Comprehensive guide to Windows 7 security - Part 3
In this section, I will show you some basic information you need to know to secure Windows 7 properly, besides some lesser-known security functions that you can use to secure Windows 7. This new operator provides . We will also introduce ways to help you prevent attacks, ensure data security and recover from attacks quickly.
>> A comprehensive guide to Windows 7 security - Part 1
>> Comprehensive guide to Windows 7 security - Part 2
It can be said that Windows 7 is designed to be safer. When used as a standalone operating system, Windows 7 will protect individual users well. It has many useful security tools inside, but only when used with Windows Server 2008 (R2) and Active Directory, protection will be more effective.
In this article, I will show you some basic knowledge needed to secure Windows 7 properly, help you achieve basic security, consider some advanced security configurations as well as go explore some of the lesser known security features in Windows to prevent and protect against possible attacks. The goal of this article is to introduce the security features of Windows 7, their enhancements and applications, and provide you with the knowledge of planning and using the right security features. this. The concepts that we introduce will be broken down and organized by block method.
Note : If you work in a company or other professional environment, you should not make adjustments to your company's computer. Follow the published security plan (or policy), as well as the best practices, principles, and guidelines published in the organization. If you're not familiar with security topics and Microsoft products, read the product documentation before applying any changes to the system.
Disaster recovery
When Windows 7 is fully secured, it needs to be backed up so that it can be restored quickly. You can use imaging software to take a snapshot of the basic installation so it can be quickly reinstalled if needed. If you have to reinstall Windows 7 from the rubble, you also need to do all the steps that have taken security. Because this job can take a long time, we should consider recovery solutions, especially if Windows 7 is used in the enterprise. The company solutions have complete imaging capabilities. Meanwhile, home users can also create a snapshot of their systems so that they can recover quickly. Either way, you can always use tools like System Restore, which allows you to take a snapshot of the system, but only if you can boot the system. The only way to recover from a comprehensive disaster is to plan ahead on that issue and build a thorough recovery plan. A simple recovery plan will be when the installation is completed, then make sure the installation disks are safe for future use. If disaster strikes, we will fix the system and if it cannot be fixed, recover the data and reinstall Windows from the installation disks. This process will take a long time and you will be at risk of losing data. A plan to respond to disaster recovery will include many ways to protect your data and provide many options for quick recovery:
- Install Windows 7, applications, toolkits and strengthen the system
- Create a system backup (imaging, virtualization, creating restore points, .)
- Prepare solutions to backup and restore centralized data
- Deploy use, wait for incident or disaster
- When things happen, find the root cause and fix it
- A disaster will make the system far beyond repair capacity and fall into a state of stopping production
- Quickly restore the underlying operating system with applications, upgrade through imaging or virtualization
- Re-apply data (PST, .) through centralized data store and drive mapping.
- System users return to work quickly without losing important data.
All systems will make sure there are some types of errors no matter how well prepared you are. Drive errors, application errors, security errors, etc. So, in your security plan, you should consider these and allow you the opportunity to recover. You also need to consider how to recover when a problem occurs with the system. Windows 7 offers a lot of options to bring your data back and work quickly when a disaster event occurs.
If you need to repair system files, or restore a previous copy of the operating system, you can do it easily with Windows 7. Windows 7 provides many tools to help you protect and backup your personal data. me, as well as the operating system itself. The use of tools such as ERD, ASR, Backup and Restore, System Restore, Recovery Console, Safe Mode, Last Known Good Installation and other options have helped administrators and users to drive disaster from release XP. Many of us have used some Sysinternal tools to rebuild the system and run after encountering serious errors (BSOD).
Backup and Restore will also include Data Backup. Backup the system itself is done with System Restore (Figure 1), where you can configure the operating system restore point for future use.
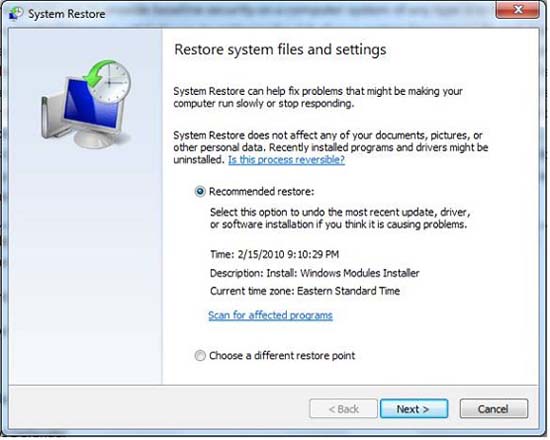
Figure 1: Use System Restore to create a restore point
Note: System Restore is used to snapshot the system, this snapshot is then saved to the hard drive. If you want to go back to that restore point, you need to be able to use System Restore again. If System Restore is compromised; you will not be able to use the restore point and need to rely on imaging, or reinstall.
