Configure IPSec Policy through GPO
In this article we will show you how to configure IPSec Policy via GPO.
Windows 2000 / XP / 2003 computers have a built-in IP security mechanism called IPSec (IP security). IPSec is a protocol designed to protect TCP / IP data packets when they are transmitted in the network using public key encryption. In addition to the above feature, besides encryption, IPSec also allows you to protect and configure workstations and servers with a firewall-like mechanism.
When working on a computer, you can easily set and assign IPSec Policy (IPSec Policy) from the Command Prompt using the NETSH command, or from the MMC console loaded with IP Security snap-in. .
However, when working with multiple computers, you need a better solution than having to go to each machine and reconfigure IPSec Policy. We need a method where we can use the same IPSec Policy on multiple computers or at least establish the same policy on some computers.
One method of configuring multiple computers to use the same IPSec Policy is to perform Export and Import IPSec Policy. However in this article we will use the second method - using the Active Directory Group Policy Object (or abbreviated as GPO) .
Note : Some features of IPSec enforcement for Windows Server 2003 families are not provided in Windows 2000 or in Windows XP. To ensure the same IPSec policy functions on computers that are running Windows Server 2003 and Windows 2000 or Windows XP, you need to test the policies thoroughly on all related operating systems before deploying. declaration. If you plan to apply IPSec policies that use new features only available in Windows Server 2003 IPSec, you must not use Windows 2000 or Windows XP versions for IP Security Policy Management to manage policies. The settings in the previous versions of IP Security Policy Management will override the settings in their IPSec policy Windows Server 2003 and the new features will not work.
Assume that you want to block PING traffic for certain computers. In order for this tip to work, you need to have the following:
- An existing Active Directory infrastructure (working without errors).
- All computers that need to be configured must be using Windows 2000 or higher versions.
- One OU, save machine accounts. If there is no appropriate OU for the situation, you need to configure the GPO on the Domain level, and thus affect all domain members. That's why we suggest creating an OU and putting computer accounts into it.
Next we need to configure IPSec Policies within the GPO. We can do this by editing the GPO, manually configuring the IPSec Policy, just like you did in the article locking Ping traffic with IPSec. The only difference is that you are editing IPSec policies as part of a larger GPO, not just an internal computer.
If all of the above are OK, you can now start configuring the GPO.
- Open Active Directory Users & Computers . Right-click the domain (or OU if you only want to configure certain computers). Select Properties .

- In the Properties window, click the Group Policy tab. Click New to configure the new GPO (if not already). Name the description, such as Secure Services .
Note : If you are configuring a Windows Server 2003 DC computer that has GPMC installed, you can shorten this action by opening the Group Policy Management snap-in from Administrative Tools and selecting the desired GPO.
- Click Edit to edit the GPO.
Navigate to Computer Settings> Windows Settings> Security Settings> IP Security Policies on Active Directory . You can now configure IPSec Policy. See the tutorial for locking Ping traffic with IPSec for examples.
