Super secure SIM card, only connecting data via Tor anonymity network helps protect information for users
Many users often choose to use the Tor anonymity network on their mobile phones to hide their IP address, without disclosing information about their location. But Tor software can only be used when surfing the web, and when users use other social networking applications such as Twitter, they can still leak your IP address.
In order to help users secure information when using mobile applications, a small internet service provider in the UK is testing a SIM card for data only. This super-secure SIM card can block bandwidth without connecting Tor out of the phone. This means that, when using this SIM card, all mobile data bandwidth on the phone must go through the Tor network.
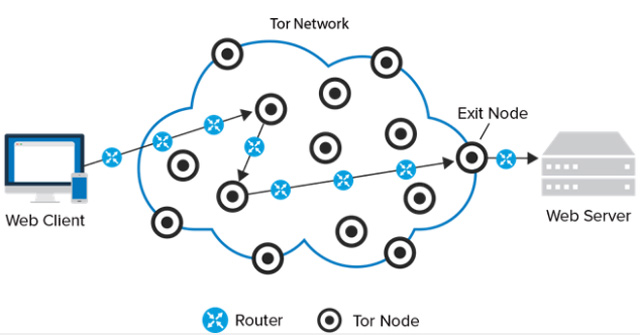
How the Tor network works.
According to Nathan Freitas, from the Guardian Project, Orbot said, a SIM card only for Tor connection is a great idea.
To use this super-secure SIM card, users need to create an access point (an access point) on their device so that the device can connect to the new network, the manufacturer will guide you to do so. this. In addition, your device must install and run Orbot.

Currently this SIM card only works in the UK. Unfortunately, it only ensures that bandwidths that do not pass Tor will not leak out when the device is using a mobile data connection, not Wi-Fi.
See more:
- How to use Tor Browser to surf anonymously
- Guide to anonymous web on Android phones
- How to protect your privacy when browsing the web on mobile?
- How to find open web pages in incognito mode