Error on Chrome allows recording and video recording without users knowing
Ran bar-Zik, a web developer at AOL, discovered a bug (bug) on Google Chrome that allowed the website to record audio and video footage without a visual indication. This error is not too dangerous because the infected pages still need users to allow the use of components related to images and sounds, but there are many different ways for them to record or record that users do not know. The only image of this error is the icon that Chrome usually displays when the user records or streamed the video.
Chrome red circle icon
Bar-Zik told Bleeping Computer that he discovered this error while working with a website running WebRTC code. WebRTC is a protocol for streaming audio and video over the Internet in real time. To do so, users must give access to component audio and video for that website.
Upon receiving access, the website will run JavaScript code to record audio and images before posting to the Internet for other WebRTC participants. This recording process is done through MediaRecorder API based on JavaScript.
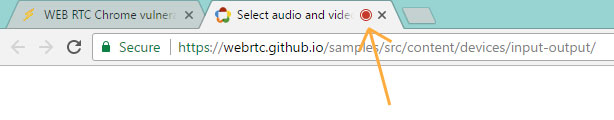
The attack code opens through Chrome's popup window
Bar-Zik discovered that this code recorded without having to run on the browser card that it received access to. Because access to audio and video data was given to the entire domain, the Israeli developer realized that he could open a popup window on Chrome and run the code for recording and recording.

Window popup when recording, recording
Chrome displays the icon on the browser tab, not the popup window because this window has no tab bar.
Report a bug with Google but the error has not been fixed immediately
Bar-Zik told Bleeping Computer that after verifying the problem, he reported the error to Google. The report comes with a demo that requires users to grant access, open a popup window when they click and record 20 seconds, then provide a link to download the recorded file. Interested readers can download the code to prove this error here.
In the response Bar-Zik received, Google refused to consider it a security error.
This is not really a security hole. WebRTC, for example, on mobile devices doesn't have a browser indicator either. That icon is an optimal priority effort that can only work on computers when the Chrome interface space can be met. We have sought to improve the situation.
The problem can be used for stealth monitoring
Bar Zik disagrees with Google's review. Researchers believe that many people tend to click on requests that require access without even reading through. Once unintentionally or deliberately empowering a website to access audio and video components, more complex attacks can occur.
For example, Bar-Zik thinks an attacker can use a small popup window to open the attack code. This code uses a camera to take pictures of users, recordings or sounds nearby. If they do not pay attention to this window, they will not know because there is no indication of recording or recording. Another scenario is that users can think of this popup window as an advertisement. If not turned off immediately, the attacker can monitor the user's computer.
Bar-Zik also said that an attacker doesn't need to create a website to ask for access. He can exploit XSS script (Cross-site scripting), insert malicious code on websites that have already received access. These vulnerabilities will bring the attack code into the computer.
Google is not wrong either
Because this is not considered a security issue, Chrome does not receive emergency recovery. However, Google is not wrong to consider this a security issue because this red circle icon is not available on all Chrome versions. Users who want to be safe from these attacks should pay attention to the access they give to the website.
You should read it
- ★ Discovered seven extremely serious security holes in Google Chrome
- ★ Warning: Google Chrome is experiencing serious security errors, patch updates right away
- ★ How to enable Site Isolation security feature on Chrome
- ★ Please download Google Chrome 62 for Windows, Mac and Linux
- ★ Released Google Chrome 66, focusing on security