How to set up IKEv2 IPsec on Windows
Prepare
First of all, you will need to download Surfshark's IKEv2 certificate here.

After downloading the certificate, open it and a prompt window will appear.
 A prompt window will appear
A prompt window will appear
Then, select the installation in the local machine (this option requires admin rights), then select Trusted Root Certification Authorities to install it.
 Select Trusted Root Certification Authorities
Select Trusted Root Certification Authorities
Click Next> Finish to complete the installation.
Establish a VPN connection
1. Open the Windows Start menu, type control panel and open the Control Panel application.
2. Click the Network and Internet category .
3. Then select the tab Network and Sharing Center .
4. Click the Set up a new connection or network option .
5. Select the Connect to a workplace option and click Next.
6. Select the Use my Internet connection (VPN) method .
7. Enter the following information:
- Internet address: Enter the domain name of the server you want to connect to.
- Destination name: You can name this connection the way you want.
- Use a smart card: Unchecked .
- Remember my credentials : You may not check this option if you want to enter your login information every time you connect.
- Allow other people to use this connection : If you do not check it, only the user for whom you are establishing this connection can connect. (If you want all users to be able to connect, you need admin privileges.)
After filling in all the fields, click Create.
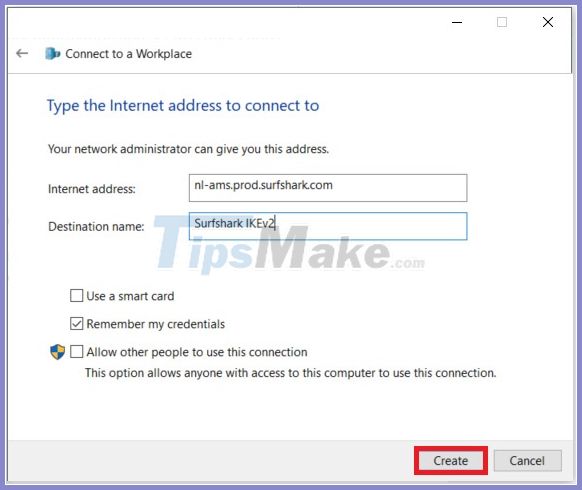 Enter the required information
Enter the required information
8. Click Create and right-click on the adapter you have created. Select Properties and open the Security tab .
Set up the following options:
- Type of VPN: IKEv2
- Data encryption: Require encryption (disconnect if server declines)
- Authentication: Use Extensible Authentication Protocol (EAP) and EAP-MSCHAPv2
Then, click OK to save these changes.
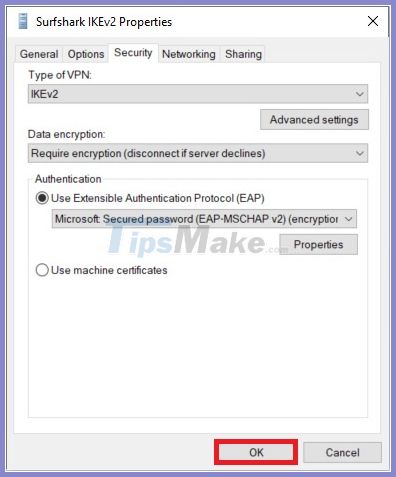 Set up options
Set up options
9. Open the Network settings (in the bottom right corner of the screen, tap the Network icon ) and select Network & Internet settings .
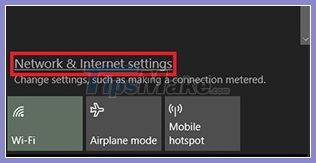 Select Network & Internet settings
Select Network & Internet settings
10. In the newly opened window, select VPN , click the newly created connection and select Advanced options.
11. In the Advanced options settings , click Edit and fill in your service credentials. Then, click Save to confirm the changes.
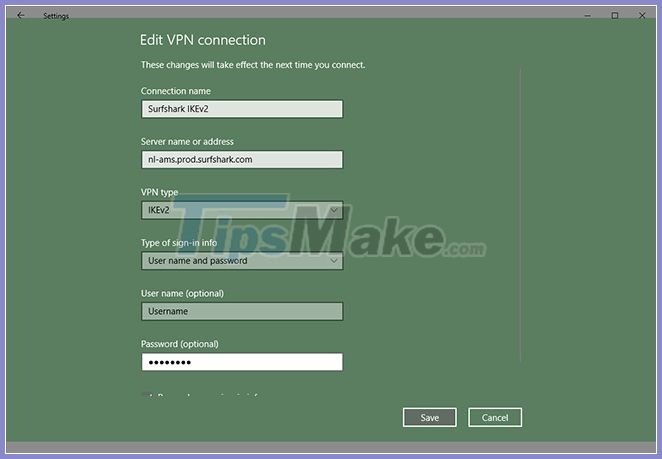 Enter service credentials
Enter service credentials
12. Now, open the Network settings again , tap on the newly created connection and click Connect.