Six Rootkit detectors protect your system
Many security suites only have simple basic detection and detection levels. The standalone tools we will cover here perform a "search and destroy" task of rootkits that may be hiding invisible somewhere in your system.
Content of the lesson
• Introduce
• F-Secure BlackLight
• IceSword
• RKDetector
• RootkitBuster
• RootkitRevealer
• Rootkit Unhooker
• Conclude
In October 2005, Windows expert Mark Russinovich announced news that "shocked" the security industry about fraudulent copy protection technology that was seriously damaging. Some Sony music CDs attached to the program are silently loaded into the computer when inserted into the CD-ROM drive. Extended copy protection technology (or XCP) prevents every attempt to scan a disk by dropping a rootkit into Windows with a tendency to destabilize the computer's operation. Not all destructive programs are completely anonymous: Russinovich's RootkitRevealer appears briefly. Long time ago, Sony had mentioned a new kind of security object and the word "rootkit" was entered into the dictionary of millions of computer users.
The concept of rootkits is not something new. It returned with the days of Unix. Intruders can use a common Unix toolkit, recompile, allowing them to administer, owning root access without leaving a trace. Rootkits, as we know them today, are programs designed to hide themselves from both the operating system and the user, usually by executing end-to-end programs around the common API system. Rootkit can be a legitimate program, but the term is often used for activities that have a bad meaning. Most are the beginning of information theft, mainly targeting bank account codes, passwords, important data and sometimes becoming the cause of other types of vandalism.
Many anti-virus software and security software companies have begun to add rootkit detection (at least at a preliminary level) in their products. There are a number of commonly used free, standalone rootkit detection tools. In this article we will provide you with the six most popular standalone applications and their functions. To test, we let applications scan a number of computers with three different rootkit variants built-in: Fu or FuTo, rootkits can "run" into any program; AFX Windows Rootkit 2003, can hide all programs and folders on the system; Vanquish, similar to AFX, but uses a slightly different hidden mechanism.
How they work
 Major search engines work by comparing file lists at each point of the system and see if anything doesn't match. One of the first methods to perform this type of detection is to output a complete file containing all the files in the operating system, then start the Recovery Console component and export the other file list, then Compare them together. If a file is on the second list but not on the first, but not the Windows file to hide by default, it can be an intruder. Recent rootkit detection programs use a number of variants of this method, which do not require a separate operating system to receive usable results.
Major search engines work by comparing file lists at each point of the system and see if anything doesn't match. One of the first methods to perform this type of detection is to output a complete file containing all the files in the operating system, then start the Recovery Console component and export the other file list, then Compare them together. If a file is on the second list but not on the first, but not the Windows file to hide by default, it can be an intruder. Recent rootkit detection programs use a number of variants of this method, which do not require a separate operating system to receive usable results.
These programs are reviewed in a lighter way, with their usefulness in the future: easy to use; how to compile results; How long to update time . Remember, rootkits are like viruses, which are mobile targets. Today's anti-rootkit anti-virus program must also protect you tomorrow against the whole new variant of threats. In fact, many program rootkit creators avoid specific detection by some existing programs.
The most important thing is that these programs target the advanced user level. They are not built for common purposes. It is not always possible to distinguish between false positives (for example, files hidden in an operating system's way) and real rootkits. They do not have any warranty, are only provided in "run" mode, no installation is required. Some of them (such as Trend Micro's products) use core platform technology in a user-friendly version much more than its main commercial product. In short, if you're not an IT professional, the best thing now is to hire a reputable consultant or use a mainstream product line that has some rootkit detection capabilities (like Trend Micro Internet Security ).
F-Securu BlackLight
F-Securu BlackLight is one of the first widely used rootkit scanners (besides RootkitRevealer). Its scanning technology is now used in F-Secure Internet Security 2006. The current version of the program may be temporarily suspended and supported after April's April 2007 fishing day. You can still download and use normally. No official information is available, but it is possible that another version of BlackLight will be commercially available.
