What is SSTP (Secure Socket Tunneling Protocol)?
SSTP is difficult to block and only provides good speeds if you have enough bandwidth.
What is SSTP (Secure Socket Tunneling Protocol)?
Short for Secure Socket Tunneling Protocol, SSTP is a type of VPN tunnel that uses SSL 3.0 channel to send PPP or L2TP traffic. SSL allows for the transmission and encryption of data, as well as checks the integrity of the traffic. Therefore, SSTP can bypass most firewalls and proxy servers by using the SSL channel over TCP port 443.
SSTP is available for use in Windows environments (since Windows Vista SP1), in RouterOS, and in SEIL (since firmware version 3.50). SSTP can be used with Winlogon or smart card authentication, remote access policies, and Windows VPN client, as it is integrated with the RRAS architecture.
As with other IP-over-TCP tunneling protocols, SSTP works well only if there is enough bandwidth on the un-tunneled network link. If there is not enough bandwidth, the TCP timer (the tool used by TCP to avoid excessive delays in communication) will probably expire, causing a large drop in SSTP performance.
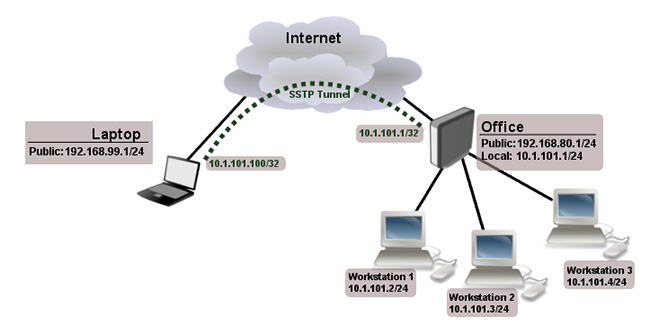
The client system connects to the server through TCP (Transmission Control Port). SSL uses port 443 to connect to the server. To confirm the connection, it requires user authentication and is usually authenticated by the client. Protocol that uses a server certificate for authentication.
Why is SSTP such a popular VPN protocol?
There are many really popular endorsement reasons for SSTP. For example, SSTP offers the highest level of security i.e. 256-bit AES encryption. Furthermore, the port it uses can evade most types of firewalls. Since SSTP is a property owned by Microsoft, it is fully compatible with Windows.

Advantages and disadvantages of SSTP
Advantages
- Capable of bypassing most types of firewalls.
- The security level depends on the cipher, but it is usually secure.
- Supported by Microsoft & integrated into Windows operating system.
Defect
- Since this is the property of Microsoft, no third party can test for the security vulnerability.
Slow speed due to high encryption level.