You can also rely on imaging tools to quickly reinstall the operating system that cannot be repaired. Installing Windows desktops from scratch is a fairly long process, especially if you are running a system such as XP. There are many hot fixes, upgrades and service packs to be used, as well as updates to applications like Microsoft Office. One way to fix the time needed to restore a system that cannot be operated by a virus is to have an image. If System Restore or other tools can't make your system work again, you need to use a new copy of Windows, but don't use hot fixes and updates now - because you can Being a victim of the same problem has caused your system to fail before.
Data is the most important thing that anyone must care about. Personal data (or company) should be available at all times and never be lost. In an enterprise environment, data is usually backed up, stored carefully and will be brought out for recovery if disaster strikes. In the family, such a way should also be done. Whether or not you want to create an offsite copy for your data, but the backup to be able to restore later if needed is the first thing you need to consider even before thinking about how to restore Windows 7 in love. how urgent The right design solution should be to keep a copy of your personal data in an external hard drive. Connected via USB (or FireWire), your data can be accessed at any time. You can also mirror copies to a second hard drive, or even use an in-house tape solution for safer data protection. If you are running a family business, you may want to add data security to prevent problems with your family when your business is not affected. cause of it. So, in general - you need to be prepared. The best way to recover when you encounter a data error or accidentally delete is to backup your data to keep it safe.
Using centralized solutions is the key to making your important data secure and available. For example, if you save all your data on an internal hard drive and never back it up, then you will face the risk of losing data because the hard drive is faulty and cannot be repaired. A simple solution is to use backup options to a minimum, copy it to an external hard drive. All hard drives can fail so until newer technology catches up with the technology deployed, we will see home computers and enterprise arrays filled with the drives. Waiting for errors to occur at any time. You must backup the data or suffer the consequences to lose it. Once you've pointed out that problem, all you need to do is find a way to quickly recover Windows with effort and minimal time.
Tip: It's best to plan for the worst scenario. If you think your system will eventually be broken and irreparable, having a good backup of your system and data will be your lifesaver. In short, the security and containment plan, even if done perfectly, is still not 100% safe, so plan to reuse Windows 7 if you need it.
It is easy to set up a disaster recovery plan for your operating system with virtualization. You can download and install Virtual PC, or Hyper-V from Microsoft. Hyper-V provides a platform that allows you to create, manage, and test virtual machines (VMs). If you are running Windows 7 at home, you can still virtualize your system or resources and take advantage of its advantages within Virtual PC (for example). In this way, if you want to create a VM as a backup, you can. A useful tip that you can apply at home is what businesses are deploying to change the way they manage software and deploy systems. Virtual PC / Server or Hyper-V will give you many opportunities to quickly change the way you work from home. If you use VHD (a virtual hard drive file), you will always have a copy for your system. You can use Disk Management to create a Windows 7 VHD as shown in Figure 2.
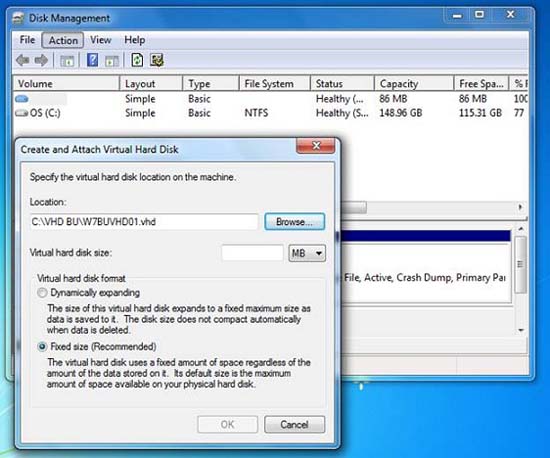
Figure 2: Creating a virtual drive using Disk Management
If in the enterprise, systems and resources can be virtualized and data can be readily available in Storage Area Network (SAN) or Network Attached Storage (NAS) devices, this will solve the problems related to disaster recovery time. If all the files used by the client that the user can find through the mapped drive with the file server, basically all you need to do then is wait for the system hardware error. happens and brings the system back to work on new computers. Most corporate environments with state-of-the-art systems have additional hardware. If you design and use redundant server concepts and use virtualization to balance, you can quickly fix the problem, within the calculation unit is seconds, users can backup and run that No loss of my working pace.