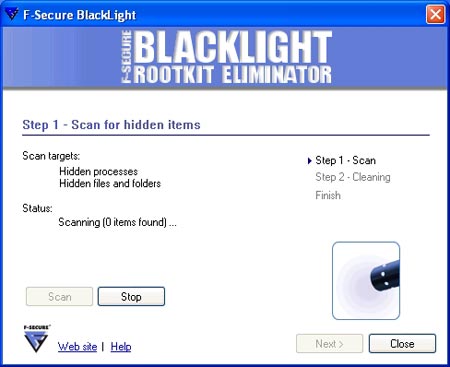
F-Secure BlackLight's scanning technology will quickly be provided as part of commercial products
BlackLight really reminds us of Trend Micro's RootkitBuster, not just the feeling but the core technology. Although they are part of another set, they are the same in features: very easy to use. No options can be set, only the " Scan " and " Stop " buttons. At start-up, BlackLight runs a pre-configured scan mode for both hidden files and hidden programs. But its detection system is quite meticulous. It "captures" the hidden program because the Fu rootkit executes and detects two other rootkits.
The file system scan program only takes a few seconds to execute, even on relatively small systems. You can then call up a list of all running programs and can be detected. You will have to provide an option to delete any detected rootkits in your computer, including renaming infringing files or removing them completely from your computer, forcing your computer to restart.
A minor annoyance to the Wizard-style user interface is that you cannot go back, you can only move on. If you encounter any errors, except on the current page, you must restart the entire program from scratch.
F-Secure also has a user guide and detailed references such as other rootkit detection programs. Even if this program is at the expert level, it is always better to have a clear guide.
F-Secure BlackLight
F-Secure Corp.
http://www.f-secure.com/
Price : free.
Summary : As a time-limited program, it is possible to temporarily pause to switch to F-Secure Internet Security 2006. BlackLight has a thorough scan mode and cleans many of the infringing files on the system.
IceSword 1.20
IceSword is increasingly emerging as the most powerful and thorough rootkit detection tool, although it is also hard to find. Its creator, a Chinese-speaking programmer, has a pif_ nickname, offering this program on his website. But after the link becomes extremely slow, the application is cloned to many other free download websites around the world (such as MajorGeeks.com).
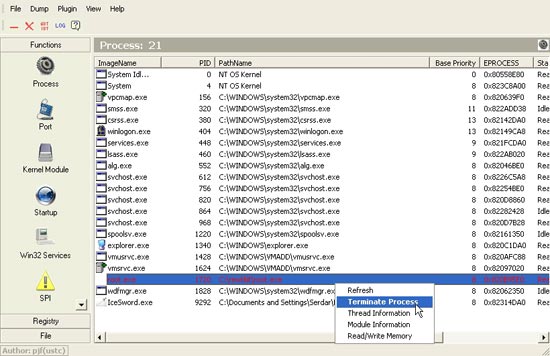
After identifying the hidden program, IceSword gives you the option, either to extract information, or to delete it completely.
The original program itself was only available in Chinese characters, but after being replicated to many other websites, many translated and released the English version (although the Help section is still in Chinese only). Although language is not troubling, you can still get a copy of it with not too much trouble. And the English translation is also quite easy to read.
IceSword performs a number of different system scanning programs and attempts to determine whether any hidden programs are controlling: running processes, starting programs, services, etc. There is a "System Check" screen "all in one", but it cannot explain why it is located at the end of the scan list but not the default. If you run this mode, it will create a fairly concise report on any suspicious activity.
You can drill down into more detailed reports, add information about the infringing program or file and destroy it. You can perform a more thorough deletion if you like. However, there were two problems with the program in version 1.3: when scanning a AFX 2005 rootkit, for example, the program broke it.
There are some small details, making sure that this program is built for professionals. The "Reboot and Monitor" function restarts the computer, then detects if there are any attempts to hide programs or Registry entries during the boot time. "Forbid all process / thread creating" allows you to "lock" the rest of the system when starting a new program, after IceSword has loaded a certain level of protection. By default, you can set IceSword to record the newly created programs and threats log, then analyze the possibility of an intruder.
