Search for malware on Windows computers with the command line
Network Administration - Hopefully the title of the article does not make you afraid. The reason we need to say this is because there are many people who want to stay away from the Windows command line utility and are more sympathetic to the complex graphical user interfaces. However when it comes to investigating malware infection, command-line tools have many benefits, while GUI-based tools don't always do this.
First, launch the command prompt.Go to Start -> Run and type 'cmd.exe' . It is very important to type '.exe' at the end of the section; This is a safe way of calling a command prompt. To deceive some users, some malicious programs may try to name 'cmd.com' and in such a case, the malware will be launched if you just type 'cmd'.
'netstat'
Next, when the command prompt appears, run the netstat command. The 'netstat -na' command can provide a list of TCP and UDP ports on the computer. Adding ' o' to the above command can know the process ID of each process using a port. Starting with XP SP2, adding ' b ' will see the EXE file name in use on each port, along with the dynamic link libraries (DLLs) that it loads to communicate with the network. However, it should be noted that adding ' b ' will consume a lot of CPU resources.
But be persistent. Suppose that you want to observe the use of a certain port and see how they change over time. Add a space and then an integer to that netstat command, this time it will be in the form " netstat -nao 1 ", the command will be run at the same frequency as the given integer, in the case This frequency is 1s. The display will continue to be displayed on the screen, as shown in the figure below.
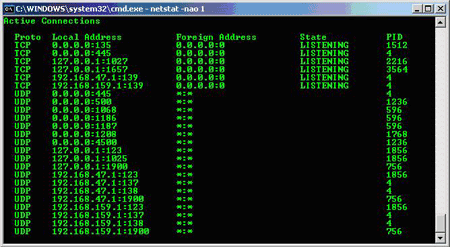
Obviously, to determine which malware is using TCP and UDP ports, you need to know the normal operation of a port. To study how ports work with computers, you can search and research ports on Google. Microsoft also has a list of ports that are generally used for both Windows clients and servers that you can refer to here. In addition, you can also search for additional ports associated with both Microsoft and third-party applications, etc.
If an abnormality occurs on TCP or UDP ports, you can perform a search on Google. Use "site:" and the following is an antivirus company like Symantec, Sophos or McAfee. These sites may have a review of malware using that port. Here is an example of this useful search query:
site: symantec.com tcp port 4444.
'reg'
A review by an antivirus vendor can help you gain more knowledge inside the registry keys that the malware may have modified. To query the registry key with the command line, use the reg command. Even if an antivirus site does not provide registry keys for search purposes, you can research the most common registry keys modified by malware: the keys related to the system's startup and the user's login. use. Known as " run " registry keys, the reg command can help display their values at the command line. However, note that many legitimate software also activate themselves using these keys. After running the command, you will see the items under these registry keys. Next, do a few searches on Google for what is shown to help you eliminate what are the valid settings and what is malware.
C:> reg query HKLMSoftwareMicrosoftWindowsCurrentVersionRun
C:> reg query HKLMSoftwareMicrosoftWindowsCurrentVersionRunonce
C:> reg query HKLMSoftwareMicrosoftWindowsCurrentVersionRunonce
We recommend that you run the commands with a relative amount of time, replacing HKLM with HKCU. The alternative will find the auto-start registry key associated with the user, instead of just the entire system settings in HKLM.
'dir'
You should also check the autostart directory to find unwanted programs starting from here. Run the dir command, use / A to display files with or without a set of attributes, as well as hidden and non-hidden files.
C:> dir / A "C: Documents and SettingsAll UsersStart MenuProgramsStartup"
'net users' and 'localgroup administrators'
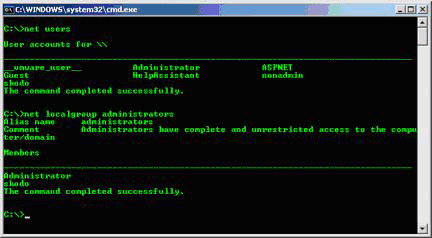
Some malware can create accounts in your local computer. In that case, we need to run the command 'net users' , which is the command to check accounts defined on the system. In addition, because some bot software can register an account of the local administrators group, then we should run " localgroup administrators ", which is a test of membership of this group. Do you know all the people in the administrator group? The following figure shows an example of this case.
'tasklist / svc'
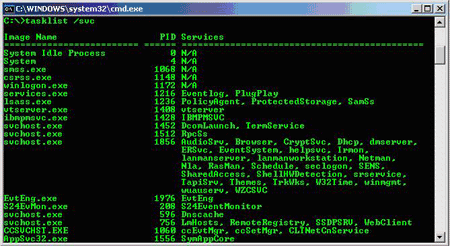
There are also more vital areas that we need to analyze: running processes. On Windows XP Professional, the tasklist command can provide a lot of useful information. This command itself displays running processes, their process ID numbers and memory usage. However, if running 'tasklist / svc' , you will see all the services that have run out of process, see below. This gives you a lot of information to look for when researching whether the system is infected by bad programs. In particular, svchost.exe processes are often quite busy, running many services. Besides spyware sometimes inserts other services into these processes or services to check or control your computer.
Some of the commands that I will show you in this article will give you a deeper understanding of the configuration of a Windows computer. But practicing a lot will make you perfect. It takes time to analyze 'clean' systems, from which you will gain knowledge of what appears on a normal Windows computer. You can then detect if a computer is infected. With some preparation and practice, command line skills will significantly improve your understanding of Windows computers and prepare you for the battle with malware that is happening every day.