Deploy IPSec / VPN system on Windows Server 2003
The need for remote access (outside the office) of intranet to exchange data or use applications is increasingly popular. This is a practical need, but due to security and information security, companies are afraid to "open" their internal network to allow remote access. This article covers solutions for remote access VPN on Windows Server 2003 with IPSec-based encryption mechanism to ensure information security.
VPN
VPN ( virtual private network ) is a technology to build a virtual private network to meet the needs of information sharing, remote access and cost savings. Previously, for remote access to the network, people often used the dial-up Remote Access method based on the telephone network. This method is both expensive and unsafe. VPNs allow computers to communicate with each other through a shared environment like the Internet but still ensure data privacy and security.
In order to provide connectivity between computers, information packets are wrapped with a header containing routing information, allowing data to be sent from the machine through the shared network environment and to the receiving machine. Such as transmitting on separate pipes is called tunnel. To ensure privacy and security on this shared environment, packets are encrypted and can only be decrypted with the appropriate keys, preventing "theft" of packets on the medium.
Common situations of VPN:
 - Remote Access: Meet the needs of data access and applications for remote users, outside the company through the Internet. For example, when users want to access databases or server files, send and receive email from the company's internal mail servers.
- Remote Access: Meet the needs of data access and applications for remote users, outside the company through the Internet. For example, when users want to access databases or server files, send and receive email from the company's internal mail servers.
- Site To Site: Apply to organizations with many branch offices, between offices need to exchange data with each other. For example, a multinational company that needs to share information between branches in Singapore and Vietnam, can build a Site-to-Site VPN system connecting two Vietnam and Singapore sites to create a road. Private transmission on the Internet for safe and effective communication process.
 - Intranet / Internal VPN: In some organizations, the data transmission process between some parts needs to ensure privacy, not allowing other departments to access. The Intranet VPN system can meet this situation.
- Intranet / Internal VPN: In some organizations, the data transmission process between some parts needs to ensure privacy, not allowing other departments to access. The Intranet VPN system can meet this situation.
To deploy a VPN system we need the following basic components:
- User Authentication: provides user authentication mechanism, only allows valid users to connect and access the VPN system.
- Address Management: provides a valid IP address for users after joining the VPN system to access resources on the local network.
 - Data Encryption: provides a solution to encrypt data during transmission to ensure privacy and data integrity.
- Data Encryption: provides a solution to encrypt data during transmission to ensure privacy and data integrity.
- Key Management: provides solutions to manage keys used for data encryption and decoding.
IPSEC (IP SECURITY PROTOCOL)
As we know, for computers on LAN / WAN or Internet systems to communicate with each other, they must use the same protocol (like the communication language in the human world) and the popular protocol currently now TCP / IP.
 When transmitting packets, we need to apply encryption and authentication mechanisms for security. There are many solutions to accomplish this, in which IPSEC encryption mechanism operates on TCP / IP protocol proved effective and cost-effective during the deployment process.
When transmitting packets, we need to apply encryption and authentication mechanisms for security. There are many solutions to accomplish this, in which IPSEC encryption mechanism operates on TCP / IP protocol proved effective and cost-effective during the deployment process.
During authentication or data encryption, IPSEC can use one or both of the following security protocols:
- AH (Authentication Header): packet header is encrypted and protected against "ip spoofing" or "man in the midle attack" cases, but in this case the main information content is not covered. guard
- ESP (Encapsulating Security Payload): The content of the information is encrypted, preventing hackers from placing eavesdropping programs and blocking data during transmission. This method is very useful, but if you want to protect the header of the packet, you must combine both protocols AH and ESP.
IPSec / VPN on Windows Server 2003
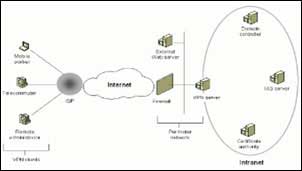
We refer to the real situation of Green Lizard Books, a company specializing in publishing and distributing cultural products. In order to promote business efficiency, the management department wants business staff in the process of working outside to access the sales report (Sale Reports) shared on File Server and can interact with the machine. Count their in the office when needed. In addition, for confidential, sensitive data such as sales reports, strict encryption mechanisms can be applied to improve data security.
Green Lizard Books needs an ADSL connection with a static IP address for connection and communication between inside and outside the company. Remote users (VPN Client) will connect to the VPN Server to join the company's virtual private network system and be allocated the appropriate IP address to connect to the company's internal resources.
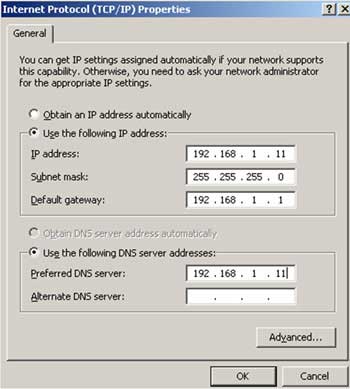
We will use 1 Windows Server 2003 machine as VPN Sever (named SRV-1), have 1 network card connected to the local network (IP: 192.168.1.1) and an ADSL card (static IP, if used Dynamic IP must be used in conjunction with Dynamic DNS services such as DtnDNS.Org or No-IP.Com) to connect to the outside (Internet).
To manage users on systems and resources we need to have a domain controller installed on Windows Server 2003 named SRV-11 (IP: 192.168.0.11).
