10 ways to surf safely in the business
QuanTriMang - In the Internet 'jungle' area, some useful tips for businesses can avoid becoming prey into the trap of predators. They trap us with phishing scams, download drive-by and malware.
Browsers, Java, Javascript, HTML5 and plug-ins like Adobe Flash allow us to use a lot of applications, but this is also a great door for cyber criminals to attack us.

Any technology has defects that are likely to be exploited. Therefore, the browser, often referred to as a global application, is considered a 'pipe' of malware into the enterprise environment. The truth is, malware and their threats are growing along with the needs of cyber criminals and black hats. Along with that, browsers have unfortunately become a specific target. Sadly, history shows that this trend of attack has only increased without decreasing. Even though there has been a revolution in security features, the browser is still a top target if you still haven't paid attention to this issue in an enterprise environment.
However, you can still improve browser security by making some changes to users, technology, and methods. We will no longer be the bait for piranhas or the tiger tiger snacks, but we can protect ourselves in the Internet 'jungle'. Here are the top 10 tips to improve security when browsing the web.
1. Overall patch management
Patch management is not something new, but it is rarely done in a holistic, comprehensive way. Most companies do this very well when patching the main operating system, but sometimes they miss out on web-related technologies like Adobe Flash and Reader, Apple Quicktime and Java. Overall management of patches includes the entire desktop application and 3rd party applications, including browsers and related plug-ins.
If the complexity on the desktop is not enough, consumer technology (many users bring their devices to the company) will introduce new threats to patch management and security. Although the operator wants to use a new tablet or a user who wants to use old and vulnerable browser-based smartphones, in any case we still have to keep the patches up to date. . A comprehensive and tight patching effort will be very helpful in preventing many different threats. Obviously, this is not a panacea and you cannot cure zero-day errors, but when you do what you can, you still have the ability to minimize risks and costs.
2. Close the browser
Despite being a follower of open source software like Mozilla Firefox and Google Chrome, I will still focus on the security of the browser with the center being the browser that is gaining the most market share today: Microsoft Internet Explorer. All parameters using the current browser show that the Explorer is still being used the most. Besides, because Microsoft is still dominating the field of desktop computers, Explorer power is even greater.
Microsoft has taken a number of steps towards enhancing Internet Explorer security, many of which are in Active Directory through Group Policy. Active Directory is not only an address book service that provides authentication and authorization for Windows domains, it also manages security policies in the Windows environment. Group Policy allows administrators to centralize Internet Explorer configuration, thereby closing all browsers completely.
Internet Explorer versions 8 and 9 provide about 1,500 installation configurations, so you can hardly say that it is not flexible enough to meet your security needs. For enterprise-specific use, the browser features user interface management by disabling some menus or configuration options - adjusting the security area (allowing users to set trust levels - trust - which the application or browser needs to have); install smart screen filter (help protect against software or websites containing malicious code); use Active X control and filtering (providing manageable add-ons); manage and block downloads, .
3. Filter Proxy with the ability to scan malware
As a secondary security layer and as part of an extra depth of security effort, a filtering proxy with the ability to scan malware will be the perfect choice. Businesses provide products such as centralized threat management devices and dedicated filtering proxies with advanced Layer 7 filtering and malware scanning capabilities.

These devices allow you to have an extra tier of applications that monitor traffic to your business; combined with URL address blocking, malware scanning and improved recording features. This helps reduce overall costs as well as speed up implementation.
4. Develop anti-malware capabilities
Anti-malware has evolved from simple signatures and technology patterns to including diagnostic and action-based functions. This is the right direction to develop in the period of many dangers on the web today.
Features such as detecting URL addresses containing malicious code, advanced firewalls right on the client, detecting unauthorized intrusion into hosts, quarantining and allowing applications to black / white lists are now supported. widely. These anti-malware methods will add an active defense layer to the weakest points in the enterprise environment. The anti-malware application you use needs to support these core features and other management tools. If not, you should add it now.
