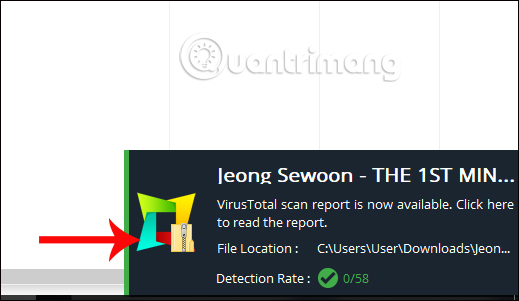
Users click directly on that message to see the details of the test data. Or else, at the data scanning interface on Winja click on the Scan Results section to store the file scanning history to see the results.
Step 8:
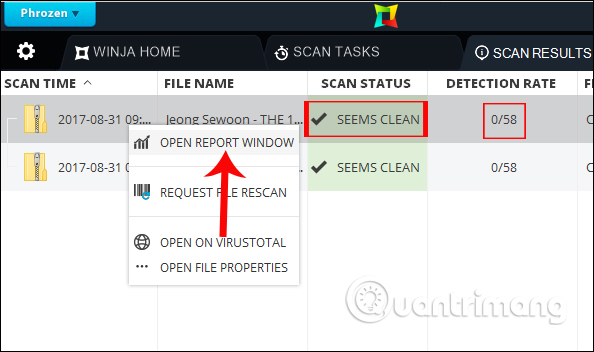
Switch to the new interface. There will be a list of checked files. You need to pay attention to 2 columns, which is Scan status if Seems Clean and Detection Rate notifications are 0/58 , meaning that the software is safe. None of the Web sites in 58 sites found a problem.
Next, right-click on the scanned file and select the Open report window to see the detailed results from the 58 secure websites.
Step 8:
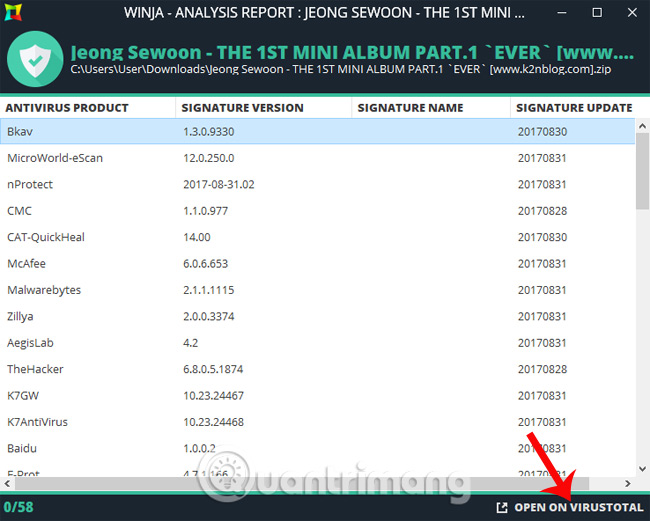
In the file test result interface, we will see a data checklist from the 58 sites on the Winja tool. Alternatively, click Open on Virustotal to see the data test results on this famous online file check service.
If one of those 58 websites warns of danger, you should reconsider it before installing.
Step 9:
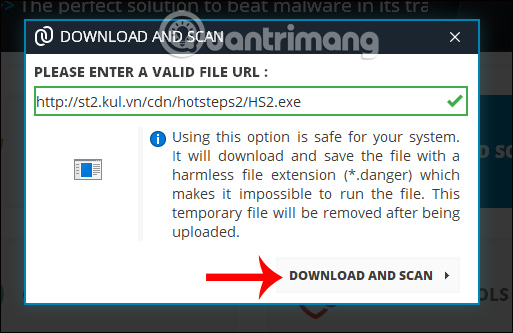
In addition, you can check the reliability of the file download link to your computer. Click on the Download and scan option on the main interface of the software.
Next in this dialog box, paste the download path and click Download and scan below. The software will proceed to download the file in security mode, then perform file scanning.
Step 10:
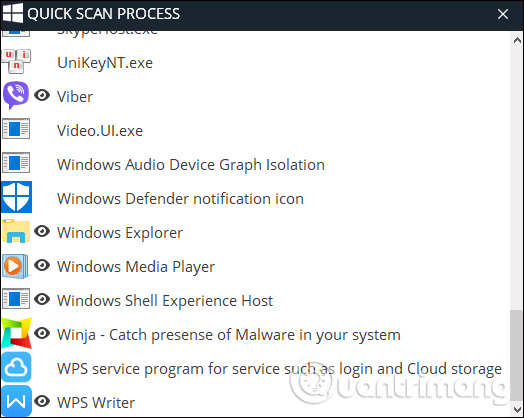
The program's Quick Process Scan option checks the background processes in Windows. In case of detecting a strange process, double click the mouse to check immediately.
Step 11:
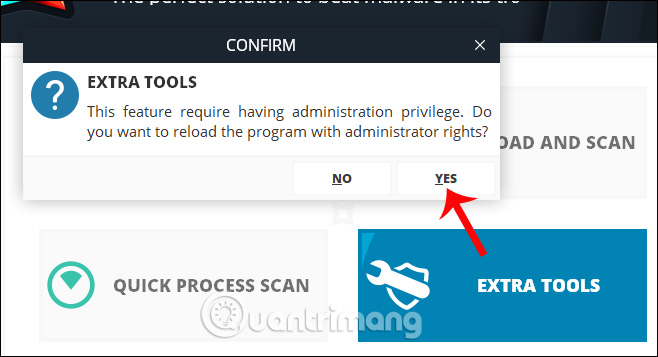
Extra Tools is an option to interfere more deeply into the system, using Admin privileges. A request table will appear, click Yes to agree.
However, if you have no experience in intensive processing, then using the other 3 test features also ensures the security quality.
With the Winja tool, we can easily check any file on the system, or check the link to download the file and then set the secure download mode with file scanning. With 58 famous security sites linked to the software, you will no longer worry whether the software contains viruses.
I wish you all success!