Learn about firewalls (Firewall)
If anyone can access your computer at any time, your computer is vulnerable to attack. You can restrict external access to your computer and information thanks to the firewall.
How do you understand firewalls?
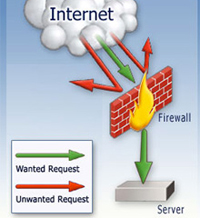
Firewalls protect you against outside attackers by blocking dangerous codes or unnecessary Internet traffic on your computer or network. Firewalls can be configured to lock data from specific locations while ensuring the necessary data can pass through. They are really important for people who often connect to the Internet.
Which firewall is the best?
Firewalls are divided into two types: hardware (external) and software (inside). In which both have their own disadvantages and advantages. The decision to choose which type of firewall to use is quite important.
-
 Hardware - Typically network firewalls, this extension device is placed between a computer or network and a cable or DSL modem. Many vendors and Internet service providers (ISPs) offer 'router' devices that also include firewall features. Hardware firewalls are used effectively to protect multiple computers and still have a high level of security for a single computer. If you only have one computer behind the firewall, or if you are sure that all other computers on the network are updated with free patches of viruses, worms and other malicious codes, you do not need to expand. the protection of a firewall software. Hardware firewalls have the advantage of separating devices running on their own operating systems, so they provide protection against attacks. However, the big drawback to them is cost, though many products also cost less than $ 100 (even lower than $ 50).
Hardware - Typically network firewalls, this extension device is placed between a computer or network and a cable or DSL modem. Many vendors and Internet service providers (ISPs) offer 'router' devices that also include firewall features. Hardware firewalls are used effectively to protect multiple computers and still have a high level of security for a single computer. If you only have one computer behind the firewall, or if you are sure that all other computers on the network are updated with free patches of viruses, worms and other malicious codes, you do not need to expand. the protection of a firewall software. Hardware firewalls have the advantage of separating devices running on their own operating systems, so they provide protection against attacks. However, the big drawback to them is cost, though many products also cost less than $ 100 (even lower than $ 50). - Software - Some operating systems have built-in firewalls, if your operating system is not available, it is also easy to get from some computer stores or software vendors or Internet service providers. Because there are many risks in downloading software from the Internet to an unprotected computer, it is best to install a firewall from a CD, DVD or floppy disk.
You know how to set up the configuration?
Most commercial firewall products, both hardware and software, are configured to ensure acceptance from most users. For each different firewall you need to read and understand the accompanying documentation to determine if the default settings on this firewall are guaranteed to meet your needs. In addition, you must pay attention to warnings about the current virus and worm because sometimes it includes information about the limitations that can be enforced through the firewall.
When properly configured firewalls it can withstand some attacks, but you should not be subject to some security flaws. Firewalls can give the computer a fairly solid protection but are not completely guaranteed to be attacked. Specifically, a firewall with uncertain protection does not prevent malicious programs from running on the computer. However, using a common firewall with security checks (such as anti-virus software and safe computer operations) will help the computer to resist all attacks.