Internet routing: More complex than you think
Network Administration - In this article we will give an in-depth analysis of Internet routing .
Since the Internet was born decades ago, there was a need for routing traffic from one computer to another and from one network to another. As the Internet grows, this routing problem is becoming more and more complicated. Today there are many protocols for routing traffic, such as the Border Gateway Protocol and Open Shortest Path First. Border Gateway Protocol is the protocol that most Internet users do not work directly with, but this hybrid protocol is necessary for Internet operation and is an important part of redundancy. In this article, we will use the Border Gateway Protocol to convey complex issues that most people don't know, or at least don't think about.
Platform of Border Gateway Protocol (BGP )
The Internet is made up of thousands of different networks. These networks are grouped together in neighborhoods called Autonomous Systems (ASes), each of which has tens of thousands of connected computers. When a computer in an autonomous network needs to send data packets to a computer within another autonomous system, this packet needs to find its way through other autonomous regions to reach the desired autonomous region. The process of packets transmitted through these autonomous regions is called routing. The protocol for implementing this routing is called the Border Gateway Protocol (BGP), see Figure 1 below to see the basics of routing between two logical autonomous regions. This Border Gateway Protocol (BGP) protocol is different from other routing protocols, such as Open Shortest Path First (OSPF), which is used for medium or large sized corporate networks. However, this OSPF protocol cannot respond to wide area networks like BGP. BGP is not restricted in routing packets between autonomous systems and can be useful for very large enterprise networks.
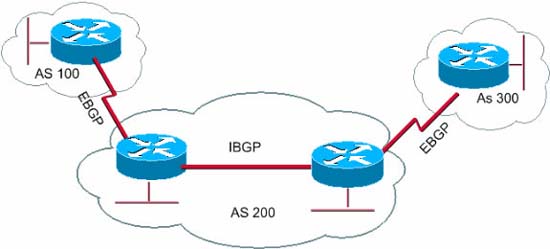
Figure 1: BGP routing between autonomous systems (AS)
BGP is often referred to as an External BGP (EBGP) when used to route packets between AS and Internal BGP (IBGP) when used inside an AS. As we mentioned, IBGP is very useful for very large enterprise networks. One reason network administrators choose to implement IBGP on their network is to take advantage of BGP's multi-home mechanism, which can improve redundancy for networks with multiple access points.
Performance issues
When large networks implement BGP, they all have to connect to each other in a full-mesh fashion, which is the type of network where each router needs to communicate with other routers in both directions. This may weigh down on the router's memory requirements. It is not necessary that it also contributes to increased network traffic. However, we have techniques that can overcome some of the problems encountered when extending the system.
One problem that the Internet had to solve a few years ago was the exponential growth of routing tables. This problem has been solved (but still quite large) with the appearance of Classless Inter-Domain Routing (CIDR). The larger the routing table, the more time it will take during the upgrade process and ultimately affect network performance. This problem also contributes to reducing CPU performance and also leads to slow routing time.
One technique that a network designer can use is called alliances. For alliances, a large enterprise network can be broken down into multiple logical ASs, each with a full-mesh connection, then routed between ASs. Basically, an enterprise network will be like a miniature Internet.
A network implementing IBGP can also implement the Router Reflecting (RR) design. In this design, a router will act as a central point as a router reflection server and other routers become reflective clients. This way significantly reduces the number of sessions each router needs to maintain and can significantly increase router performance. However, this design can lead to a reduction in routing optimization. Indeed there must always be a bid here that you have to choose to be reasonable.
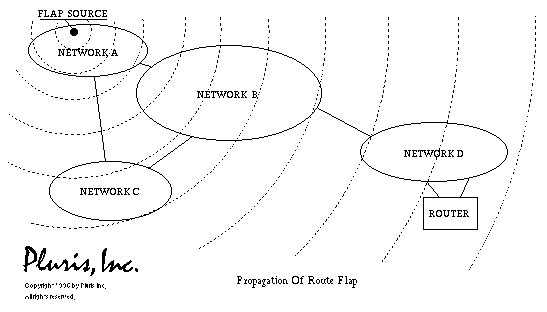
Another performance issue that network designers need to consider is route flapping. Figure 2 below shows an example of route flapping. Within any large network, all BGP routing tables must be upgraded regularly because the links can crash at any time. However, for specific routers, this type of action will not be performed regularly. Sometimes routers may be misconfigured; and this often results in repeated and repeated cycles. It will then lead to redundant action with all of the routers on that peer. When a router is online, whether for the first time or after a short downtime, a re-declaration is required for other peer routers. This can lead to an effect on CPU performance in a short amount of time (several seconds). This action is called route flapping. To overcome the route flapping phenomenon, we need to have many BGP implementations to reduce the route flapping phenomenon (route flap damping).
Route flap damping is a process that attempts to limit the negative effects of route flapping. When using this technique, the system will ignore repetitive statements (when a router works again) for longer periods of time. Previously, route flap damping was seen as an effective method for reducing route flapping. But there are many problems that hinder the optimization of network performance. Many network experts still argue about route flap damping. To be safe, if you are a network administrator, it is best to manage your router effectively from the beginning!
Architecture of routers
What makes these routers perform better to connect without route flap damping techniques? There are many obvious reasons here. First, router CPUs are getting more and more efficient like desktop CPUs. Second, the bus speed is also significantly improved. Another major change that has contributed to increased router performance has been the architectural changes that have taken place over the past few years. In particular, changes occurring in the routing table are upgraded by router processors on interface cards. Interface card processors also manage routing. The CPU manages the operating system and many other management tasks are performed by the administrator. This decentralization has significantly improved the overall performance for network routing performance.
As you can see, there are many factors that affect routing problems for large networks. These are the first suggestive thoughts about the protocol design phase, followed by the router design phase (hardware, software design and even router's overall architecture), and even far away. moreover, the network design phase, where designers and administrators use the tools available to them in the protocol and on the routers themselves to optimize routing for their networks. Please follow the following sections of this series.