What do you need to know about VPN technology
How they work, what they can do for you and issues that need attention.
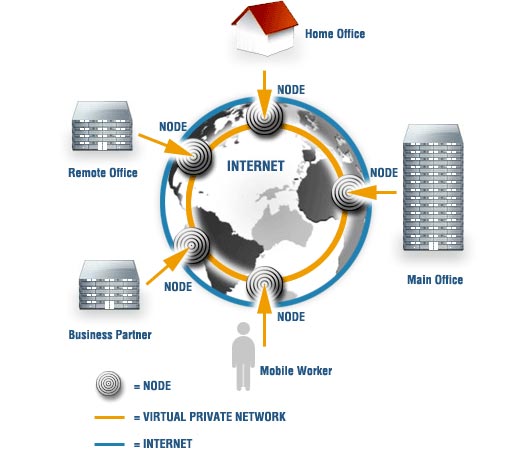
Virtual Private Network (VPN) - Virtual private networks extend the scope of Local Area Networks without any separate lines. Merchants can use VPNs to provide network access to mobile and remote users, connect geographically dispersed branches into a single network and allow remote use of applications. Use based on services in the company.
VPNs can use one or both techniques: use the service provider's own subscriber channels (this is called a Trusted VPN ) or send encrypted data to the Internet (this is called is Secure VPN ). Using a Secure VPN over a Trusted VPN is called Hybrid VPN . Combining both types of Secure VPN in one gateway, such as IPsec and SSL is also called Hybrid VPN .
Trusted VPN
Over the years, Trusted VPNs have changed from private subscribers from telecom agents to private IP subscribers from Internet service providers. The main technology of running Trusted VPN with IP address network is ATM channels, frame relay circuits, and MPLS.
ATM and frame relay works at the data link layer, which is the second layer in the OSI model (the first floor is the physical layer, the third layer is the network layer). MPLS simulates some properties of switching networks and packet switching networks. It operates on the same floor, often referred to as the '2.5' floor because it is located between the link layer and the network layer. MPLS starts replacing ATM and frame relay to enforce Trusted VPNs with a large number of businesses and service providers.
Secure VPN
Secure VPN can use IPsec in encryption. IPsec is in the L2TP protocol ( Layer 2 Tunneling Protocol ), in the SSL ( Secure Sockets Layer ) 3.0 component in TLS ( Transport Layer Security ) with encryption, L2F ( Layer Two Forwarding ) or PPTP ( Point-to-Point) Tunneling Protocol ). Let's take a look at these key components.
IPsec or IP security - is the standard for encryption as well as for IP packet authentication at the network layer. IPsec has a set of cryptographic protocols with two purposes: secure network packets and change encryption keys. Some security experts, such as Bruce Schneier of Counterpane Internet Security, have viewed IPsec as a protocol for VPNs since the late 1990s. IPsec is supported in Windows XP, 2000, 2003 and Vista; in Linux 2.6 and later versions; in Mac OS X, Net BDS, FreeBDS and OpenBDS, in Solari, AIX, and HP-UX, in VxWorks. Many have provided IPsec VPN server and IPsec VPN client services.
Microsoft has deployed PPTP client in all versions of Windows since Windows 95 OSR2 and PPTP server in all server products from Windows NT 4.0. PPTP client is also included in Linux, Mac OS X, Palm PDA devices and Windows Mobile 2003 devices.
PPTP is very popular, especially on Windows systems. Because it can be widely used, free and easy to install. However, when deployed by Microsoft, it is not the safest component of Secure VPN .
Schneier with 'Mudge' of L0pht Heavy Industries found and published deficiencies in Microsoft PPTP in 1998. Microsoft quickly corrected these problems with MS-CHAPv2 and MPPE. Scheier and Mudge then published an analysis that tested the improvements in 1999, but pointed out that Microsoft's PPTP security still depends on the security of each user's password. Microsoft has addressed this supply by forcing the strength of the password into the operating system. But Shneier and Mudge still think that IPsec should be a Secure VPN heir rather than PPTP.