In short, always backup your data and protect the system. Strengthen it to the best of your ability, but it should also allow you to get back up and running without spending a lot of time on installing software, drivers and reconfiguring the system.
Note : Incorporating fire safety issues, or offsite backup solutions for data to prevent environmental disasters.
Advanced security features
Windows 7 has many advanced security features that you can use, such as encryption and biometric options. Secure communication over unsafe connections must be secured. Controlling access, exploiting the collected information is something you need to plan when deploying Windows 7, because disasters can occur and data is also so that it can be lost at any time. . Worse, because mobile jobs and laptops are used for personal purposes, security is at risk when users lose their laptop, leave it somewhere or may be stolen. If USB is used and lost, how will your data be kept safe? To prepare for these problems, you can deploy the following security features with Windows 7:
Biometrics - Biometric problems are used to control access. Most systems (especially IBM / Lenovo ThinkPad series) have introduced fingerprint recognition. This technical innovation can be used for any system, from home, business, or elsewhere. Public libraries will abandon the use of library cards and replace them with a retina scanner. Parental control applications for children at home and personal functions will be performed in the form of biometric ID. Windows 7 is ready for all that. Microsoft has worked specifically with fingerprint recognition developers and hardware vendors to ensure that Windows 7 is ready to do what it promises. Identity management is an important issue to consider when applying security.
BitLocker Drive Encryption (BDE) - BitLocker (and BitLocker to Go), is used to provide data security issues contained in both external and internal drive systems. With Windows 7, you can use both versions of BitLocker to secure data on internal hard drives, external drives, USB drives and other portable storage formats. BDE can protect data stored on these drives by requesting certificates to access it and also using TPM.
Microsoft's Trusted Platform Module (TPM) feature is only available on TPM consensus hardware. When agreed, Windows Vista / 7 and Windows Server 2008 can use advanced security features and features. Microsoft's Trusted Platform Module (TPM) Management is a new feature included in Windows Vista / 7 and Microsoft Windows Server 2008. Its basic function is to allow Windows systems to use advanced processes and functions. hardware encryption at the hardware level. As mentioned above in this article, one of these features requires relatively high (compatible) hardware. If you want to use a feature and find it in a non-active or inaccessible state, chances are that your hardware does not agree with this feature, or you may be using it. wrong version of Windows 7 and that feature is not available in your version.
Tip : TPM can be configured and managed through the BIOS and MMC snap-in components we have installed above.
You can also securely connect to remote resources with Windows 7 by configuring IPsec / VPN connections. Virtual Private Network (VPN) is a term used to describe the type of security applied to keep you safe from attacks. You will still be making connections through an unsecured public network, but because the encrypted tunnel is used, your data will be private and secure. You can create a new VPN connection quickly by going to the Start menu, typing VPN and following the Control Panel link to create a new VPN connection as shown in Figure 3.
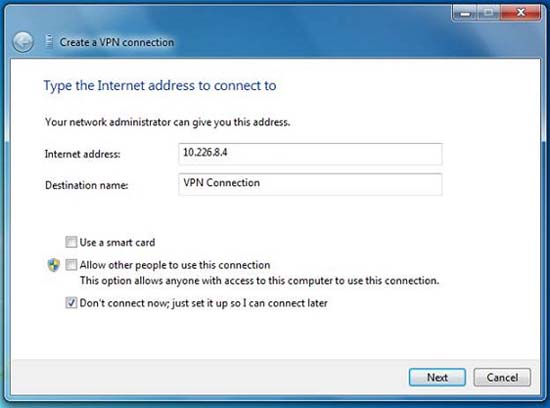
Figure 3: Configuring the VPN connection
You can create connections with other systems using advanced protocols that provide security through encryption algorithms. This problem often requires a processor capable of providing hardware encryption options. VPNs can be used to create secure connections for different systems.