In this model, we use an external client machine running Windows XP operating system, VPN connection with IPSec ESP-based authentication and data encryption mechanism.
Here I only present the main steps in the deployment process, details of installation and configuration you can refer to video files (.avi) downloaded at the website www.pcworld.com.vn .
Step 1: Create the controler domain
( dcpromo-srv-11-greenlizardbooks-domain-controller.avi )
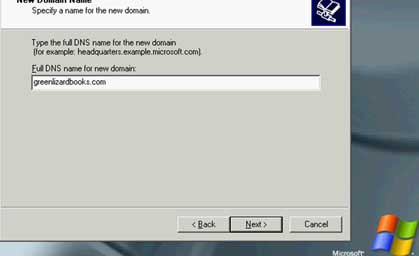
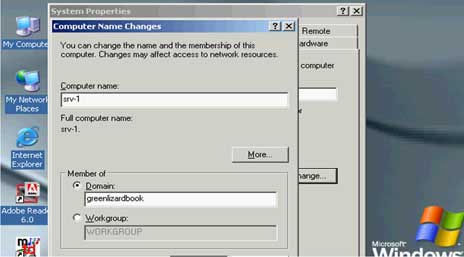
Step 2: Insert the SRV-1 (VPN Server) into the domain
( join_srv-1_server_to_domain.avi )
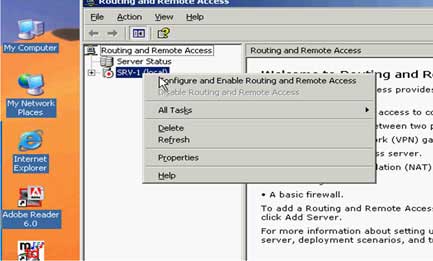
Step 3: Install VPN Server on SRV-1
( install_vpn_server_on_srv-1.avi )
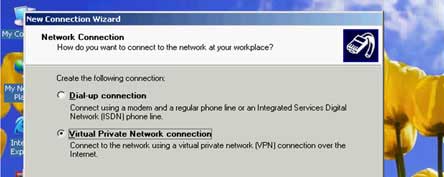
Step 4: Set up a VPN Client Client-1 to connect to the VPN Server
( create_vpn_client_1_and_connect_to_srv-1_vpn_server.avi )
Step 5: Connect the VPN Client Client-1 to the domain
( join-vpn-client-1-to-greenlizardbooks_domain.avi )
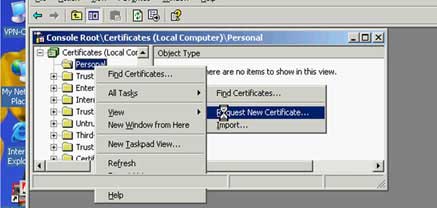
Step 6: Request for issuing electronic certificate (certificate) for VPN Server and Client for authentication and encryption.
( request_certificate_for_vpn_server_and_client.avi )
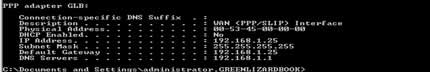
Step 7: Set up a VPN connection using L2TP / IPSEC protocol
( establish_L2TP_VPN_connection.avi )

CONCLUDE
VPN is the most commonly used technology to provide a safe and effective connection to access internal corporate resources from outside the Internet. Although we use shared network infrastructure, we still guarantee the privacy of data as if it were communicating on a private network. The "soft" VPN solution introduced in this article is suitable for a small number of users, in order to meet a larger number of users, a hardware VPN solution may be required.
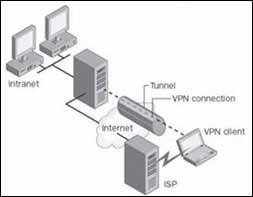
TUNNELING
Tunneling is a technique that uses an intermediate network (usually the Internet) to transfer data from this computer network to another computer network but still maintain privacy and data integrity. Data transmitted after being split into frames or packets (packets) according to the communication protocols will be wrapped with a header layer containing routing information to enable packets to be transmitted through intermediate network systems according to separate roads (tunnel). When the packet is transmitted to the destination, they are separated from the header layer and transferred to the final workstation that needs to receive data. In order to establish tunnel connection, the client and server machines must use the same tunnel protocol.
- PPTP ( Point-to-Point Tunneling Protocol ): PPTP can be used for Remote Access or Site-to-Site VPN. The advantage of using PPTP for VPN is that it does not require a certificate for authentication and the client can put behind the NAT Router.
- L2TP ( Layer 2 Tunneling Protocol ): L2TP is a combination of PPTP and Layer 2 Forwading (L2F, the protocol developed by Cisco System). Compared to PPTP, L2TP has more powerful and safe features.
On Microsoft systems, L2TP is combined with IPSec Encapsulating Security Payload (ESP) for data encryption, called L2TP / IPSec. This combination not only allows authentication for PPTP users, but also allows authentication for computers through certificates, improving the security of data transmission, and tunneling can takes place on many different network systems. However, in the L2TP / IPSec environment the VPN Client cannot be placed behind the NAT Router. In this case we need to have a VPN Server and VPN Client that supports IPSec NAT-T.
Nguyen Tran Tuong Vinh
MCSA / MCSE Security, Comptia SECURITY +, SCNP
Leader@Security365.Org
Director - SECURE SOLUTION