Lukitus Guide to preventing extortion malicious code
What is Lukitus?
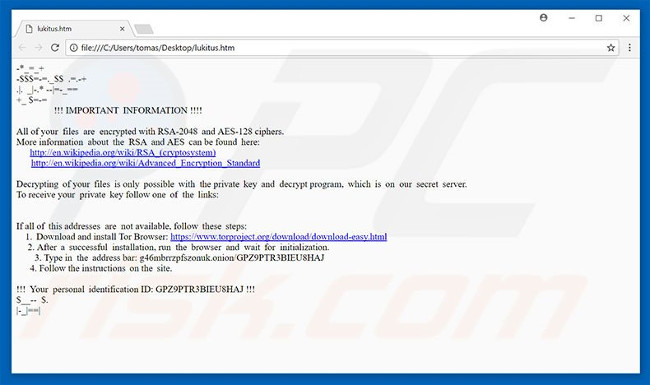
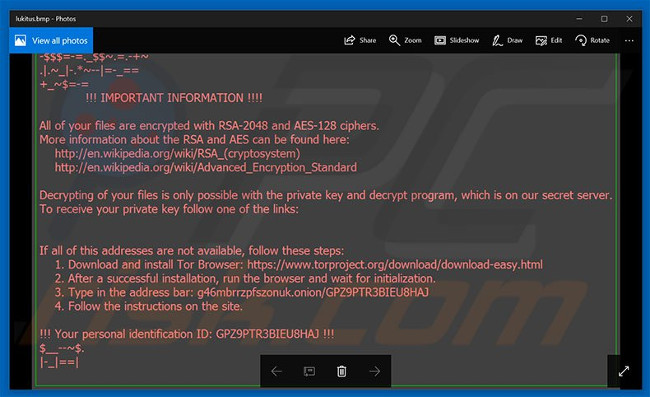
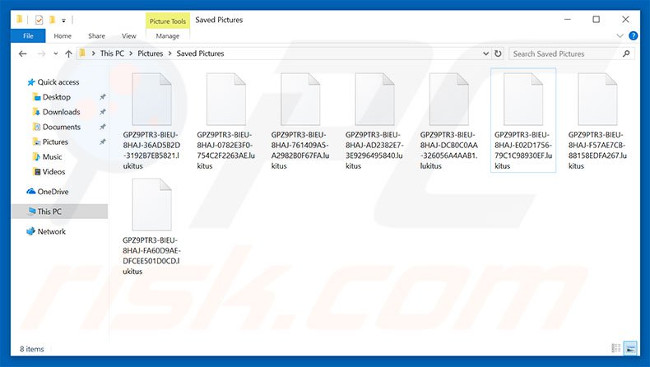
Lukitus is an updated version of a ransomware virus (extortion code) called Locky.Developers spread Lukitus via spam (malicious attachments).After penetration, Lukitus encrypts data stored with RSA-2048 and AES-128 encryption algorithms.During the encryption process, the virus will rename the encrypted files using the form "32_random_letters_and_digits] .lukitus".For example: "sample.jpg" can be renamed as file name "GPZ9AETR3-BIEU-8HAJ-36AD5B2D-3192B7EB5821.lukitus".After successfully encrypting it, Lukitus changed the desktop background and created an HTML file ("lukitus.htm") to put it on the desktop.
- How to get rid of root virus * .OSIRIS - Ransomware Locky?
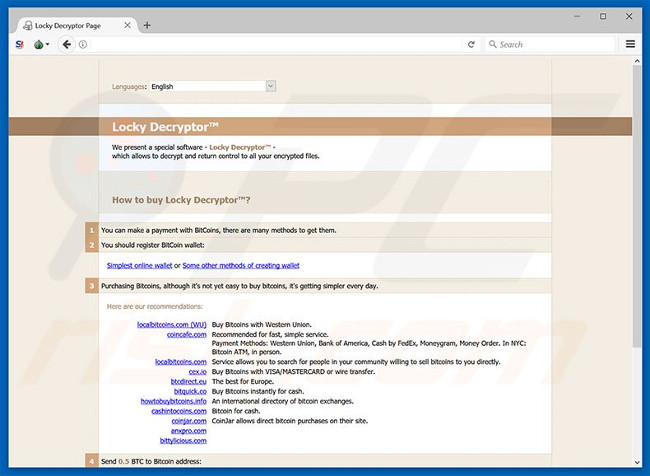
The desktop file and the HTML file on the computer contain a message about ransom requests that the file is encrypted and can only be restored through a specific decryption program using a unique key.Unfortunately, this information is correct.As mentioned above, Lukitus uses RSA and AES cryptographic algorithms, and therefore, only one decryption key is created for each victim.These keys are stored on a remote server controlled by Lukitus developers.Victims are required to pay a ransom to receive the key by following the instructions provided on the official website of the malware.The cost of decoding is 0.5 Bitcoin (approximately 50,000,000 VND).However, keep in mind that tech criminals should not be trusted because they often ignore victims when they get ransom.Payment is not guaranteed to ensure that your files will be decrypted.Moreover, giving money to cyber criminals indirectly supports their malicious virus business activities.Therefore, do not contact these people or pay any ransom.Unfortunately, there is no tool that can recover files encrypted by Lukitus and the only solution is to restore your files and systems from backup.
