How to scan websites for potential security vulnerabilities with Vega on Kali Linux
Resisting a hacker attack is one of the most important responsibilities a system administrator must perform. This is especially necessary for websites that contain sensitive customer information and a large number of users. Therefore, it is important for a system administrator to take proactive measures to find and fix vulnerabilities in their websites.
A tool that scans web pages for security holes is the Vega Vulnerability Scanner. This is a free, open source web testing software developed by security company Subgraph. This tool has some interesting features like proxy scanners, but the article will focus on automatic security check aspects that can help find and validate SQL injection, cross-site scripting vulnerabilities (XSS), accidentally disclosing sensitive information and many other vulnerabilities.
- SQL Injection attacks and prevention in ASP.NET
There are web application scanners similar to Vega such as Portswigger's Burp Suite Scanner and Security Scanner from Netsparker, both of which have advanced security vulnerabilities scanners but Vega's scanner can perform many of the same tasks. which is completely free. Vega's scanner helps to find and understand the severity of vulnerabilities in web applications by clearly and concisely displaying useful resources in each scan.
How to use Vega to scan websites for security holes
- Step 1: Install Vega
- Step 2: Start Vega
- Step 3: Configure Vega
- HTTP Proxy Vega Request (Optional)
- Using Tor's User Agent (Optional)
- Average HTTP request (Optional)
- Step 4: Scan the website with Vega
- Step 5: Explain Vega's announcement
Step 1: Install Vega
Since the Vega Vulnerability Scanner is usually preinstalled on most versions of Kali Linux, you should use the Kali system. If you're not sure if Kali has set up Vega, you can run apt-get as in the terminal window below. The user will receive a message saying that it was installed if it was, and if not, use this command to install.
apt-get update && apt-get install vega
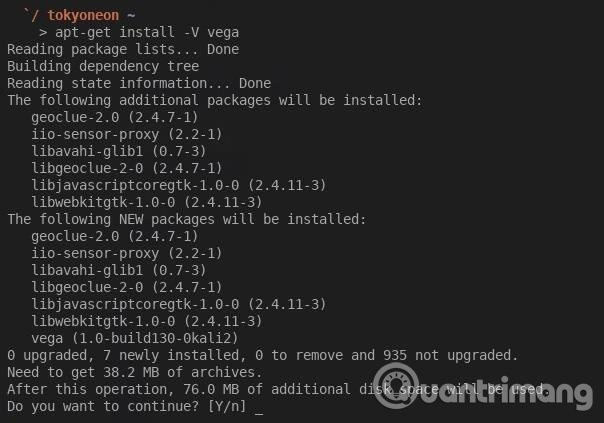
If you are using BlackArch, you can install the Vega Vulnerability Scanner with the command below. BlackArch does not use the APT package manager, so users should use Pacman.
pacman -S vega
Step 2: Start Vega
In Kali Linux, the tools are automatically sorted into categories, so click " Applications ", then hover over the " Web Application Analysis " category and click " Vega ". Depending on the use of Kali versions such as XFCE, the Applications menu may look slightly different. You can also just search " Vega " from the " Show Applications " screen.

Step 3: Configure Vega
After starting the application for the first time, you should see the options available. In the top left corner, click the " Window " menu, then see " Preferences ".

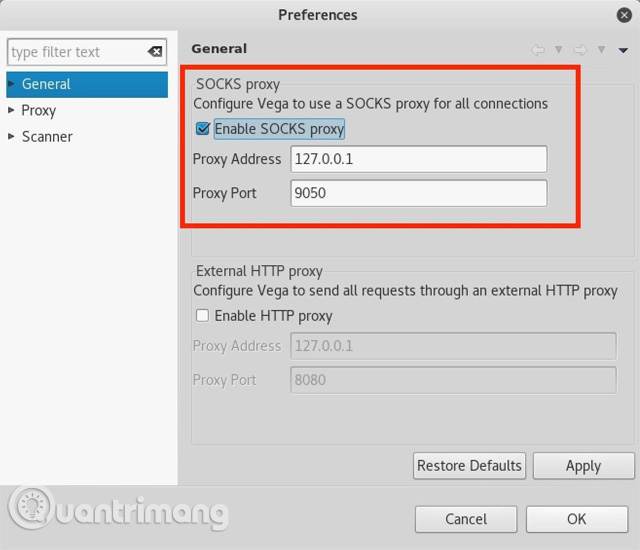
HTTP Proxy Vega Request (Optional)
If you want to anonymously scan Vega and proxy all connections, select the option " Enable SOCKS proxy " under General and enter a proxy address and port. If you're using Tor, enter the default Tor address and port (127.0.0.1:9050). This will help hide the scan source. If you are using a free or premium proxy service, select the address and port you want.
Using Tor's User Agent (Optional)
If you decide to scan Vega via Tor, you can also consider changing Vega's user agent to the Tor user agent. This will help users access some websites (but not all) that block Tor HTTP requests.
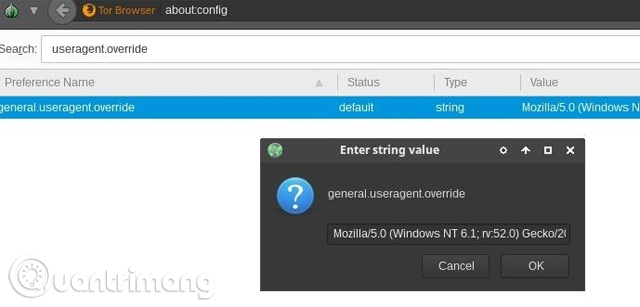
To modify the Vega user agent, click on the " Scanner " list and enter the user agent of the Tor Browser next to User-Agent, then click " Apply " and " OK " to save the changes. Below is the current Tor Browser user agent since February 2018.
Mozilla / 5.0 (Windows NT 6.1; rv: 52.0) Gecko / 20100101 Firefox / 52.0

