The truth about the automated process of running CTFMON.EXE
Many computer users have "scratched their heads" with the process of automatically running the name "ctfmon.exe". What is that?
Searching Google with the keyword "ctfmon.exe", you will get hundreds of results with different opinions about the process. The opinions are focused on two directions explaining that this is a process of Office software or a trojan. Indeed, there are up to two "type" ctfmon.exe that all have the same file icon.
Type 1 : This is an Office suite service that launches Alternative User Input Text Input Processor and Office Language Bar . This service monitors user input to provide appropriate input methods such as voice, handwriting, and keyboard. The ctfmon.exe process will be installed with the Office suite when you choose Alternative User Input in Office Shared Features . To disable this process, do the following (apply to Windows XP Professional): Go to Start -> Control Panel -> Add or Remove Programs , click Microsoft Office and select Change , in the window that appears, you highlight Go to the Choose advanced optimization of applications box and click Next . In the next window, navigate to the Alternative User Input section of Office Shared Features, click and change the icon to an X (Not available) and then select Update .

Then go back to Control Panel, select Date, Time, Language and Regional Options -> Regional and Language Options , click on the Languages tab and click Details , in the Text Services and Input Languages window, click the Advanced tab and highlight Select the Turn off advanced text services box , click OK . So ctfmon.exe "type 1" is gone!

Type 2 : This is Vb.AQT trojan (some other names like FakeRecycled.AQT! Tr , Recycled.20480 ). After being activated on the computer, it will perform the following "nefarious behaviors":
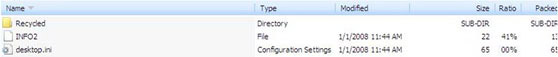
- Create the following folders and files on storage devices such as floppy disks, usb, hard disks:
[Drive name]: autorun.inf
[Drive Name]: Recycleddesktop.ini
[Drive name]: RecycledINFO2
- Create a copy of itself in [Drive Name]: RecycledRecycledctfmon.exe
- Create ctfmon.exe and desktop.ini files in the Windows Startup folder
- Perform the same actions as above but with another folder name is RECYCLER
This Trojan is extremely intriguing in that if you double-click the fake Recycled folder, you will be directed to the real Recycled folder right away. To see the "inner nature" of this directory, you have to use another trick: install compression software like Winrar, Winzip, open the corresponding drive, right-click on the Recycled folder (you must choose Show hidden files and folders and uncheck Hide protected operating system files in Folder Options to see this folder), use the command Compress to . on the context menu to create a compressed file from the Recycled folder above, at the end open the zipped file and "admire" the contents.
These trojan-infected storage devices will encounter a status that cannot be accessed directly by double-clicking and you must right-click and select Explore . More dangerous, according to information on some informative forums, Vb.AQT trojans can act as a spyware or keylogger to steal personal information of users.
Do not worry! You can easily kill this trojan with three steps :
Step 1 : Use the Windows Search feature with the keywords "Recycled", "RECYCLER", "INFO2", "ctfmon" to determine the path of folders and files created by trojans (remember to check Select the Search hidden files and folders section before searching). The path will be similar to the one described above, you may also find some paths to Windows cache directories like Prefetch, dllcache .
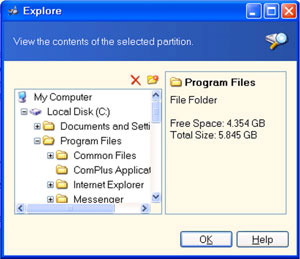
Step 2 : Delete all found files and folders. If an error message cannot be deleted, do the following: Download the iso image file of the boot disk Acronis Disk Director Suite at http://www.fileden.com/files/2007/5/5/1051345 /AcronisDiskDiretorSuite.iso then burn it to a CD, then boot the computer using this disc. In the interface of the program, double-click the drive name and move to the files and folders to be deleted, select and click the X-shaped icon to delete, you can rest assured that there will be no error message at all
Step 3 (optional): Although the above two steps are enough to get rid of the Vb.AQT trojan, you should use antivirus software like Bitdefender or Kaspersky to check again for sure.
(Note, if you remove the above two steps and only use antivirus software to kill, it will not succeed, because often this software only scans and detects, not "handles" the Trojan).
The experience shared above will hopefully help you. If you still have questions, you can email phuc_asimo@yahoo.com , I will be ready to answer.
 New invention makes battery life up 30%
New invention makes battery life up 30% Photo of PC assembly process in factory
Photo of PC assembly process in factory The software will be killed by Vista SP1.
The software will be killed by Vista SP1. SSDs are still ... far away
SSDs are still ... far away Learn Control Panel in Win. XP
Learn Control Panel in Win. XP News about the project code-named Oslo
News about the project code-named Oslo