Fix for OpenVPN driver vulnerabilities that cause Windows systems to crash
Are you seeing the OpenVPN Blue Screen of Death error in your VPN app? This error stems from an OpenVPN driver vulnerability and requires a patch from the source. Since most major VPN providers use the OpenVPN protocol, your Windows device may be vulnerable to this critical error. Here's how to diagnose this error when it occurs and prevent serious PC issues.
OpenVPN Crashes Windows
OpenVPN is widely used in VPN applications. In June 2025, a serious buffer overflow vulnerability was found in OpenVPN's data channel switching (DCO) driver - "ovpn-dco-win", causing a blue screen of death.
This is not the first time. OpenVPN's plugin mechanism has long been a vulnerability, allowing for remote code execution or privilege escalation. In 2024, Microsoft discovered four bugs (CVE-2024-27459, CVE-2024-24974, CVE-2024-27903, CVE-2024-1305), the last of which caused a memory overflow in the Windows TAP driver, leading to a denial of service (DoS) issue.
If you are using a VPN product and have it set to launch on system reboot, you may encounter this error if you have not updated your OpenVPN client to the latest patch, "OpenVPN 2.7_alpha2" or higher. Your VPN provider will release a fix in their own Windows client, so update your VPN as soon as possible.

The DCO driver handles packet-level tasks like encryption, decryption, and routing, moving them from user space to the Windows kernel. Unlike WireGuard, OpenVPN's DCO operates in kernel space. Crashes mostly occur because these components interact closely with the operating system.
Previous kernel-level malware incidents have shown how difficult these issues can be to manage, and CVE-2025-50054's corrupted packets cause crashes due to low-level memory corruption.
Locate and disable OpenVPN driver in Windows PC
If you don't use OpenVPN, you can leave it disabled. Your VPN client may have its own driver installed, so check to see if it's available.
Open File Explorer . Go to C:WindowsSystem32Drivers . Look for OpenVPN related drivers like DCO driver – 'ovpn-dco.sys'.
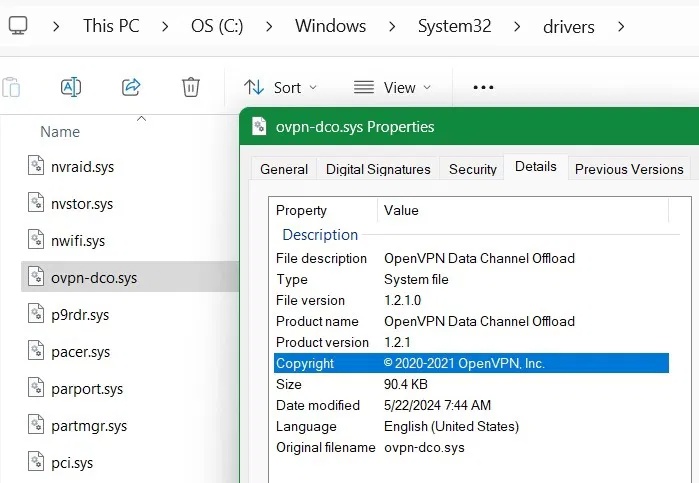
Other vulnerable OpenVPN drivers include TAP-Windows Adapter V9, 'tapwindows6.sys', Wintun driver, 'wintun.sys', and named pipe interfaces, such as '.pipeopenvpn'.
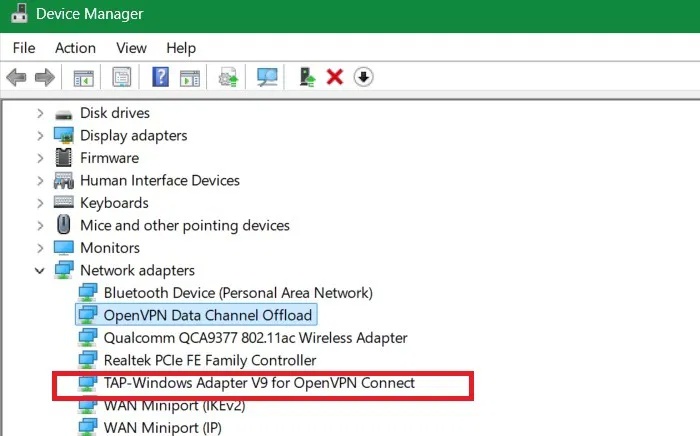
You can locate these drivers in Device Manager . In the Run command, type devmgmt.msc and go to Network Adapters . You should see the OpenVPN adapters on your system, such as DCO and TAP-Windows Adapter V9, listed here.
