Find security holes on every site with Nikto
There are several tools and applications to find security vulnerabilities in web pages, but one of the simplest tools is nikto . This small and simple tool checks a website and reports security vulnerabilities. Although it is extremely useful and effective but not 'sneaky', any website with IDS or other security measures will detect that you are scanning it.
- Some basic security rules for websites
Step 1: On the computer running the Kali Linux distribution, access Kali Linux -> Vulnerability Analysis -> Misc Scanners -> nikto .
Although there are many options for nikto, but we will use the following basic syntax:
nikto -h
Step 2: Scan the Web server (Web Server)
Let's start with a secure web server, in this example the http service. Scan for vulnerabilities by typing:
nikto -h 192.168.1.104
- What is HTTPS? and why is it needed for your site
Nikto gives a lot of information as shown below:
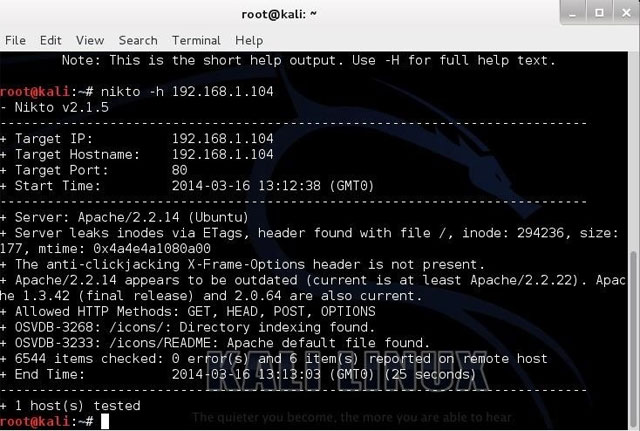
First, information indicates that the server is Apache 2.2.14, probably on Ubuntu. It provides more information about other potential security vulnerabilities on this web server. Note, at the bottom of the page are OSVDB security vulnerabilities. This is the database of open source security vulnerabilities.
Step 3: Scan the website
Try another site, try it at webscantest.com.
nikto -h webscantest.com
It identifies the server (Apache) and then proceeds to identify many potential security holes that are predetermined with OSVDB. You can visit the Osvdb.org website to learn more about these vulnerabilities.
Now, use this page to find information about one of the vulnerabilities identified by nikto like OSVDB-877 .
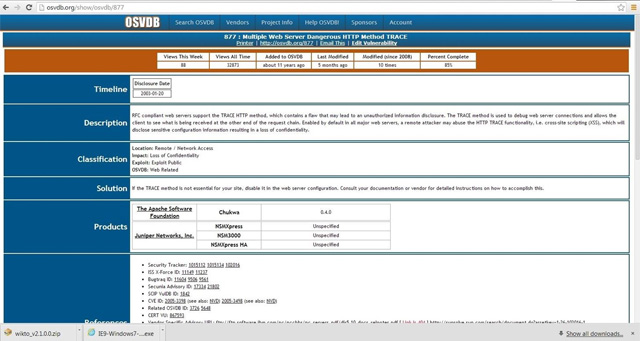
Note, in the lower half of this page there are cross-references to various sources of information about this vulnerability, as well as references to tools and filters like Nikto, Nessus and Snort.
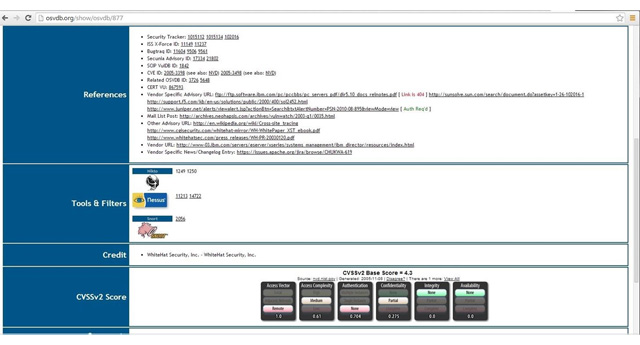
Scan the WonderHowTo page
Scan a few other websites and see what information it provides. Here scan the page, Wonderhowto.com.
nikto -h wonderhowto.com

Nikto said that WonderHowTo is using Microsoft's IIS 8 as a web server and then lists many security vulnerabilities. However, exploiting the vulnerabilities listed will reveal that all of them are false-positive errors because WonderHowTo simply returns a harmless 404 page. This is because WonderHowTo is not built on php or asp.
Such validation errors can occur because the scan does not actually perform every possible vulnerability but only scans to see if the server responds without error with exploitable URLs. or not.
Scan Facebook
Finally, try scanning Facebook.
nikto -h facebook.com
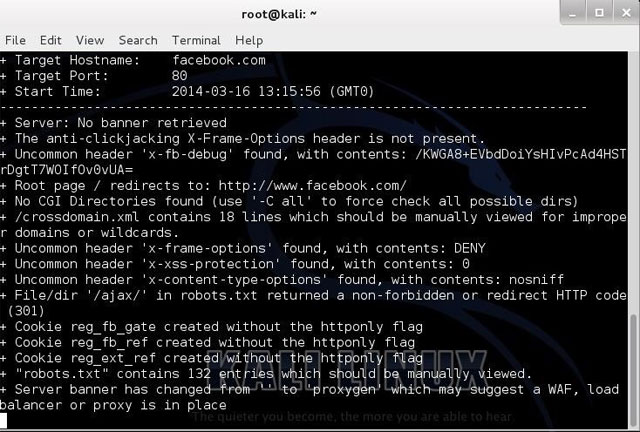
As you can see, Facebook is tightly secured with little security holes.
You should read it
- ★ 5 common errors in managing security vulnerabilities
- ★ There is a new zero-day vulnerability in Windows
- ★ Foreshadow - the fifth most serious security hole in the CPU in 2018
- ★ Vulnerabilities discovered in many web browsers that allow users to be tracked through installed applications
- ★ Security vulnerabilities - basic insights