The Alarming Truth About Router-Related Network Vulnerabilities
Most of the time, your only concern with your home network is whether or not you can access the Internet . However, if you check for vulnerabilities, you may discover some more pressing issues.
Why should you scan your network?
Your home network may include a router that connects all your wired and wireless devices. This setup is known as a SOHO (Small Office/Home Office) network and can have vulnerabilities that hackers can exploit. Attackers can try to access your network in a number of ways:
- Exploit open ports exposed to the Internet
- Target devices on your local network
- Launch wireless attacks
- Attacking remote work connections (e.g., VPN or RDP )
Regularly scanning your network and addressing vulnerabilities can help protect against such threats. Luckily, it's easier than you think.
2 network scanning methods
Pentest Tools
If you are new to penetration testing or want to get a simple overview of your network without having to boot up a Linux server, Pentest Tools will fit the bill.
- Locate your external IP address without using a VPN and make a note of it. You can find your external IP address by searching Google for "what is my IP address" or using websites like What Is My IP? .
- Open Network Vulnerability Scanner on Pentest Tools, copy-paste your external IP address into the Target field and click the Start Scan button .
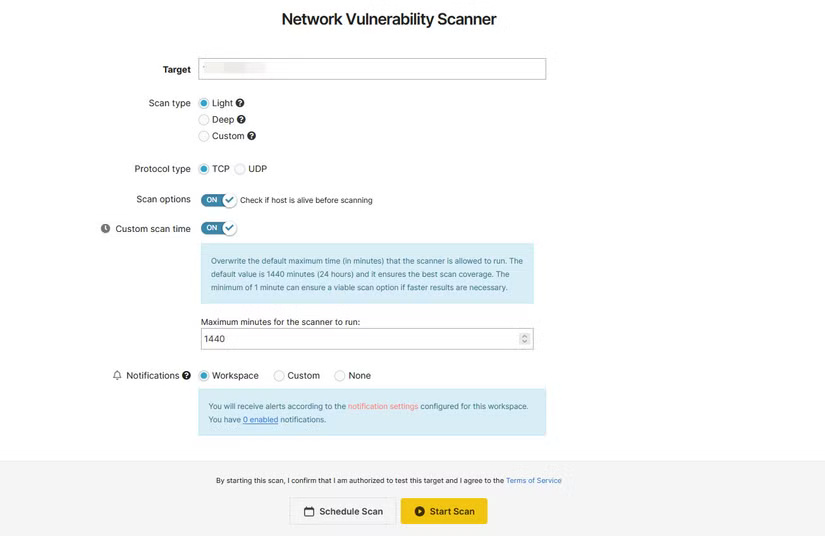
The results page will show you all the network information and open ports that an attacker could glean by scanning your public IP address—a big reason why you shouldn't make this information public. However, the free user's light scan is only useful for finding common ports that might be open on your network by default. Running a deep scan, which scans a significantly higher number of ports, can cost up to $85/month; however, considering that the site still uses Nmap for scanning, you're better off looking into Nmap if you need more in-depth results.
Nmap
If you want in-depth results, Nmap (Network Mapper) is a better choice. Installing and running Nmap requires some technical knowledge, but a GUI version is available for Windows.
- Download Nmap
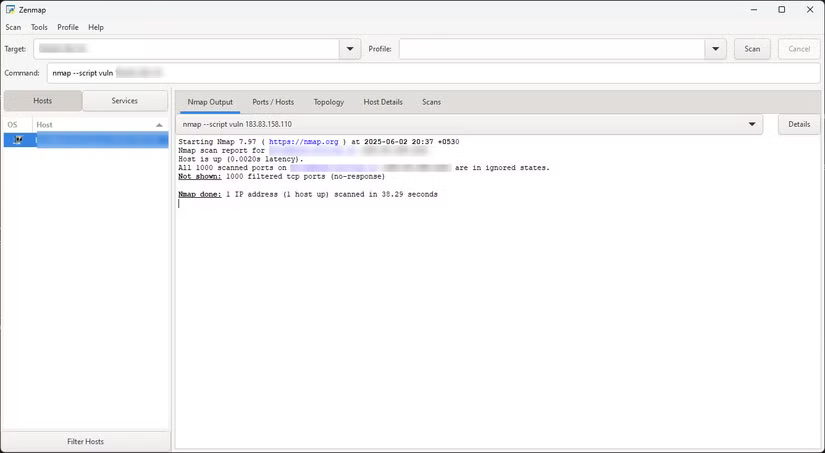
Install Nmap on your Windows, macOS, or Linux device. You can then scan other devices on your home network:
nmap -sT [địa chỉ IP bên ngoài của bạn]This command scans all devices on a typical home subnet for open TCP ports.
However, the best way to run Nmap is through an online Linux server. Running Nmap from an external server allows it to scan your network from the outside, detecting open ports, vulnerabilities, and potentially exploitable services. When running locally, Nmap can scan other devices on the network — such as routers , smart devices, or other PCs — to identify open ports and services. It won't reveal what an outsider sees unless it's run from outside your network.
Once setup is complete, run sudo apt install nmap in terminal to install Nmap. Then, scan for vulnerabilities on open ports:
nmap --script vuln [địa chỉ IP ngoài của bạn]Warning : Running a scan from a VPS means sharing your home IP with a third-party service. Always follow your VPS provider's terms of service and never scan networks you don't own or aren't authorized to check.
Patching vulnerabilities and "hardening" home Wi-Fi routers
No matter which scan you run, you'll see information about your router, Internet Service Provider (ISP), current location, open ports, and if you're using Nmap, any vulnerabilities you might have encountered. Typically, you'll find a list of commonly used open ports:
- 80 (HTTP)
- 443 (HTTPS)
- 53 (DNS)
- 3389 (RDP)
- 22 (SSH)
- 23 (Telnet)
Not all open ports are dangerous, but you should be aware of them. Open ports allow outside services to communicate with software running on your devices, such as PCs, smartphones, Smart TVs , and even your router itself. However, simply disabling all open ports is not a practical solution, as it will hamper your Internet connection.
Common ports like 80 (HTTP), 443 (HTTPS), and 53 (DNS) should be left open. However, if you have any open ports that are used by third-party applications or features on your operating system, such as RDP (3389), SSH (22), Telnet (23), and FTP (20 and 21), you should consider closing them, depending on your network usage.
If you need to open a specific port for any reason, you can hide it from hackers scanning your IP or router for vulnerabilities. Other times, you can open specific ports as needed, then close them to secure your network. There are many legitimate uses for RDP, SSH , Telnet, and FTP, and closing those ports will prevent those protocols from communicating with outside services.
As you can see in the scan results from the previous section, all of the ports that Nmap and Pentest Tools' network scanner tested on the network were closed. More specifically, they were in a "filtered state," meaning the network scanner could not confirm whether the port was open, closed, or filtered.