Simple steps to secure your smart phone data
TipsMake.com - You may already know the basic knowledge of Internet security and keep personal data from being compromised when browsing the Web such as: Using a firewall, do not open attachments without your knowledge. Clearly, do not click on links given by strangers. But what about your smart phone? In his speech on Android phones and botnets in the framework of the security conference ShmooCon 2011, Georgia network security expert Weidman said: "Anyone interested in securing personal data is saved. store on your smartphone, think carefully before downloading unclear or unreliable applications ".
So how can botnets spread on smart phones? (Botnets are malicious software that allow an attacker to actively control your computer to connect to a particular server.) First, the victim needs to download a file containing a 'bot '- is a malicious code. This code will install a 'bot' into the phone's basic operating system. The infected files can be an application, a music file or even an email attachment. " It can be disguised in anything, " Weidman said. " Someone absolutely can offer a great application with the functions that users want. Worse, these applications can be disguised as such ads so no one will doubt it. , and so botnets can survive for years ".
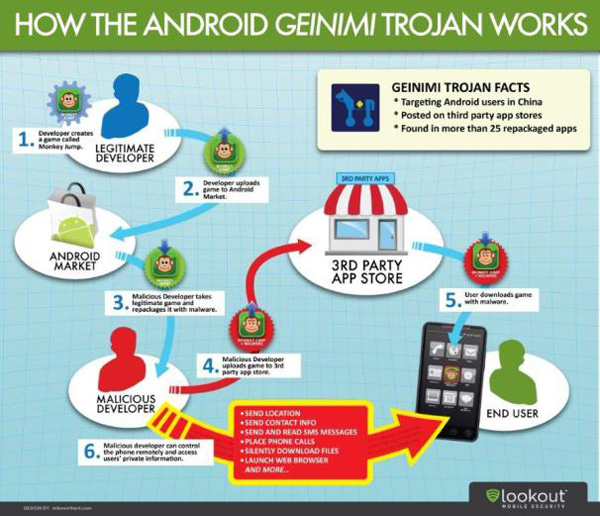
Case study: How Geinimi Botnet spreads Geinimi (based on the help of mobile security firm Lookout).
Once your phone is infected, a bot slave program will be installed in the basic operating system, hiding under the application layers that most users are familiar with. Since then these programs can monitor and modify all data sent to and from your smart phone, allowing the host bots (botmaster) to command and control your phone without your knowledge. . " Because these bots know all the information before the user knows, it can capture personal data and move it anywhere on the Internet, " Weidman said. " What you did, the people you were talking to and where you were ."
Once the botmaster has taken control of your phone, its first priority is to infect as many other users as possible. In the past, mobile botnet took advantage of Internet access of smart phones to spread malicious code via email; but the Android botnet that Weidman mentioned here is much more dangerous because it communicates and spreads via SMS. Weidman said the attack via SMS messaging service is far more efficient and sophisticated than accessing the Internet via the phone's modem. In addition, it opens up new attacks, whereby users can receive text messages from a friend whose botnet is infected with links to malicious codes.
" If I receive a text message from a friend with a link that says" this, try this link , "" why don't I trust it? "Mrs. Weidman said. " If someone in my contacts is infected with a botnet, they can cause infection to me without them knowing . 'Of course, the malware in smartphones is nothing. new, security companies such as Symantec and Lookout have provided malware detection apps for iOS and Android operating systems and remote security features like locking or scanning phones via SMS But the mobile market segmentation with many different manufacturers as well as different products often makes it difficult for security companies to keep their applications up to date with each malware. Worse, most software detects only scanning other applications to find malicious codes and cheat. They will find those applications but they can almost do nothing if these bots have overwritten a portion of the phone's operating system. Her botnet model on Android operating system, she thinks that bots can work on any smart phone. Currently, she is testing on iOS and Windows Phone 7 operating systems.
 Weidman's security studies seem to be worrisome, but this is just research. " If this type of attack becomes popular in the future, we will update the software to detect it, " said Kevin Mahaffey, technology development manager for security firm Lookout. " Unless we see malware like this in reality, we will continue to focus our efforts on current threats first ."
Weidman's security studies seem to be worrisome, but this is just research. " If this type of attack becomes popular in the future, we will update the software to detect it, " said Kevin Mahaffey, technology development manager for security firm Lookout. " Unless we see malware like this in reality, we will continue to focus our efforts on current threats first ."
In addition, a fairly simple task to protect your smartphone and avoid your data being botnet is that you just need to use security software for the iPhone and Android seriously. like on your laptop. Do not download applications or files from people you do not trust, and be wary of any links or files attached to text messages. Remember that any file you download to your phone is likely to be infected with a botnet.