5. 'Take care' of mobile devices
Smartphones and tablets are increasingly present in business environments. Along with that, malware also follows these devices into your company. Top devices such as Google Android and Apple iOS have shared security issues and we can only expect this to continue. Network management and system managers do not have the same management or security features on mobile devices as on traditional desktop computer operating systems. Users can easily be tricked into downloading malicious code, phishing or other phishing techniques right on their mobile device. This happens when the device lacks a protection method provided by the same powerful security and browser protocols on the desktop computer.
Apple needs to act more than just claiming its software is always safe and assumes no need for any malware. Similarly, Google also needs to focus more on unnoticed markets. Honestly, both companies need to work harder to improve security. Currently, 3rd party management applications for Android and iOS are doing a great job of providing management capabilities and increasing security.
6. Policy creates good passwords and authenticates with 2 elements
Free password-breaking tools and knowledge are currently in existence. Therefore, passwords and policies that create your passwords need to be strong enough to discourage hackers. At any time, your password policy needs to include the full range of password, complexity, and age requirements (password expiry date).
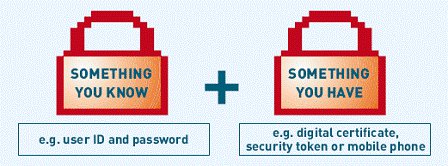
Validating by two factors is often a good choice, but it is often not very complicated and expensive. For those who use a traditional password, browser protection with password management can help prevent users from being shown important passwords. However, a sad thing is that such things still happen. For password management issues, there are many applications that are capable of doing this, some are built into the browser and others are created by third parties. Some of the best names are RoboForm, LastPass, or KeePass open source application.
No matter where you use your password, strong policies are always the best idea
7. Regularly ask users to participate in security training
While many companies have focused on end-user security training, this is still a global affair. However, users play an important role in protecting information - a safer and more secure environment will be set up by well-trained users. Security training for end users should be carried out regularly because threats are constantly evolving. At least, the annual training will help users remember and improve their skills in dealing with the latest hazards. A high level of employee security awareness will be a great asset in fighting many current dangers.
8. Policy and proper method
The correct computer security policy will help users understand how they should and should not use the source of information.
Users should read, accept and sign confidential policies. Methods should be given to users to understand their role in ensuring business safety. Policy and method should be 'reviewed' during the training process so that users are alert and attract them to do it voluntarily.
Bringing such policies and methods into daily end-user training can give them a background in security risks and how they respond properly when faced with them.
9. Minimum right
It's hard to imagine, but some companies still run desktop computers with admin rights. To avoid ongoing requirements when installing or configuring software, IT teams sometimes allow users to install all they want.
End users often lack the expertise needed to detect malware, so they often fail to find them. In addition, internal threats are also very practical and by running desktop computers like that, you are like challenging security risks.
To minimize the potential dangers that web-based malware is targeting, users should only get the minimum number of permissions needed to cater to their daily tasks. Reducing decentralization is a simple task that can help better security.
10. Comprehensive defense
Don't be 'lulled' by false security warnings that many security software offers. Without any service, product, action or effort is enough to get comprehensive security.
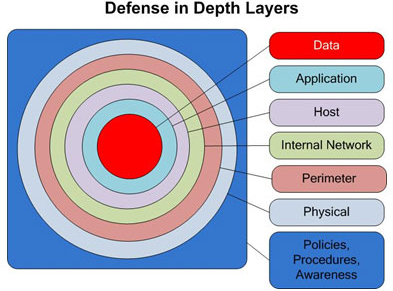
What is needed is a comprehensive, appropriate effort to minimize harm by using the above methods - good security habits that you should learn. Security is not a simple solution like point-and-click, it is a continuous, varied, repeating process that requires coordination.
Although the above 10 methods are just one of many effective methods we can introduce to you in this article, but they are still a step to form the right direction. Technology alone is not enough for your company to be safe, but having a comprehensive view of security will help reduce the risks of infection through the web. With malware on the web, cloud computing and portable devices still growing and growing, there's no reason to say that the dangers will soon be eliminated.
Your company cannot be a 'paradise' containing malicious code, Javascript containing malicious code, bug plug-ins or other browser-based exploits. Therefore, you will have to 'tame' the browser or at least make it safer. In addition, deploy a comprehensive defense system, thoroughly investigate the dangers on the web and ultimately enjoy a less hazardous environment.