If you want to list all hidden OpenVPN drivers in your system, open PowerShell with admin rights . Now, enter the following command:
Get-WmiObject Win32_SystemDriver | Where-Object { $_.Name -like "*ovpn*" -or $_.Name -like "*tap*" } | Select-Object Name, State, PathName, StartModeYou can then choose to uninstall the OpenVPN app and manually remove all of its drivers. Sometimes they persist even after you uninstall the app.
On a VPN client like NordVPN or ExpressVPN , if you don't plan on using OpenVPN, switch to WireGuard.
Note : OpenVPN's complex codebase, old drivers, unprivileged processes, and slow patch adoption make it particularly dangerous on Windows. That's why Windows users should switch to WireGuard instead of OpenVPN.
Restrict OpenVPN driver access to PC permissions
OpenVPN's flexibility and deep integration into operating systems makes it susceptible to low-level bugs that can have serious consequences, especially on Windows.
To prevent this, you can restrict the corrupt OpenVPN driver's access to modify permissions (this solution ensures you don't have to uninstall your VPN client).
Open PowerShell with admin rights and enter the following command:
$driverPath = "C:WindowsSystem32driversovpn-dco.sys" icacls $driverPath /inheritance:r icacls $driverPath /grant:r "SYSTEM:R" "Administrators:R" icacls $driverPath /deny "Everyone:W" 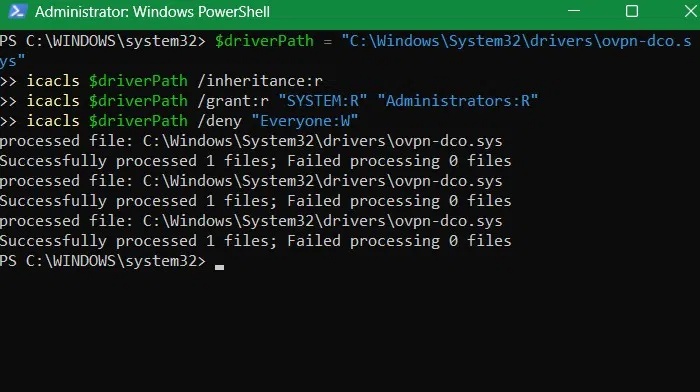
The above command clears inherited permissions to prevent accidental access. It also denies write access to everyone, including unprivileged users and malware, ensuring that driver issues don't affect your system.
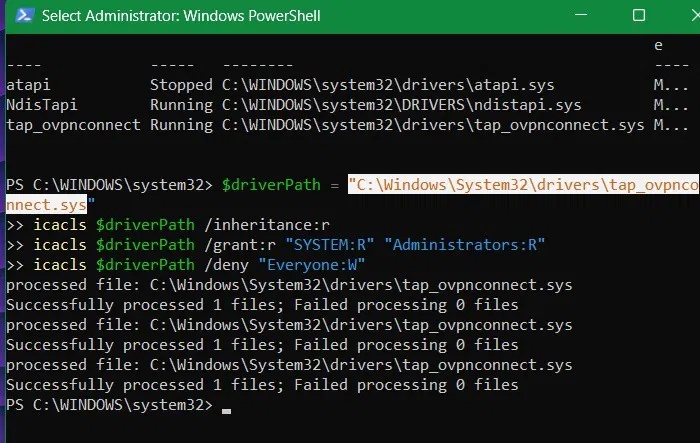
In the previous step, we saw how to list all hidden OpenVPN drivers. You can repeat the above command with a little tweak in the driver path to deny access to them in the same way. Here, we are denying access to TAP-Windows Adapter V9, 'tapwindows6.sys'.
Monitor BSoD crashes caused by OpenVPN drivers
While OpenVPN patches are released quickly, many users are still slow to update. There is a proactive way to monitor these issues from happening. First, download a utility called Blue Screen View and install it as instructed here.
Now, open PowerShell with admin rights and run the following script as shown. Replace the $nirDir path with the actual path of the folder where you installed the application. It will check recent crash dumps and flag any that list OpenVPN related drivers as the root cause.