Note : If managing remote Microsoft systems, you can use Remote Desktop Connection (RDC). If you use Telnet as a remote connection tool for Unix systems and Cisco network devices (for example), you should consider disabling this service (disabled by default) and using Secure Shell (SSH).
You can also create manageable tunnel connections with the IPsec protocol and manage them with the MMC or Windows Firewall management interface. There are even features within this interface that allow you to manage and troubleshoot IPsec connections such as typed keys, security association issues (SA), file problems Encoding, setting time as well as other ISAKMP configuration issues. These problems can also be managed in Windows Firewall, Advanced Features.
When access and recovery control options are selected and you can securely connect to network resources through encrypted tunnels, what happens if you want to share resources in a way? safe on the company or home network? Windows 7 provides a new function called HomeGroup, which is available in Control Panel. You can configure it to make changes to the system to connect other computers on a secure home network to share resources as shown in Figure 4 below.
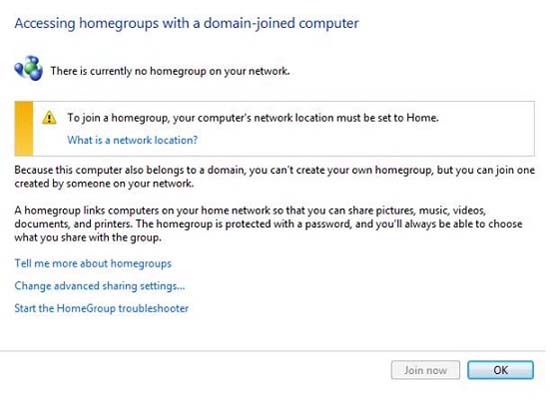
Figure 4: Configuring Windows 7 HomeGroup
Windows 7 can be configured to securely share resources with other systems on your home network. HomeGroup can provide a basic level of security for accessing, using, and sharing data. For example, if you configure two computers on a home network and one of them uses a local printer, HomeGroup will allow you to share that printer as a resource for all systems. can use it. You can also set a password to protect it and specify who can use it and who doesn't. With Windows 7, this alternative to using the Workgroup function. However, not all versions of Windows 7 allow you to create a HomeGroup. Versions of Windows 7 can join a HomeGroup, but only one HomeGroup can be created in Home Premium, Professional, or Ultimate versions.
Obviously, Windows 7 will be safest when using it with Windows Server 2008 in an Active Directory environment. Running the enterprise class operating system will open the door to the most complete testing and blocking features. For example, web surfing can be controlled and checked with Active Directory, Group Policy, especially blocking templates, kits as well as tools such as proxy servers. Users can log in to the domain (Domain) and can be managed and inspected completely. Anything the user does can be recorded. Any tool or service that Windows provides can be customized, changed or removed completely.
With Forefront products, all aspects of computer use, identity verification, logging and testing are available and managed in a centralized interface. You can upgrade Windows Server to a higher level by integrating with Forefront. Forefront is a new line of Microsoft products that can provide a complete security experience for businesses. It provides server, desktop, access control and personal solutions for SharePoint and many other components. When running Windows clients in an enterprise environment, this solution can provide the ability to fine tune security settings as well as multiple options for centralized management and testing.
In some cases, you may have to run Active Directory. For example, what will happen to you if the policy requires you to verify all access to company resources and keep a copy of all employee emails? When working in an enterprise, you will definitely encounter an assessment - especially if you work in a commercial company. 'Must' data is protected and can be restored. Certain levels of security must be set and this is done with government law.
In the enterprise, you will be more secure for workstations or desktops by using Active Directory (AD DS) directory service, domain model, Group Policy and other tools to focus and control the security function. Kerberos is upgraded to keep all transactions safe via tags. This will create a secure platform for what is built above it. If you build on that platform, the ability to apply advanced control levels will not stop here.
Windows 7 can be managed as a client and when done in a domain model, the Active Directory provides security by integrating all services, the ability to control access to it and go. The same is a number of options for security deployment strategies, such as installing only the 'core' component of what is deemed necessary to limit the attack surface to the lowest, or install and configure Figure, add services, all through options and toolkit. In addition, when Group Policy is properly applied, it can help you deploy many of the features we discussed, for example, you can integrate BitLocker and AD and then deploy the same policy. You can control Internet Explorer as well as restrict access, lock it all with configured lists of malware sites and blacklisted networks.
