Protect the entire network with Untangle
Network Administration - We all know that protecting your computer from malicious software like viruses, trojans, spyware is actually protecting your files and data. However, with the appearance of a series of devices that can store data participating in the network, it is difficult to prevent malicious software from entering the entire network. Now applying safety protections to a wide area network is extremely necessary and will allow you to protect mobile devices as well as add a second layer of protection to his computers.
There are many ways to allow you to enforce security for such a wide area network. In this tutorial we will introduce you to the Untangle platform, which is a platform you can install on a dedicated computer or run as a virtual machine (VM). It is also set to work as a network router or firewall, in addition to giving you more interesting additional features. As shown in Figure 1, the platform's feature is a user-friendly GUI, allowing users to easily configure and manage all components.
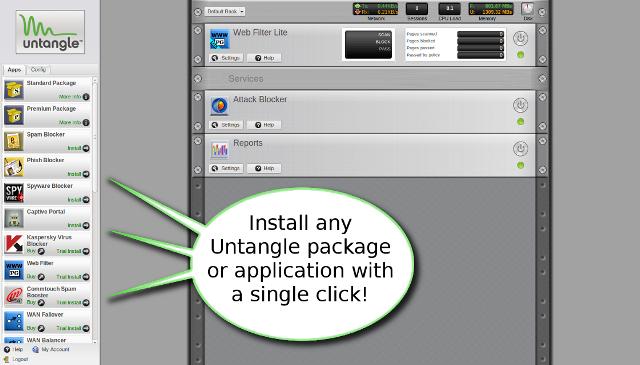
Untangle offers an open source distribution called the Lite Package (which we will cover in this article), in addition to a premium distribution starting at $ 50 per month for about 10 users.
Discover Untangle Lite
This is the most general overview of the components included in the open source version of Untangle:
Firewall: Like most preferred routers, the open source version of Untangle also allows filtering traffic based on IP address, protocol, port. In addition, it can also perform NAT, which means you can attach Untangle directly to the Internet modem.
Intrusion Prevention: Use open source intrusion detection system Snort, which helps you detect and prevent thousands of different attack attempts.
Attack Blocker: Basically a smart firewall, capable of analyzing traffic to block specific hosts that are thought to be risky. Help prevent Denial-of-Service (DoS) denial of service attacks or other attacks from the Internet.
Phish Blocker: Based on ClamAV, it allows to detect and help you manage fake emails or scams to try to trick you into logging into an online account as well as to reveal personal information.
Protocol Control: Allows you to specify the protocol or port to be logged or locked with time-based policies. It even allows you to detect and prevent applications from performing port jumping.
Virus Blocker: Using an open source virus scanner, ClamAV, allows to actively scan web (http), email (SMTP, POP & IMAP) traffic and file transfer traffic (FTP), block malware detected before they reach your computer. It even lets you scan compressed and archived files. Signs of the virus will automatically be updated with the latest known threats.
Spyware Blocker: Also use ClamAV, protect against spyware with a variety of different methods: Lock URL, cookie lock, ActiveX key, . You can temporarily allow a blocked site or include it in the Black or white list permanently. You also have additional controls on cookies and ActiveX blocking.
Web Filter: Allows you to lock by website categories, some URLs and some file types. Recording and reporting will help you check traffic, the list of clients going through will allow you to eliminate certain computers during the filtering process.
Spam Blocker: With the help of the SpamAssasin open source filter, it allows the use of some spam detection and management techniques, providing users with a list of travels and personal glasses.
Captive Portal: Allows you to ask users to view or log into a certain website before being allowed to access the Internet, which is very beneficial in ensuring that users accept certain conditions when using Wi-points Public Fi. Users can customize the web site that requires this access and many support, RADIUS, and Active Directory authentication. Time policies can restrict access and exception lists can exclude certain computers.
OpenVPN: Allows remote, secure access to your network from the Internet. It even helps you distribute client software and encryption keys.
Reports: Provides you with detailed information and reports for each user, all of which can be exported and emailed automatically.
Hardware requirements
Like other router and firewall platforms, Untangle can be preinstalled on the server or you can install the software on your computer or server yourself. When installing yourself, you need to comply with the following minimum requirements:
- 1 GHz Intel-based processor (32 or 64 bit)
- 512 MB RAM
- 20 GB hard drive
- 2 Ethernet cards (3 if you want to create a DMZ)
- Ethernet switch or wireless access point (for distributing access)
At least during the installation process, you need to have a bootable CD or DVD, monitor, keyboard and mouse. To create an installation disc, you need a blank CD or DVD and need access to a computer with a CD or DVD burner.
Warning: Untangle installation will delete all data on the hard drive.
Deployment options
There are two ways to deploy Untangle. The Router method provides NAT, which means you will attach the Untangle computer directly to the modem. The Transparent Bridge method will turn off the NAT function, which means you will connect the Untangle computer to the router plugged into the modem. It is impossible to say which method is safer or better than the other but the method requires less hardware than the Router method.
It should be noted that no matter which method you deploy, your Internet traffic must go through the Untangle computer. An Ethernet port of the Untangle computer name will play the role of Internet / WAN input. Another Ethernet port will play an output role for the local LAN. So you need to have an Ethernet switch to connect to multiple computers or wireless access points to provide Wi-Fi connectivity.
Install Untangle
Download and burn the ISO image file to a blank CD or DVD. Make sure you use either the Router method or the Transparent Bridge for the Untangle computer. Then insert the image disc into the desired computer, reboot, and then follow the installation order. When the installation is complete, your computer will be restarted. Then click Launch Client, go to Setup Wizard and select Lite Package.
If you need other help, you can consult the Wiki.
When the basic functions of the Internet and the network work, you can start configuring security features.
Timely update security software on computers
Although Untangle provides quite secure protection, it does not support malware scanners for HTTPS traffic, like other wide area network solutions. So you always need to install and update Internet security software on all desktops and laptops. However, because there are two layers of protection, you can choose to use a free antivirus software, such as AVG or AVAST. In addition, you should make the most of the firewall that comes with Windows.
 Encrypt the Windows drive with DiskCryptor
Encrypt the Windows drive with DiskCryptor Bkis is about to stop providing Bkav Home
Bkis is about to stop providing Bkav Home Opera released web page debugging tool
Opera released web page debugging tool Android security: 6 tips to help protect Google Phone
Android security: 6 tips to help protect Google Phone Protect user location information in IE 9 and Firefox 4
Protect user location information in IE 9 and Firefox 4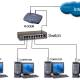 Defend against attacks inside the network environment
Defend against attacks inside the network environment