The Tor Browser user agent will change according to any major Tor Browser updates. To find the latest user agent, open the latest Tor Browser and enter about: config in the URL bar. If you see a warning warning, select " I accept the risk ", then enter useragent.override in the search bar.
- The "About: Config" tricks improve Firefox browser
Double-click the display entry, allowing users to copy the user-agent string. Alternatively, you can also right-click and select " Copy ".
Average HTTP request (Optional)
Another thing in the Scanner menu that users may want to modify is the Maximum number of requests per second to send option . By default, the software is set to 25 requests per second.
Depending on the scenario, the requirement per second may be too much or too little. Suppose you have the right to scan a website with Vega, ten requests per second is probably the right number to start. With the websites you own, 100 requests per second may be more appropriate. The number of requests is entirely up to the user.
You will not notice an increase in processing power by using multiple requests per second, so it is safe to set that number higher. Vega is not a DDoS tool, Internet bandwidth and web bandwidth will automatically reduce the requirement.
- The easiest way to speed up Internet, bandwidth right in Windows

Listener settings in " Proxy " are options that are not related to scanners. " Debug " option in the Scanner section for Vega developers.
Step 4: Scan the website with Vega
Now, Vega has been installed and configured, you can start scanning the site. To start scanning, open the " Scan " menu at the top left and click on " Start New Scan ". The Select a Scan Target window will appear, enter the URL you want to scan into the box below Scan Target, then click " Next ".

Vega has dozens of modules designed to search a wide range of popular web server vulnerabilities such as SQL, XSS and XML injection vulnerabilities. If you want to activate all scanning modules, just select all and click " Finish " to start scanning the website. If not, uncheck the modules you don't care about on the first run.
Note: If you do not need to adjust the Authentication Options or Parameters options , simply select " Finish " after selecting the modules.
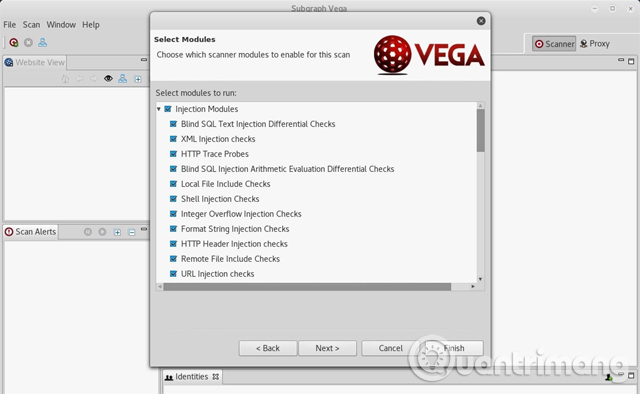
This scan can take 2 to 8 hours to complete depending on the size of the website and the requirement that each second has been placed before. Users know the scan has started when the website appears in the Scan Alerts tab. When the scan is complete, you will receive a detailed report of the security vulnerabilities found.
Step 5: Explain Vega's announcement
When the scan is complete, Vega will clearly and briefly present the summary of the alerts. If Vega reports on "High" vulnerabilities, users don't need to panic. Vega's modules are very sensitive and sometimes create false false positives for vulnerabilities that may not actually exist. Sometimes this is not a bad thing. Therefore, you should comb through the report and check each alert manually.
Vega does a great job explaining the meaning of each alert, their impact on the site and how to fix the vulnerabilities. It also includes useful references that can help users better understand how to deal with vulnerabilities. Clicking on one of the alerts will display tons of useful information.

Vega is a great tool to help security researchers better understand Pentest security reviews. With multiple module choices, even new users can delve into potential security risks and assess its severity to websites. Anyone who is interested in improving website security and enhancing hacking skills on the web will love Vega and its ease of use.
See more:
- Security vulnerabilities - basic insights
- Find security holes on every site with Nikto
- Oracle patched 101 security holes
You should read it
- ★ How to fix BlueKeep security error for Windows 2003, Windows XP, Windows 7, Windows Server 2008
- ★ 5 common errors in managing security vulnerabilities
- ★ Mac computers stuck with a dangerous security vulnerability, Apple was announced in February but has not yet resolved
- ★ Internet Explorer has vulnerabilities, unused users are still hacked
- ★ Serious security vulnerability on Intel chips