Notice of ransom request of cyber criminals:

Lukitus closely resembles Aleta, BTCWare, GlobeImposter and dozens of other types of extortion codes.These malware are also designed to encrypt files and request ransom.There are only two main differences: 1) the ransom required and 2) the type of encryption algorithm used.Research shows that most of these viruses use algorithms that generate unique decryption keys (eg RSA, AES, DES, etc.). Therefore, it is almost impossible to recover these files without There is a decryption key for cyber criminals.
How does extortion code attack computers?
Although Lukitus is distributed via spam, cyber criminals often distribute similar malware using fake software, trojans and third party software downloads (download sites). about free, free file hosting sites, peer-to-peer networks, etc.).In this case, Lukitus is distributed to the victim as a compressed .rar file.However, spams often contain JavaScript, MS Office documents and other similar files designed to download or install malware.The fake software update exploits outdated software errors to infect the system.Third-party software downloads often increase malicious performance by 'introducing' them as legitimate software.
How to protect your computer from extortion?
To prevent malicious blackmail infection, you need to be very careful when browsing the Internet.Never open files received from suspicious emails or download software from unofficial sources.Furthermore, use legitimate anti-spyware / anti-spyware software and update installed applications.However, keep in mind that criminals distribute malware through fake updates.Therefore, using third-party tools to update the software is very dangerous.The key to keeping computers safe is caution.
Sample spam used to distribute malware Lukitus:
Lukitus HTML file:
File Lukitus screen wallpaper:
Lukitus Tor website file:
Files are encoded by Lukitus ("[32_random_letters_and_digits] .lukitus" template file name):
Lukitus Guide to preventing extortion malicious code
Step 1: Eliminate extortion code Lukitus uses safe mode with the network.
Windows XP and Windows 7 users : Start your computer in Safe Mode. Click Start> Shut Down> OK . During the computer boot, press the F8 key on the keyboard several times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
Video tutorial on how to start Windows 7 with "Safe Mode with Networking ':
Windows 8 users: Go to the Windows 8 Start Screen, type Advanced , in the search results select Settings . Click the Advanced startup option in the "General PC Settings" window that has been opened. Click the "Restart now" button. Your computer will now reboot into the "Advanced Startup options menu" . Click the " Troubleshoot " button, then click the "Advanced options" button. In the advanced options screen, click Startup settings > Restart . The computer will reboot into the Startup Settings screen. Press F5 to start with Safe Mode with Networking.
Video tutorial to start Windows 8 in Safe Mode with Networking.
Windows 10 users: Click the Windows icon and select Power. In the opened menu, click " Restart " while holding the " Shift " button on the keyboard. In the "choose an option" window, click " Troubleshoot ", then select "Advanced options" . In the advanced options menu, select "Startup Settings" and click the " Restart " button. In the next window, click the " F5 " button on the keyboard.This will restart your operating system securely with the network.
Video tutorial to start Windows 10 in "Safe Mode with Networking":
Step 2:: Removing Lukitus extortion code to use system restore
If you cannot start the computer in Safe Mode with Networking, try performing a system restore.
Video instructions on how to remove ransomware with "Safe Mode with Command Prompt" and "System Restore:
1. During the computer boot process, press the F8 key on the keyboard several times until the Windows Advanced Options menu appears, then select Safe Mode with Command Prompt from the list and press Enter .
