McAfee releases the remainder removal tool Pinkslipbot using a PC as a proxy
Last week, McAfee released a tool called AmIPink C2, a command-line software for Windows that removes any files left after being infected with Pinkslipbot. These remnants will help malware continue to use the poisoned computers as a transit proxy, even if the binary file of the malware has been deleted and removed completely from the computer.
Pinkslipbot is a bank trojan that appeared in 2007, also known by other names like Quakbot, Qbot and PinkSlip.
Pinkslipbot - famous malware dangerous
Pinkslipbot is a dangerous malware, mainly because it pursues specific goals. It does not chase ordinary users but previously pointed towards companies in North America, especially in outstanding industries like banking, finance, insurance .
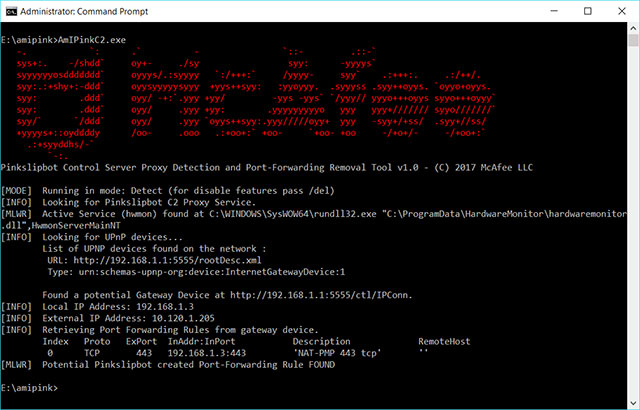
Pinkslipbot's residual remains on the computer even if you have removed the malware
This banking Trojan is not always active, it appears in installments, like part of a clearly planned campaign. In previous years, many security companies had followed the attacker and found many different versions of the malware. Most recently, the case was discovered by the security researchers at IBM that discovered the version of Pinkslipbot that closed Active Directory on the infected computer.
McAfee found Pinkslipbot's new move
One of the companies that has followed Pinkslipbot for the longest time is McAfee. Researchers here presented the Trojan's C&C server structure analysis and its C&C communication method at the Virus Bulletin security conference last year. While observing Pinkslipbot's campaigns, they found a new way of operating malware.
These researchers say Pinkslipbot's author is smarter than they think. According to McAfee, besides stealing user data, the trojan also uses the infected host as a proxy server to receive and transmit information from the central C&C server to other infected hosts in the network.
McAfee's new tool removes the remnants of Pinkslipbot
According to McAfee, most tools only help remove binary files, preventing trojans from stealing passwords from infected computers. This process of removing Pinkslipbot will not affect the code used to turn the computer into a proxy server, running through Windows UPnP (Universal Plug and Play).
McAfee's new tool will remove the remaining files and prevent Pinkslipbot from using a user's computer as a hub to transfer commands from C&C or retrieve stolen data through a proxy network. You can download AmIPink C2 here and read McAfee's user guide here.
You should read it
- Instructions on how to remove multi-platform malware on Facebook Messenger
- 5 types of malware on Android
- Remove root malware (malware) on Windows 10 computers
- Warning: 5 million Samsung, OPPO, Vivo smartphones ... are infected with malware and this is how to check and remove
- How to find and remove WMI Persistence malware from Windows PCs
- What is FormBook Malware? How to remove?
 How to use Kaspersky Free antivirus software
How to use Kaspersky Free antivirus software 4 virus fake troll friends extremely happy
4 virus fake troll friends extremely happy Lukitus Guide to preventing extortion malicious code
Lukitus Guide to preventing extortion malicious code How to delete malicious programs using Kaspersky Virus Removal Tool
How to delete malicious programs using Kaspersky Virus Removal Tool How to use the Bitdefender Adware Removal Tool to remove adware on Windows
How to use the Bitdefender Adware Removal Tool to remove adware on Windows 10 typical malware types
10 typical malware types