L2TP (Layer 2 Tunneling Protocol) price?
Here is everything you need to know about the L2TP protocol.
What is L2TP?
L2TP stands for Layer 2 Tunneling Protocol, and like the name implies, this is a tunneling protocol designed to support VPN connections. Interestingly, L2TP is often used by ISPs to allow VPN operations.
L2TP was first introduced in 1999. It was designed as a successor to PPTP, developed by both Microsoft and Cisco. This protocol uses different features from Microsoft's PPTP protocol and Cisco's L2F (Layer 2 Forwarding) protocol, then improves on them.
 L2TP stands for Layer 2 Tunneling Protocol
L2TP stands for Layer 2 Tunneling Protocol
How L2TP works
L2TP Tunneling starts by connecting LAC (L2TP Access Concentrator) and LNS (L2TP Network Server) - two endpoints of the protocol - on the Internet. Once that is achieved, a PPP link layer is activated and repackaged, which is then passed through the web.
Then the PPP connection is initiated by the end user (you) with the ISP. When the LAC accepts the connection, the PPP link is established. Then a vacant position in the specified network tunnel and the request is then routed to the LNS.
Finally, when the connection is fully authenticated and accepted, a virtual PPP interface is created. At that time, the link frames (the unit that transmits digital data in the computer network) can freely tunnel. The frames are accepted by LNS, then discard the L2TP encryption and proceed to treat them like normal frames.
Some technical details about the L2TP protocol
L2TP is usually paired with IPSec to ensure payload of data.
When paired with IPSec, L2TP can use up to 256-bit encryption keys and 3DES algorithm.
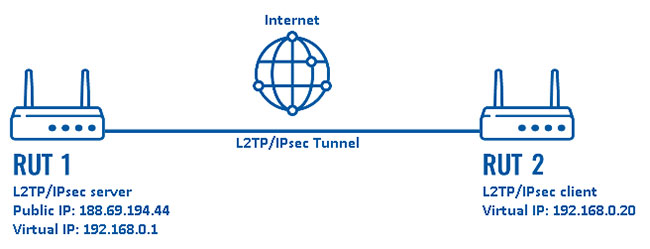 L2TP is often associated with IPSec
L2TP is often associated with IPSec L2TP works on multiple platforms and is supported across Windows and macOS devices and operating systems.
L2TP's dual encryption features provide better security, but also means that it uses more resources.
L2TP usually uses TCP port 1701, but when it is paired with IPSec, it also uses UDP ports 500 (for IKE - Internet Key Exchange), 4500 (for NAT), and 1701 (for L2TP traffic).