How to conduct IoT pentest with Kali Linux
Kali Linux can be used to perform many pentest tests on computers in combination with other related techniques.
With an overall security strategy related to device-specific operating systems, firmware and network configurations, Kali Linux can serve as one of the penetration testing tools targeting devices. Smart Internet support.
When learning how to work with Kali Linux, you will find it useful to cross-examine the IoT network and its devices for potential vulnerabilities, exploit exploits, sniffing and spoofing, passwords, social engineering, etc. .
The following are the penetration testing platforms and methods for IoT devices related to Kali Linux.
How to get started with Kali Linux?
To get started, you'll need to install Kali Linux on a bootable PC or USB with Kali Linux ISO on it. On Windows systems, you can start the Kali Linux GUI from the 'Advanced startup' menu, then select USB / EFI mode.
The first home screen will give you a few options to get started. Select 'Live system (forensic mode)' to boot the PC into Kali Linux.
Many penetration tool options are available from the 'Kali Live' menu.

General pentest strategy for IoT devices
Unlike Internet-enabled computers, penetration testing for IoT devices has many barriers. Not just need a home WiFi network to test. You need exploit exploits to work on BLE, Zigbee, LoRaWAN, MQTT and many other networks.
Next, there are many pieces of hardware that can be targeted: Chip, sensor, camera, API, etc. The hacker or pen tester must be able to target the chapter to the device's operating system or firmware.
This makes penetration testing more diverse and difficult. However, this is why hackers are also more elusive. But some smart devices may be hiding a major flaw that can be exploited using a penetration tool like Kali Linux.
Just two or three weeks ago, Ring Doorbell posted information about device hijacks, multiple suspicious login attempts, and even hackers created their own podcasts of hacked footage.
According to the Ring spokesperson, the attacks were caused by device owners not activating two-factor authentication (2FA) and using very simple passwords that can be found in the database. metasploit hacker.
How to test penetration for IoT devices?
Using the above suggestion, design a strategy to penetrate a video doorbell device with a simple password or the owner has set a password that is easy to guess and does not have two-factor authentication.
This trick will assume that a smart device with an IP address is exploited through someone who has access to the remote network.
The example will use a very popular online password attack with Kali Linux called Hydra. In this attack, the login cracker uses an extremely large password database to hack devices with weak passwords.
Use the location command of the metasploit file to try and recover the password from an insecure device.
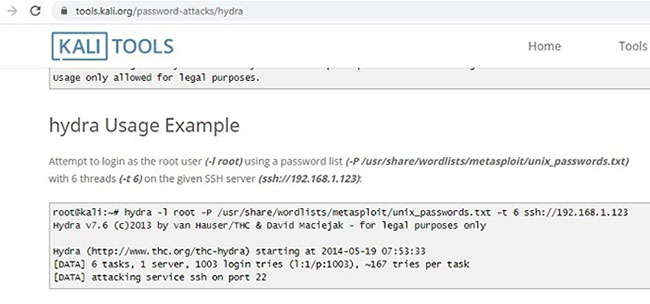
You need to go to the relevant directory where the password has been stored for metasploit. In this case, it is saved in the user / share / wordlists directory.
There is a large collection of stored passwords. One of them will be displayed if the result matches the penetration test of the Hydra tool.
The brute force method will certainly work with IoT devices that come with default passwords that never change. If you've started working with Kali Linux, you can guess what hackers think. In addition to the more than 600 common hacks and exploits introduced on the Kali website, you can find many other third-party references, such as the video doorbell example above.