L2F is a protocol developed later by Cissco. L2TP is a combination of L2F and PPTP ideas to create a data link layer protocol. This protocol provides a tunnel (virtual path), but is not safe and verifiable. L2TP can carry PPP sessions in the tunnel. Cissco has implemented L2TP in its routers. There are a few open source plugins of L2TP in Linux.
L2TP / IPsec combines L2TP's virtual path with IPsec's secure channel. It allows to change Internet Key Exchange more easily than pure IPsec. Microsoft has provided a free L2TP / IPsec VPN client for Windows 98, ME, and NT since 2002, and attached an L2TP / IPsec VPN client for Windows XP, 2000, 2003, and Vista. Windows server 2003 and Windows 2000 servers have L2TP / IPsec server.
SSL and TLS are protocols for secure data streams on the fourth floor of the OSI . SSL 3.0 model and TLS 1.0 are inherited versions that are commonly used with HTTP to enable secure Web path protection, called HTTPS. However SSL / TLS is also used to create a virtual path tunnel VPN. For example, OpenVPN is an open source VPN package for Linux, xBSD, Mac OS X, Pocket PCs and Windows 2000, XP, 2003, and Vista. It uses SSL to provide encryption for both data and control channels. Some vendors have provided SSL VPN servers and clients.
Profit and security risks of VPNs
A virtual private network can erase geographic barriers in business, allowing employees to work effectively at home and allow a business to securely connect to their agents and businesses. partner company. A virtual private network is usually cheaper and more effective than virtual private lines.
But on the other hand, the use of a VPN can expose potential security risks. While most virtual private networks are being used fairly securely, a virtual private network can make itself more difficult to circumvent by protecting the network parameters appropriately. The responsibility of network administrators is to apply the same security standards to connect computers to the network via VPN when computers connect directly to the LAN.
The combination and usage of both types of VPNs can see the potential of this company with another company. In addition, using remote control software such as PC Anywhere, GoToMyPC or VNC in conjunction with a VPN can exploit the company's network capabilities to malware in a remote station that does not connect to the VPN.
Reliability, elasticity and implementation of VPNs
Because Secure VPN uses encryption, and because some cryptographic functions are used quite expensive, a heavily used VPN can download to its server. The administrator's characteristic is to manage server downloads by limiting the number of concurrent connections to know which server can control.
When the number of people trying to connect to the VPN suddenly skyrocketed, breaking the transmission process, employees also found themselves unable to connect. Because all VPN ports are busy. This is the motivation for administrators to create application keys that do not require VPN. For example, set up a proxy service or Internet Message Access Protocol service to allow employees to access e-mail from home or on the road.
How to decide between IPsec or SSL / TLS to get a perspective can be very complicated. One thing to consider is that SSL / TLS can work through a NAT-based firewall. IPsec does not. But both protocols work through firewalls and will not translate addresses.
IPsec encrypts all IP traffic transferred between two computers. SSL / TLS specifies an application. SSL / TLS uses asymmetric encryption functions to establish a connection. It protects more effectively than using symmetric encryption functions.
In real-world remote applications, administrators can decide to combine and merge protocols to create the best balance for performance and security. For example, clients can connect to a Web-based via a firewall using the secure path of SSL / TLS. Web servers can connect to an application service using IPsec, and application services can connect to a database across other firewalls that also use SSL.
The scalability of VPNs can sometimes be demonstrated by the use for hardware services. However, in order to do that, we must overcome the competing purposes of VPN firms. Perhaps that will be the topic for another day.
VPN source
Virtual private networks maintain a list of its members, a table of components of IPsec, and a table of components of SSL VPN with the contribution of each vendor. VPNC also provides CAs with free, basic certificates, open source auditing through the package for administrators.