Build wireless networks with a broadband router - Part 3: Connect wireless computers to the network
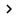 Part 1: Prepare the hardware
Part 1: Prepare the hardware
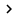 Part 2: Configure the router and the machines in the network
Part 2: Configure the router and the machines in the network
Connect wireless computers to the network
Through the previous two parts of this series, all computers that are now directly connected to the router with a regular cable can access the Internet.
The next step is to allow computers using wireless connections to access the network and access the Internet.
Your wireless network will be listed in the list of available networks on computers with wireless network cards within the broadband router range.
So all you need to do in this step is to click on the available wireless network icon on the task bar or double-click the wireless connection in Network Connections ( Start > Control Panel ) to see a list of wireless networks. in there. As shown in Figure 18, we have a number of networks (from a neighbor's network or an external network . so encryption is a very important issue). All you need to do is double click on the network you want to connect to (in this example, MyHome ).
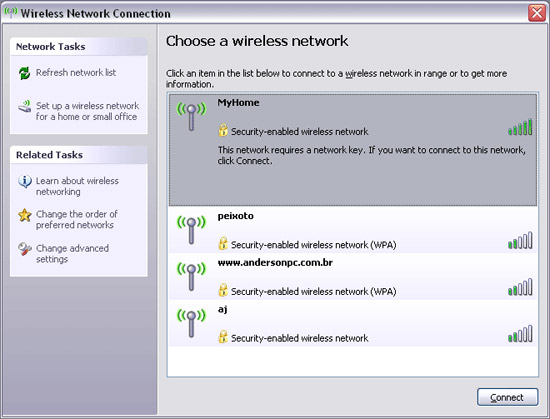
Figure 18: Wireless networks available
After double-clicking on your network, Windows will ask you about the encryption key (the 26-character string you wrote down), see Figure 19. You need to re-enter it here.
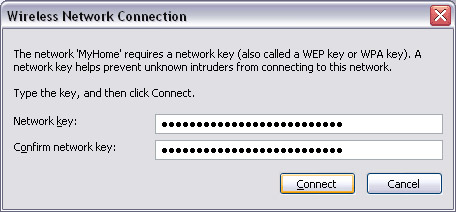
Figure 19: Enter the encryption key (password) to access the network
After clicking OK , your network status will be displayed with the words ' Acquiring Network Address ' then it will change to ' Connected ', see Figure 20.
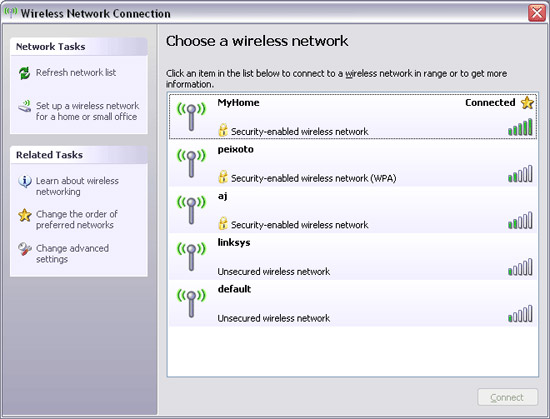
Figure 20: Connected to the network
If you hover your mouse over the wireless icon in the Windows task bar, you will see the word ' Connected ' and the signal strength, see Figure 21.
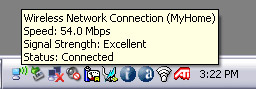
Figure 21: Laptop connected to the wireless network
The wireless network is now 100% active and protected. Here you can read our tutorial on how to share folders and printers in the network to learn how to share shared resources on the network. Don't be afraid of privacy because the encryption feature is enabled and no one outside the network can access it to retrieve your data.
Advanced configurations
Each router has a number of different advanced configurations. Therefore, it is not possible to introduce all the options available in all routers currently on the market. So we will only list one of the most interesting options available in most wireless broadband routers on the market with some examples of use cases. In these subsequent examples, we will continue to use the D-Link DI-524 router above.
• Lock Internet access by time and day of the week : This is a very interesting configuration for both home and office users. Home users can allow young children in their homes to access the Internet only for a certain period of time (eg 4 to 6 pm) and access the Internet freely during both weekends. . For office users may want to block their employees from using the Internet for some time for many reasons. On the example router, this configuration is done by clicking Advanced > Filters , selecting ' IP Filters '. Then it is necessary to configure the IP address for the computers that want to lock (enter * will lock all computers) and the range of ports (ie service types like web, email, FTP, import * for all computers). service). Then select ' From ' and set the day of the week and Internet hours to be disabled for the computers we listed.
