How to hide confidential data in images or audio files in just one note
Steganography is the art of hiding information and in this tutorial, we will use Steghide - a simple command line tool to do that.
What is steganography?
Unlike encryption, there is an information that is explicitly hidden, Steganography hides data in a simple view, inside a file such as an image, an audio file.
- What is data encryption? Things to know about data encryption
Steganography is very useful in encrypted messaging situations such as in countries where freedom of speech is not available. It is also commonly used as a digital watermark to find stolen images or audio files.
How Steganography works
There are a number of different techniques for hiding data inside regular files. One of the most widely used and perhaps simplest uses is the Least Significant Bit, commonly known as LSB.
This technique changes the last few bits in a byte to encode a message, particularly useful for images, where the red, green and blue values of each pixel are represented by 8. bits (one byte) range from 0 to 255 in decimal or 00000000 to 11111111 in binary form.
- Basic measurement units in computers
Changing the last two bits in a completely red pixel from 11111111 to 11111101 will only change the red value from 255 to 253, but the naked eye cannot recognize the color change but still allows us to encrypt data inside the picture.

The smallest weight bit technique is also used for audio files. There are two things to consider when hiding information is encrypted and compressed. Encrypt data before embedding it in additional security layers while compressing data.
How to hide data in images or audio files
Step 1: Embed data into a file
Using Steghide is easy, to install it from Terminnal in Linux, just use apt .
apt-get install steghide
When the installation is complete, embed the data into a file, enter the command below.
steghide embed -ef secretFile -cf coverFile -sf outputFile -z compressionLevel -e scheme
The statement elements are broken down as follows:
- -ef determine the path of the file you want to hide, you can embed any file type inside the cover file like Python script or shell file.
- -cf is the file that the data is embedded in, it is limited to BMP, JPEG, WAV and AU formats.
- -sf is an optional argument specifying the output file. If omitted, the original file will be overwritten by the new steganographic file.
- -z determines the compression level, from 1 to 9. If you don't want to compress the file, use the -Z argument.
- -e specify the encoding type. Steghide supports multiple encoding types, and if ignored by default, Steghide will use AES 128-bit encryption. If you don't want to use encryption, just type -e none .
In this example, confidential information is hidden in the image of a cat, not overwriting the original image or compressing it, only encoding the image.
steghide embed -ef secret.txt -cf StegoCat.jpg -e none -Z
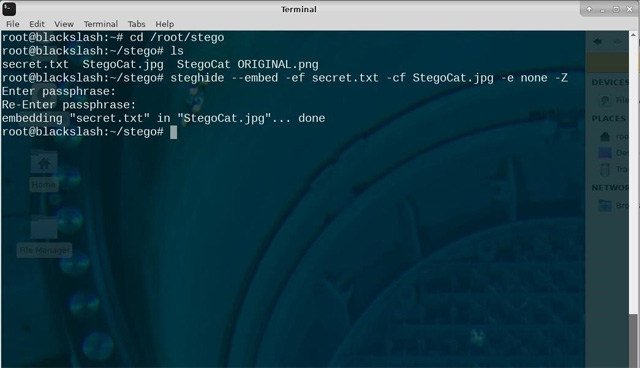
After executing the Steghide command, there is a password setting message to extract the embedded data that appears, enter the password and confirm again.

Step 2: Extract hidden data from the file
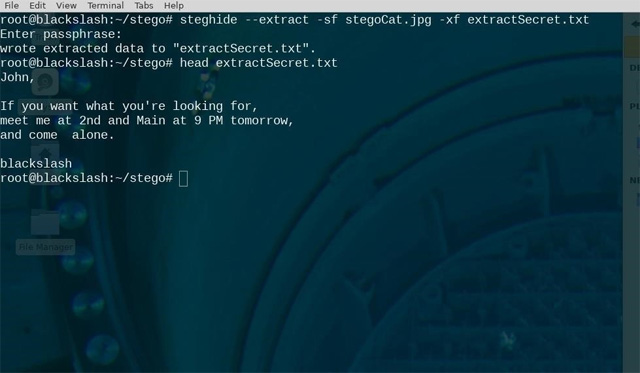
Extracting hidden data from a steganographic image is even easier with the following command:
$ steghide extract -sf stegoFile -xf outputFile
When running this command, you will be prompted to enter the same password created above.
I wish you all success!
Alternatively, you can use cmd to hide confidential documents in images Hide confidential documents as images
See also: Instructions for setting password to protect files and folders in Windows