Microsoft Sysmon has added a feature to block the creation of EXE files
This feature is a powerful tool for system administrators as it allows them to block the creation of executables based on various criteria such as file path, whether it matches specific hashes or brought about by certain executables.
Example : If you have a list of the hashes of a known malicious code, you can configure Sysmon to block the creation of executables that match that hash. Or if you want to prevent malicious Office attachments from spreading malicious code, you can stop creating executables from Word or Excel.
Blocking executable file creation in Sysmon
Sysmon, or System Monitor, is a free Microsoft Sysinternals tool that can monitor the system for malicious activity and log events to the Windows Event Log.
Sysmon will monitor basic events such as file creation and time changes by default to the Event viewer. However, it is possible to create a custom configuration file containing advanced options that define what Sysmon monitors or blocks.
The full list of directives in the Sysmon schema can be found by the user, which can be viewed by running the sysmon -s command in the command prompt.
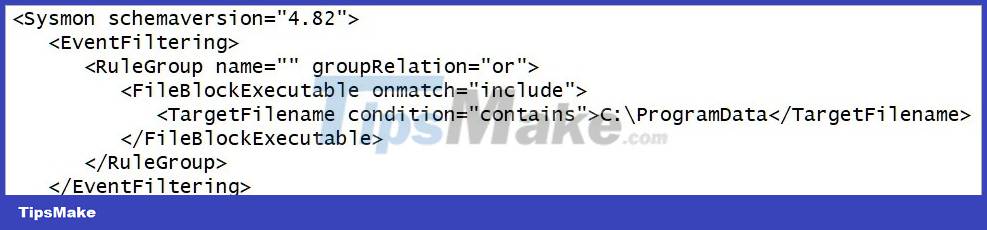
The current Sysmon Schema is version 4.82, which now includes a "FileBlockExecutable" configuration option to block the creation of executables based on their path, name, hash, and the program trying to create the file as shown below. :

Example : To prevent Microsoft Office applications from creating new executables, you can refer to the rule created by Olaf Hartong. The rule that you can see in the image below will block the creation of any executable using Excel, Word, PowerPoint, Outlook, Access or Publisher and write any event to the Event Log under the name "technique_id=T1105, technique_name=Ingress Tool Transfer."

To start Sysmon and direct it to use the configuration file above, you will need to execute the command sysmon -i followed by the configuration file name.
In the example we are following, the name of the configuration file is msoffice-fileblock.xml, so we will use the following command from the Command Prompt (Admin) to start Sysmon:
sysmon -i msoffice-fileblock.xmlAfter booting, Sysmon will install its driver and start collecting data quietly in the background.
All Sysmon events will be logged to 'Applications and Services Logs/Microsoft/Windows/Sysmon/Operational' in the Event Viewer.
With FileBlockExecutable enabled, when the executable is created and matches the rule, Sysmon will block the file and create an "Event 27, Sysmon" in the Event Viewer.
Example: Here is an experiment with this feature to block the creation of executable files in the C: ProgramData folder, which is often the target of malicious code.
Then when we try to copy C:Windowsnotepad.exe to C:ProgramData, the following event log appears when file creation is blocked.
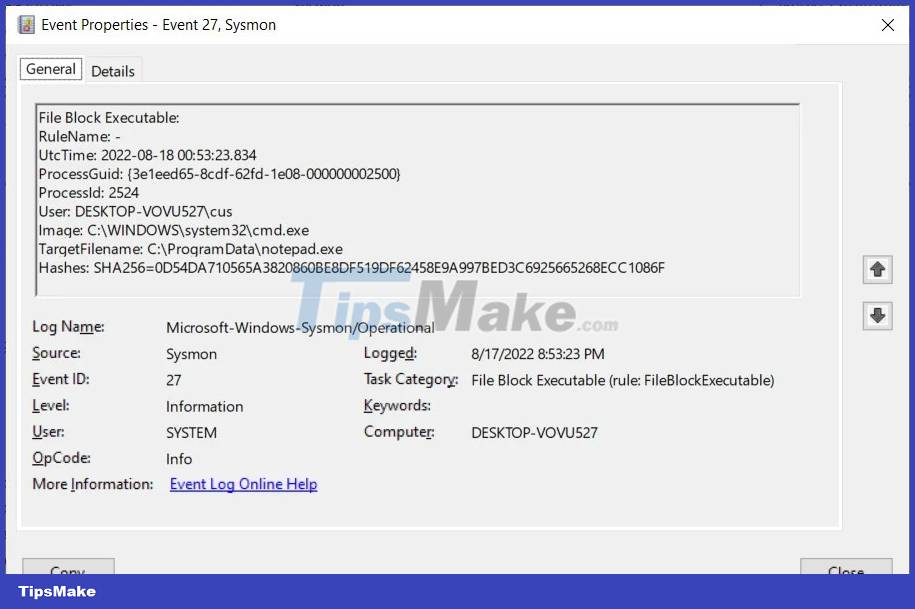
The entries in the created Event Log contain valuable information as explained below:
- ProcessID : The ID of the process trying to create the file.
- User: The user associated with the file creation.
- Image: The name of the program that created the file.
- TargetFilename: The file has been blocked from initialization.
- Hash: The SHA256 hash of the file being generated.
According to Hartong, Sysmon will determine if a file is an executable based on the file's header. Therefore, Sysmon will also block DLL and SYS executables when they use the same MZ file header.
If you want pre-made Sysmon configuration files that block known malware and hacking tools, you can download the file created by security researcher Florian Roth via the GitHub link.
There is a way to bypass the FileBlockExecutable feature
While this is a useful feature, don't consider it a 100% secure solution. After only a short time, security researcher Adam Chester found a way to bypass FileBlockExecutable.
Therefore, while it is useful to monitor and prevent malware, you should not consider FileBlockExecutable as the only protection.