What is Website Traffic Fingerprinting? Is it dangerous?
Browser Fingerprinting is a technique that helps websites know who is accessing them. Website Traffic Fingerprinting or traffic fingerprinting is a similar approach. It allows third parties to snoop on you and learn what you do on the Internet. The following article will explain more about this.
Website Traffic Fingerprinting
Website Traffic Fingerprinting is a method for determining when and what users do on the Internet. The user in question may be using a proxy or VPN tunnel that is secure, encrypted, etc. However, it is still possible to determine his or her internet usage through tracking the packets that move through. back on the Internet.

Even the TOR Network (The Onion Router) says criminals can decrypt what is being done by users. In its blog, TOR says that, when data is encrypted and sent, we all know there are a lot of nodes in the TOR network so that a third party cannot track users.
But then, the fingerprinting of the website shows up. Also for TOR, data packets are vulnerable until they reach the first node in the TOR network. This information can be easily obtained. If authorities or criminals set up multiple nodes on the TOR network, there is a high chance that data will pass through them. When such things happen, information about where the packets are going is revealed.
But Website Traffic Fingerprinting is not just a matter of TOR browser. It is also related to how people snoop on what you are doing on the Internet and how they use that information.
What motivates Website Traffic Fingerprinting?
According to TorProject, the exact motive for this attempt is usually not specified, but there seem to be 3 possibilities:
1. An adversary is interested in blocking specific patterns of censored website traffic, while leaving the rest of Tor-like traffic unimpeded.
NOTE : You can replace the TOR with any other encrypted traffic.
2. An opponent is interested in identifying all users who visit a small group of targeted pages.
3. The other party is interested in recognizing each website that a user visits.
How website Traffic Fingerprinting works?
Website Traffic Fingerprinting, or simply called traffic fingerprinting, works on the client side. Snoopers study the data packets entering and leaving a website. As mentioned earlier, it could be just a marketer interested in knowing what type of website gets more views, or maybe an organization that wants to track your moves, right away. even if you use a proxy, VPN or other form of secure browsing.
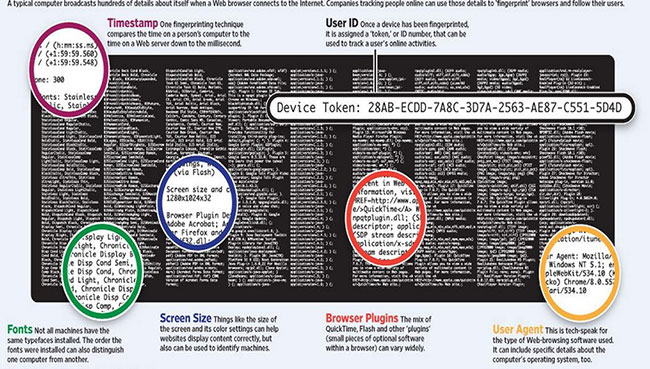 The way the data leaves and enters a web page tells a lot about what is being viewed
The way the data leaves and enters a web page tells a lot about what is being viewed
The way data leaves and enters a web page says a lot about what is being viewed, written to the buffer, or being downloaded. If the data packets are large and the bounce interval is too high, that indicates that the user is on some video site.
Likewise, if the data packets are quite small and the user leaves the site after a very short amount of time, it could be an email website or someone is simply reading a web page.
Based on these, one can understand what is going on. But unless the encryption breaks, otherwise they cannot know about the specific data being transferred.
Dangers of Website Traffic Fingerprinting
The only deadly danger is Website Traffic Fingerprinting that can reveal your identity. It won't steal data in any way, if you're using a VPN or other form of encryption. The main purpose is to know information about the users and their interests on the Internet.
This method is mainly used for encrypted packets to check if something illegal is doing or not. It's hard to think of how it could be used for anything else. Therefore, no need to worry if you are using encrypted connections.
You should read it
- ★ Learn AZ from Direct Traffic on Google Analytics
- ★ 47 steps to increase keyword rankings and website traffic effectively and sustainably over time
- ★ OS X 10.9 appears more on the Internet
- ★ How to Ride a Bicycle in Traffic
- ★ The Ultimate Link Building Guide: Tips and Strategies for Driving Traffic to Your Website