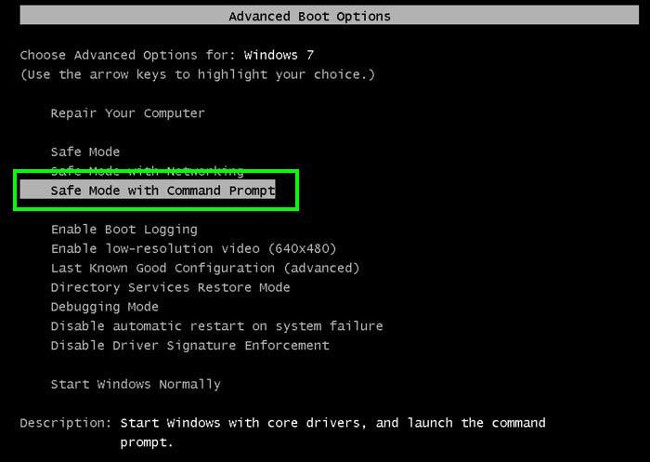
2. In Command Prompt, enter the following line: cd restore and press Enter .
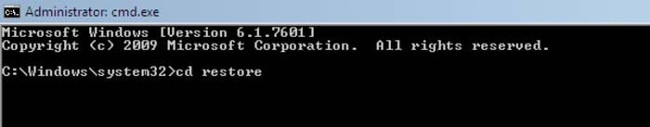
3. Next, type this line: rstrui.exe and press Enter .
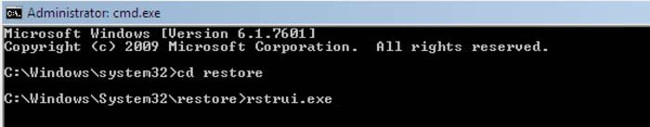
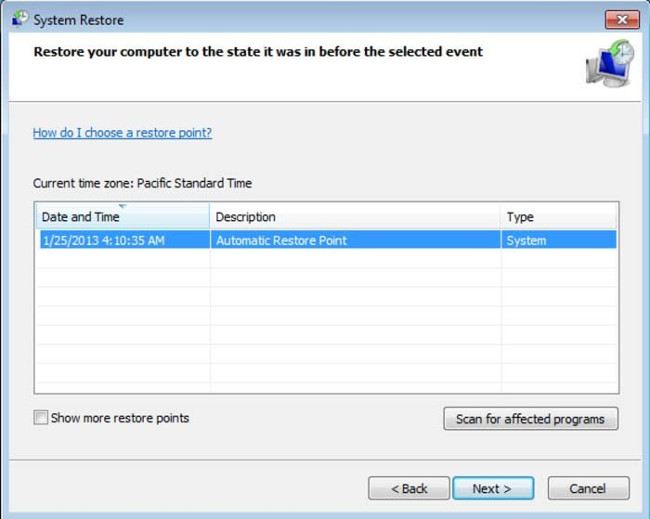
4. In the window that opens, click " Next ".
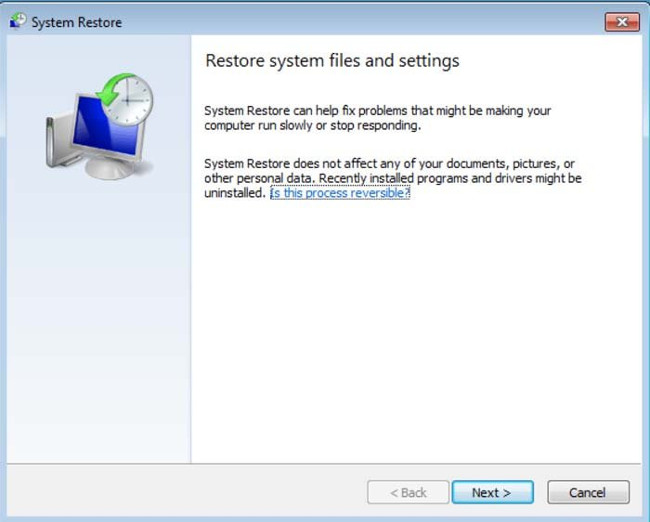
5. Select one of the Restore Points and click " Next " (will restore your computer system before the Lukitus virus invades).
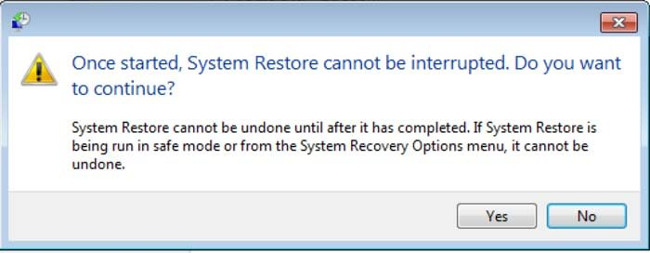
6. In the window that opens, click " Yes ".
7. After restoring the computer, download and scan your computer with malware removal software to remove any Lukitus remnant malicious code files.