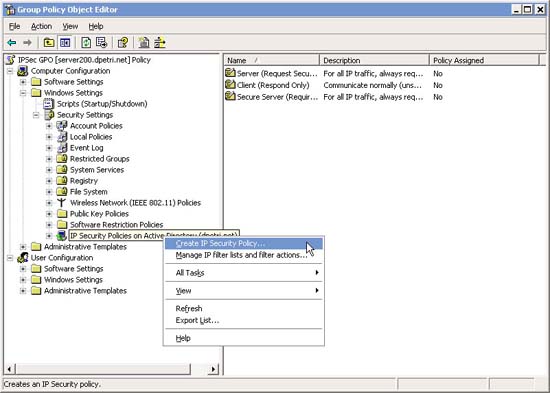
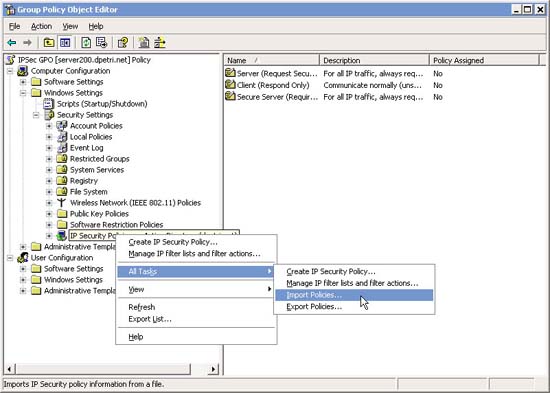
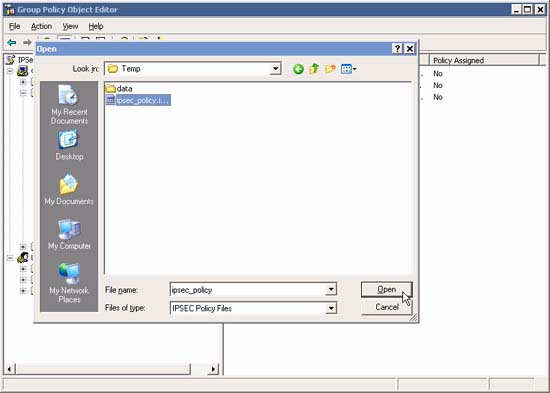
Or if configured, import it as a .IPSEC file.
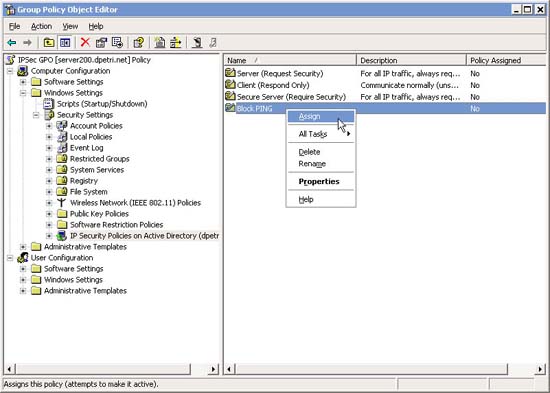
- After the IPSec Policy is properly customized, right-click it and select Assign .
- For the changes to take effect, restart the client or refresh the computer policy. Run the following command:
secedit / refreshpolicy machine_policy / enforce
In Windows XP and Windows Server 2003, type
gpupdate / force
When assigning an IPSec policy in Active Directory, you need to know the following:
- A list of all IPSec policies can be assigned at any level in the Active Directory architecture. However, only one IPSec policy is assigned to a specific level in Active Directory.
- An IPSec policy assigned to an OU in Active Directory will take precedence over domain-level policies applicable to members of that OU.
- An IPSec policy assigned to a lowest-level OU in the domain hierarchy will override the IPSec policy assigned to the higher-level OU, with the member computers of that OU.
- An OU will inherit its parent OU policy unless this inheritance is locked or the policy is assigned.
- IPSec policies from other OUs are never affected.
- The highest possible level in the Active Directory hierarchical architecture should be used to assign policies to reduce the number of configuration and administration required.
- An IPSec policy can be actively maintained even after the GPO it is assigned is deleted. For this reason, you should unassign the IPSec policy before deleting the policy object. To avoid this situation, use the procedure below:
- Cancel assigning IPSec policy in GPO
- Wait 24 hours to make sure your changes are popular.
- Delete the Group Policy object.
If you delete the Group Policy Object without following the above procedure, the computers in the Active Directory section will work with the IPSec policy as if found and continue to use a saved copy.
Before assigning an IPSec policy to a GPO, it is necessary to verify the Group Policy settings required for the IPSec policy. For example, if an IPSec policy requires certificate authentication, assign Group Policy settings to allow computers to enroll certificates (use a day or two before assigning the IPSec policy to the request to use a computer certificate). In addition, you need to test the certificate enrollment process and identify the errors before assigning the IPSec policy.