IceSword is updated quite regularly. The 1.x series versions appeared throughout 2006 and pif_ said he would continue to update, providing new versions of the program with some other outstanding features. The software also has a plug-in structure, which can be used to expand the program. IceSword currently has only one add-on tool, used for low-level disk editing.
IceSword 1.20
www.blogcn.com/user17/pjf/index.html
Price : Free
Summary : It is a bit difficult to find the author but has a high efficiency and continues to be updated with some smart pro level components.
RKDetector 2.0
RKDetector actually has two applications: one for scanning hidden files on the hard drive and one for scanning hidden programs, kernel hooks (links in the operating system kernel). To perform advanced scanning in this software a bit difficult. You must perform a partial scan separately, but there is no way to get a consolidated report. Individual results are not hampered by the main function of the tool, but its usefulness is overshadowed by some of the other applications discussed here.
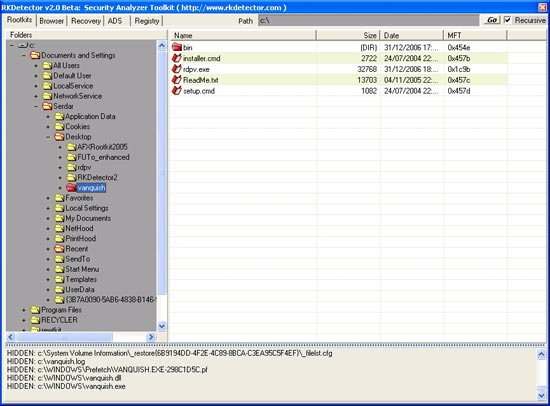
RKDetector scans individual files and programs;Its interface is not clear.
The main program consists of 5 tabs: Rootkits, Browser, Recovery, ADS (to scan alternate NTFS data streams, where rootkits can hide), and Registry.
Before scanning any object, you must provide a root path to know where to start scanning (eg C :), not just click Go or press Enter. The Rootkit tab is the best place to start and often returns the most results. Folders with hidden files will be highlighted in red. If the files are found to be hidden but are not legal because the operating system executes, it will be marked with a deep red. One drawback is that if rootkits hide some folders and not a single directory, you'll have to manually detect the relevant directories. This can be very frustrating.
After finding the infringing file, you can: export it to the file itself or point to the MFT table, record it or delete it safely (the MFT entry is also deleted). The program uses US DoD 5200.28-STD "secure erase" algorithm to make sure the file is completely removed and you can use it with a bit of caution.
It is not very impressive with the RKDetector detecting the hidden, hook analysis program. It can't find a program in memory that is compromised by Fu's rootkit.
RKDetector 2.0
www.rkdetector.com
Price : free
Summary : Includes two separate applications that scan file systems and programs that run separately. RKDetector has no flexibility and many components like other programs.
Trend Micro RootkitBuster 1.6
One of the most interesting points at Trend Micro is that they often create gifts from their own commercial products. If you are infected with a virus, you can use their online antivirus tool to "scan and clean". With the same rootkit, Trend Micro has split the rootkit detection technology in the commercial Internet Security 2007 product into a free standalone tool for users. The documentation section is almost unavailable, and it is impossible to know if the product has been updated regularly. But if you've got it in your hand, you'll probably always carry it.