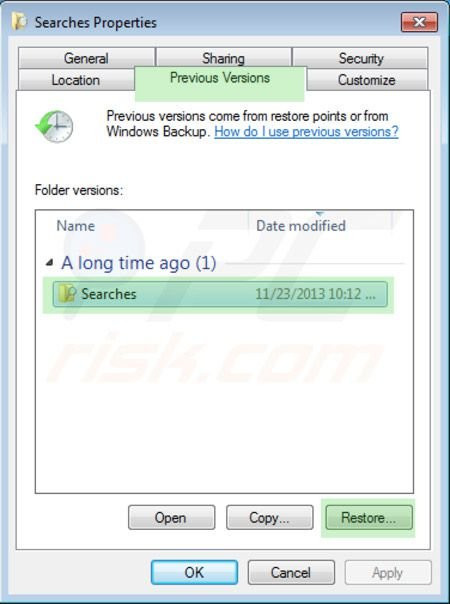
To restore these maliciously encrypted personal files, try using the Windows Previous Versions feature.This method is only effective if the System Restore function has been activated on an operating system attacked by malicious code.Note that some variants of Lukitus can delete Shadow Volume Copies of files, so this method may not work on all computers.
To restore a file, right-click it, go to Properties and select the Previous Versions tab. If the related file has Restore Point, select the file and click the " Restore " button.
If you cannot start the computer in Safe Mode with Networking (or with Command Prompt), start your computer with a rescue disk.Some variants of disabled extortion code with Safe Mode with Networking make deleting it complicated.For this step, you need access to another computer.
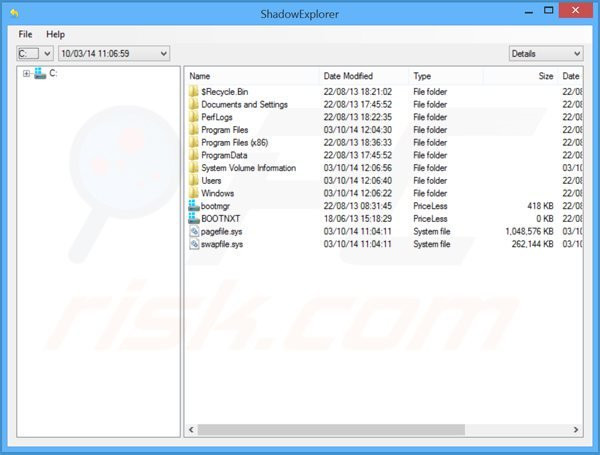
To regain control of files encrypted by Lukitus, you can also try using a program called Shadow Explorer.
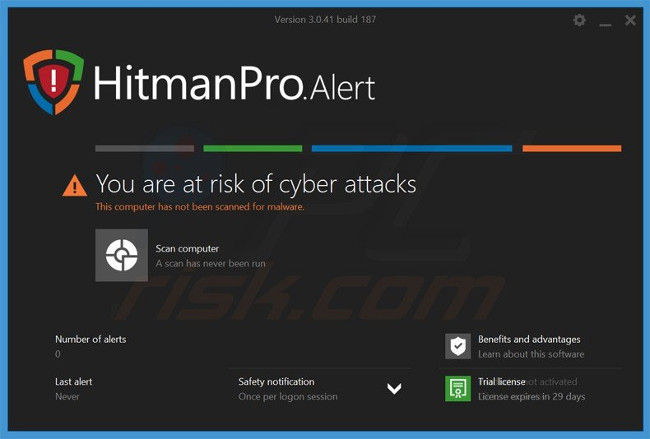
To protect your computer from file encryption extortion malicious code like this, use reputable anti-virus and anti-spyware programs.As an additional protection method, you can use programs called HitmanPro.Alert, which artificially create group policy objects in the registry to block fake programs like Lukitus.
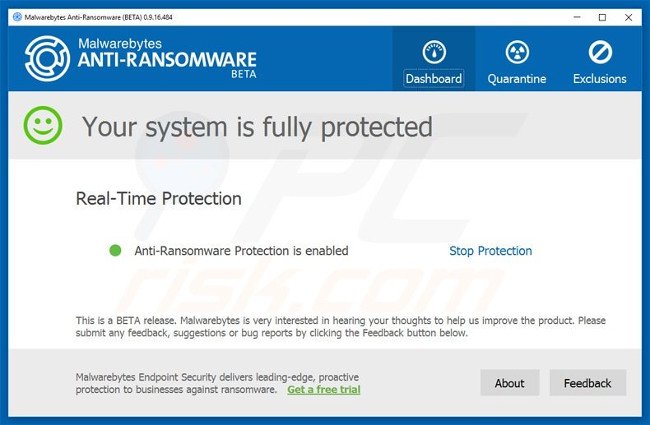
Malwarebytes Anti-Ransomware Beta uses advanced technology to monitor blackmail malicious activity and terminate it immediately - before reaching user files:
The best way to avoid damage from extortion code is to keep regular updates on backups.
Other tools are known to remove Lukitus extortion code:Plumbytes Anti-Malware andSpyHunter 4 .