# Set path to your BlueScreenView directory (update if needed) $nirDir = "C:ToolsBlueScreenView" # ← Change this to your actual path $csvPath = "$nirDirbsod.csv" # Monitoring loop while ($true) { # Run BlueScreenView in command-line mode and export to CSV Start-Process -FilePath "$nirDirBlueScreenView.exe" -ArgumentList "/scomma `"$csvPath`"" -Wait # Import and analyze results $bsods = Import-Csv $csvPath -Header Dumpfile, Timestamp, Reason, Errorcode, Param1, Param2, Param3, Param4, CausedByDriver $recent = $bsods | Where-Object { ($_.Timestamp -as [datetime]) -gt (Get-Date).AddMinutes(-10) -and $_.CausedByDriver -match "ovpn|tap|wintun" } if ($recent) { Write-Warning "⚠️ BSOD caused by OpenVPN-related driver in last 10 minutes!" $recent | Format-Table -AutoSize } else { Write-Host "✅ No recent OpenVPN-related BSODs." } Start-Sleep -Seconds 600 # Wait 10 minutes before checking again } 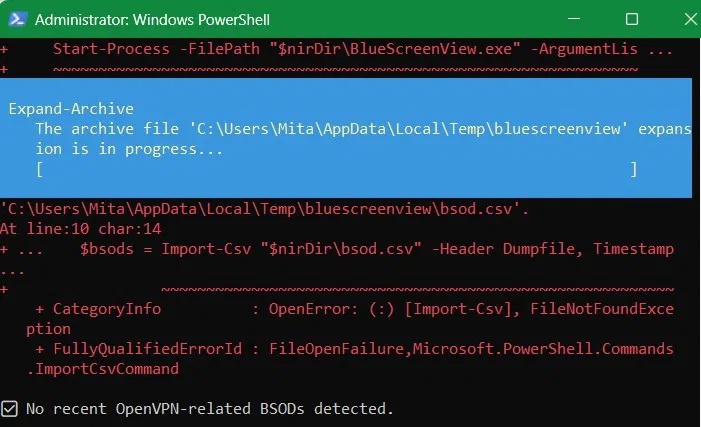
As shown in the results window above, no recent instances of BSoD crashes due to OpenVPN were detected.
Tip : Windows itself will release timely patches to fix issues caused by applications like OpenVPN. Check out our Windows update guide to monitor and prevent any BSoD issues that may affect your system.
Use software restriction policy for OpenVPN driver
On Windows Pro/Enterprise devices, you can use the software restriction policy in the Local Group Policy Editor to block the OpenVPN driver from executing randomly without your permission.
Open Group Policy Editor from the Run command by typing 'gpedit.msc' . Go to Computer Configuration -> Windows Settings -> Security Settings -> Software Restriction Policies -> Additional Rules .
Right click on the last item to select New Path Rule .
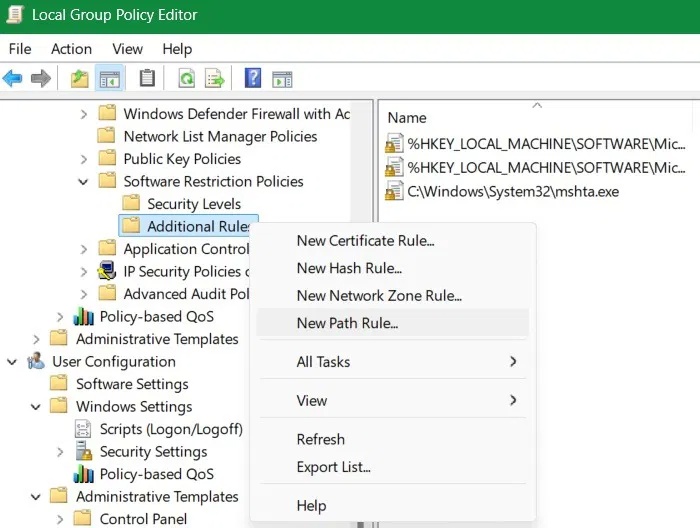
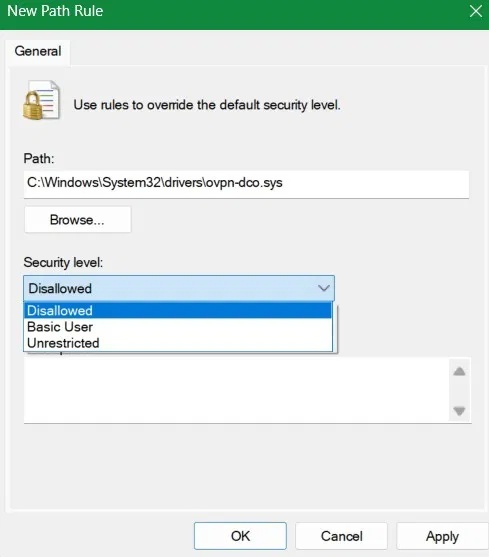
In the pop-up window that opens, copy-paste the driver path. In this case, I copied-pasted the driver path for OpenVPN's DCO. Select Disallowed , then press Apply -> OK . Now, repeat this method for all other drivers.
Since OpenVPN kernel space drivers maintain session state even after you uninstall the application, they are a major cause of Windows crashing during startup. By following the methods above, you can prevent bad errors. If you are looking for a new VPN product, learn the important criteria they must meet.