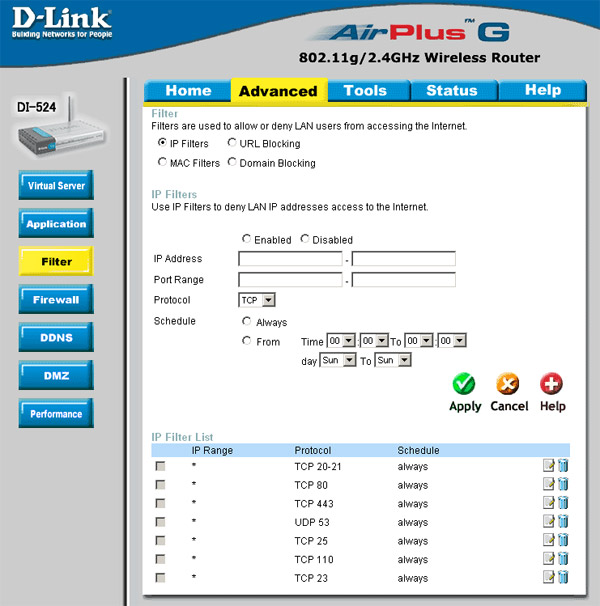
Figure 22: Internet access lock by time and day of the week
• Access to certain websites : You can block children in the house or employees from accessing certain websites. In this example, this is done on the same screen above, but you must select ' domain blocking '. In addition, this example's router also has the ability to block certain websites based on keywords (for example, words like 'sex'). This feature is also configured on the top screen but select ' URL blocking '. You can also configure the opposite of what we just said, which allows users to access only configured websites and block all other websites.
• Configure online games and applications that are accessible via non-standard ports : the router's firewall blocks any connection to non-standard ports. Some programs, especially online games, peer-to-peer file sharing and IP voice use of non-standard ports will not work because the router will block them. What you need to do here is 'open' the ports that are used on each of these programs. You need to know which ports are used by TCP and UDP protocols to configure them. This information is listed in each game's user guide or program documentation. In our router, this feature is configured in Advanced > Application , as shown in Figure 23. Let you have more knowledge about creating peer-to-peer programs working on the network using a broadband router, We have decided to introduce you to this issue in the following article.
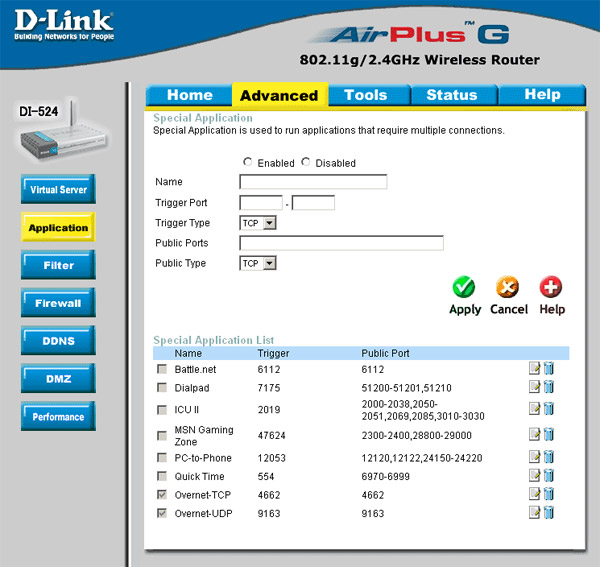
Figure 23: Allow programs to access non-standard ports
• Remote management : You can manage the router to allow people outside the network to access the router's control panel. This option should be disabled but there are also some interesting uses for this feature: if you are a person responsible for network configuration and want to access the router from outside the network. Some technicians use this feature to configure their client network without sitting at the office. To increase security, you can allow remote management with only one IP address, possibly your home IP address, so no one else can access the control panel. In our router, this feature is configured in Tools > Admin , under the Remote Management field. If you do not use this feature, you should disable it to prevent hackers from accessing the control panel from the router.
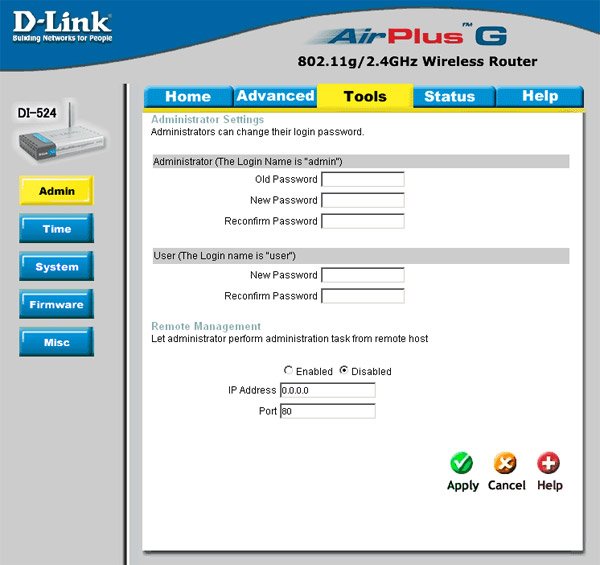
Figure 24: Remote management
There are also a number of other features that can be very interesting to each person's situation, we only list the most common things that a typical user might need. Don't be afraid to explore your router control panel to learn all these options. You may find interesting and useful options for your own situation.