Techniques for decentralizing Window administration
Derek Melber
Today Group Policy is becoming more important and has more options for delegation. Understanding where to set up permissions and how to delegate certain tasks can help you set up a more secure and efficient network.
Since Microsoft released Windows 2000, the options for assigning certain tasks are always set. Defining decentralization can be a bit confusing, but what decentralization is so important is to increase network efficiency. Without using decentralization, you have the ability to be stuck with only the default groups that allow administrative privileges through certain tasks and objects. For example, when there is no authorization for user accounts and group accounts, the user must be placed in the Account Operator group that can only manage users, groups, and computers within a certain range. Of course, users can also be placed in the Domain Admins group or Enterprise Admins group, but this allows users to have too many privileges compared to just managing accounts. In some similar cases, placing users in the Account Operator group also allows them to have privileges such as modifications not only in their account, but also the administrator account. Solve this problem by allowing decentralization to objects and tasks throughout the system.
Decentralization analysis
If you want the network to be more effectively managed by implementing decentralization, you need to pay attention to the following issues:
1. Who will receive decentralized privileges?
2. What is the assigned user group?
3. Who controls decentralization?
4. Where is decentralization done?
5. What are the privileges for configuring complete decentralization?
If these things are done separately, they will not achieve the best results.
Note first that the standard of creating groups will be decentralized. This way, it is easy to add more users and also easily remove user permissions.
The second note is that not all tasks can be decentralized. Therefore it is necessary to make a list of authorized permissions. We will create these lists later on the tool where permissions are set. Once you have a list of permissions, it is much easier to choose any permissions you want.
For object decentralization, you need to know what you delegate. Do you want others to control the entire user account or just some attributes of the user account? You can also choose from multiple groups, computers, organizational units, or Group policy objects.
One of the most important concepts is knowing the location of decentralization configuration. There are 3 main tools to do this. We will carefully analyze these 3 tools later.
Finally, when activating the tool and want to decentralize, you need to know which "options and dialog boxes" will accomplish your purpose. Some decentralization is quite easy, but others require you to do some checks and evaluations before you can guarantee decentralization.
Active Directory users and computers (ADUC)
Active Directory has a complete and comprehensive decentralized component. If you are not using decentralization in AD, you have missed one of the important reasons when using AD. Authorization within AD allows administrators to configure groups of users to access certain tasks. The benefit of this is that very detailed tasks and reduced administrative controls are limited to tasks that are acknowledged with the user group.
The key to understanding decentralization in AD is to understand its capabilities. Microsoft added a number of options in Server 2003, but there are still a limited number of options that control administrative permissions. Below is a list of main objects configured with authorization controls:
- User account.
- Group account.
- Organizational units.
- Computer account.
Although it lists all the objects that can be controlled, more importantly, it is important to understand the permissions restrictions for each object. In particular, which permissions are appropriate for user accounts, group accounts and computer accounts.
- Reset Password.
- User account management.
- Group management.
- Change team members.
- Add computer to OU.
- Computers have little control . use permissions through GPO.
Some permissions are shown in Figure 1.
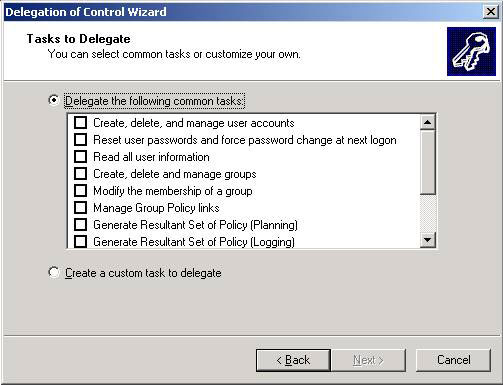
Figure 1: ADUC mandate
Group Policy management control (GPMC)
PMC provides an environment that not only allows administrators of GPOs, but also protects those who can manage those GPOs. Along with the appearance of the GPMC all management and decentralization of GPOs is integrated into this tool. I want to be clear. It is clear that the GPMC only provides GPO management permissions, not other AD management permissions. Therefore, anything similar to the control OU, user, group . must be done in ADUC.
For permissions with GPMC you have the following options:
- Create GPOs
- Edit GPOs
- Delete and securely manage GPOs
- Linking GPOs
- Read GPO settings
Some permissions are shown in Figure 2.
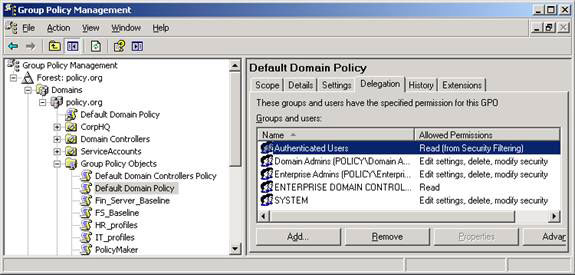
Figure 2: Assigning GPMC permissions to control and manage GPOs
Once the creation of GPOs is made for "domain", there is no mechanism to control an OU. However, you can authorize someone who can link a GPO to an OU, giving you task controls as if you wanted to be authorized at a higher level. Linking GPOs is delegated at domain, OU, or pages. The process of editing, managing, deleting and reading GPOs is decentralized at each GPO, making it easy to control them.
Advanced group policy management (AGPM)
The final model of AD decentralization and GPO is AGPM. This tool provides an important end for GPO management. GPMC is a very good program but it lacks key management features like AGPM. AGPM provides the following characteristics via GPMC:
- Prepare offline GPO.
- Change management of drafting GPOs.
- Archive GPO.
- Automatically backup GPO backups.
Some permissions are shown in Figure 3.
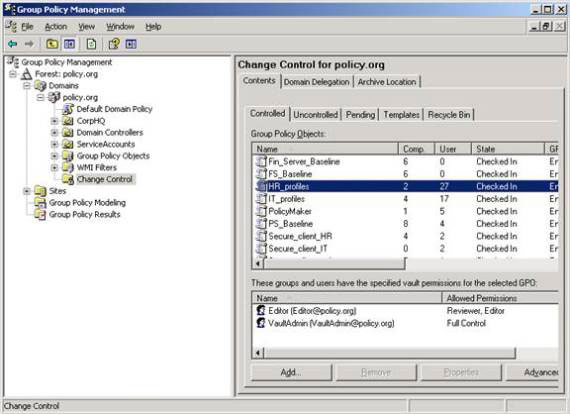
Figure 3: AGPM authorization management options
With AGPM you can assign authority to anyone in the company. The AGPM interface provides a perfect solution that allows administrators to edit a GPO without affecting other computers or administrators.
summary
The three solutions mentioned above are the necessary tools for you to delegate tasks and responsibilities of AD and GPO objects. ADUC provides a solution for AD-related tasks that do not include GPO management. Both GPMC and AGPM can manage GPOs. Combining these tools provides an effective solution for comprehensive GPO management. As soon as you perform decentralization with these tools you will gain an effective management model and ensure that administrators only have the right to modify things in their authority.