You can also deploy advanced security features of Windows 7 to further tighten security, such as:
Advanced DNS Security - Extension Domain Name System Security (DNSSec) with Windows 7 support will give you a new level of security for name resolution. Because DNS is so important and is the backbone of most solutions, it is also the target of many attacks. RFC 4033, 4034 and 4035 list new standards for DNS security storage and Microsoft has compiled with Windows 7.
DirectAccess - DirectAccess is a feature of Windows 7 that allows working on the fly and the ability to work remotely over the Internet without using VPN technology. DirectAccess is tightened with enterprise resources to allow you to securely access them remotely. It also allows mobile users the ability to receive remote support from IT staff. DirectAccess also allows you to manage remote computers and upgrade them through Group Policy. It also uses IPv6 on IPsec to encrypt traffic through the public Internet.
AppLocker - When working with Local Security Policy Editor (or Group Policy), you can configure AppLocker, a feature in Windows 7 that can control your installed applications. When configured, you can block, restrict and control desktop applications. It does that through a set of rules. You can configure rules for application control, how updates are managed, and so on. Figure 5 shows the Local Security Policy editor in Windows 7, where you can configure application security with AppLocker .
Figure 5: Use AppLocker to secure applications
Finally, always consider your network. Wireless systems are very easily compromised systems. Routers, switches and other management devices in the network are all vulnerable to attack if not solidified. That's why the concept of Defense in Depth is so important - you need to explore the entry points and the areas that can be exploited.
Tip: With Windows Server 2008 R2 and third-party products such as Cisco Systems, you can deploy NAP / NAC to secure and enforce access control policies. Với Microsoft, cơ sở hạ tầng Network Access Protection (NAP) gồm có các máy khách NAP và các máy chủ Health Registration Authority (HRA) và có thể được điều khiển tốt hơn thông qua Network Policy Server (NPS). NAP sẽ điều khiển truy cập máy khách thông qua một chính sách đồng thuận được cấu hình trước. Nếu máy khách không có đủ các yêu cầu cần thiết, nó sẽ bị yêu cầu nhập vào đầy đủ các yêu cầu đó. Nó cũng có thể được cấu hình để khóa hoặc từ chối sự truy cập. Cisco sử dụng kỹ thuật tương tự như vậy mang tên Network Admission Control (NAC). Khi sử dụng cùng trong các môi trường Microsoft/Cisco, bạn có thể tạo mức bảo mật và kiểm soát cao.
Conclude
Hệ thống Windows 7 tại nhà có thể được khóa chặn và quản lý dễ dàng. Thậm chí còn có thể cấu hình một cách an toàn để có thể truy cập Internet từ một vị trí từ xa nếu bạn rời nhà mà vẫn để máy tính ở trạng thái tích cực. Windows 7 có thể được bảo vệ để 'đạn bắn không thủng' nếu bạn thực sự muốn làm vững chắc nó ở mức khóa chặn toàn bộ. Tuy nhiên nó cũng có thể trở thành đối tượng tấn công nếu bạn sử dụng máy tính trên Internet. Do đó chúng ta cần lên kế hoạch cho những gì có thể xảy ra và làm vững chắc Windows 7 theo đó.
Khi xem xét việc sử dụng Windows 7, với tình hình các tấn công, các khai thác hiện nay ngày một nhiều và tinh vi, các tùy chọn bảo mật và khả năng linh hoạt là sự ưu tiên hàng dầu trong việc tạo quyết định. Windows 7 quả thực an toàn, tuy nhiên không thể 100%. Bạn phải sử dụng kiến thức, các công cụ và các cấu hình nâng cao để bảo mật tất cả các khía cạnh của nó và sau đó nâng cấp và kiểm tra chúng một cách thường xuyên. Tất cả những công việc đó rất đáng giá nếu bạn tránh được tấn công. Bên cạnh đó Windows 7 còn có nhiều cải tiến về bảo mật và có thể được cấu hình để khôi phục một cách nhanh chóng.
Thêm vào các nguyên lý bảo mật cơ bản, chẳng hạn như Defense in Depth cần phải được áp dụng kết hợp với các hướng dẫn bảo mật khác và các biện pháp bảo mật tốt nhất để không chỉ áp dụng bảo mật trong bảo vệ mà còn làm gia cố thêm nhiều lớp bảo mật khác cho việc phòng chống.