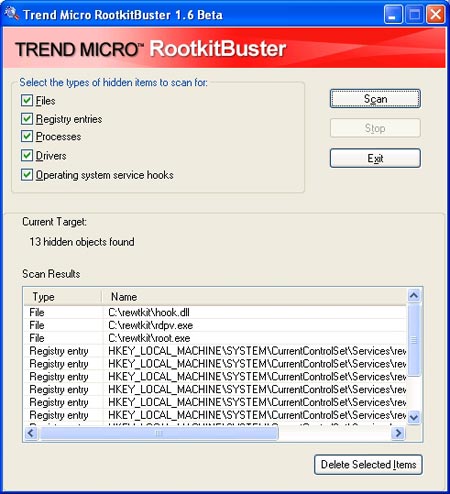
Trend Micro's RootkitBuster doesn't have many options, but the scan tool is quite perfect
RootkitBuster does not work badly. The program can run immediately without installation and scan five areas: file system, Registry, running programs, hard drive and operating system level service hooks. Results are automatically written to the log file. If any file is found to be infringing, you can choose to delete it (and force the machine to reboot to make sure the file has been deleted).
For some reason, RootkitBuster does not scan the list of default service hooks. But there is an option to control this function for users in the "one and only one" interface of the program. So this is not a big deal. (This option is not set by default to cut the total scan time, since most rootkits are classified into four different categories.)
This application has a slightly faster scan speed, but much less information about detected problems than IceSword or Rootkit Unhooker. RootkitBuster does a good job of searching and deleting. It "caught" the programs hidden by Fu rootkit and found two other pretty test rootkits. All three are deleted just by clicking a button and restarting. However, the suspicious files will not be deleted if RootkitBuster determines to protect itself against the damage of rootkits, which it finds should not work.
Trend Micro RootkitBuster 1.6
Trend Micro Inc.
www.trendmicro.com
Price : free.
Summary : Independent version, "promotion" of rootkit scanning technology separated from Trend Micro's commercial product. Operation is actually quite effective.
RootkitRevealer 1.71
RootkitRevealer 1.71 (RKR) is one of the first rootkit detection tools by Mark Russionovich and Bryce Cogswell of Winternals (now part of Microsoft). It is limited to a certain extent although it is updated quite often. The most recent version was released in November 2006 in the United States. Russinovich and Cogswell are Windows technical experts in the branch. This rootkit detection application will continue to be updated, at least for the time being.
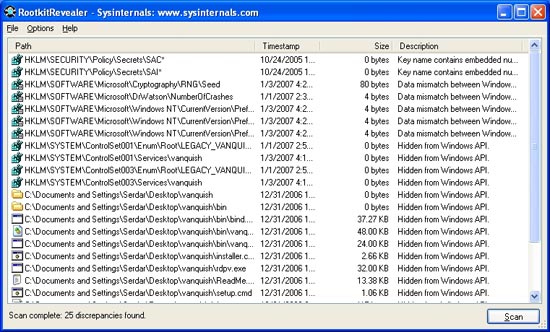
RookitRevealer only scans the hard disk, not the memory.But the hard drive scanning mechanism is really strong.
RKR is quite simple to use. Just open it (no installation required), click "Scan", it will repeat through the Registry, the file system to find any infringements from the operating system. The program will issue a number of false error messages by default, mostly in the Security field of the Registry, annotated in detail and easily ignored.
The results are displayed in the open report, but no action can be taken to handle the elements detected in the program itself. For example, you cannot right-click on a suspicious file and delete it. If you want to have an operation you have to do it completely in a different way, which can be difficult if you have to handle a file or program that is legal.
RKR's documentation points out that it is not designed to detect rootkits that are self-muting in memory like Fu (it cannot find this rootkit). The program will check each section specifically to see if something is trying to intrude on the file system or the Registry. In this respect it is limited.
This application can detect signs of two other rootkits, which is not bad. But for advanced scanning and the ability to define more operations before rootkits, RKR is not as responsive as many other applications.
RootkitRevealer 1.71
Winternals Software LP / Microsoft Corp.
www.microsoft.com/technet/sysinternals/utilities/RootkitRevealer.mspx
Price : free
Summary : one of the first rootkit detection tools, now overshadowed by many better programs, but still works relatively well.
Rootkit Unhooker 3.0
Like IceSword, Rootkit Unhooker has no exact origin. It is the product of a group of programmers from Russia, but better and more advanced than the programs that have been mentioned. It also means that it is much more complicated, but programmers help users more easily understand by a single report all scans of the program.
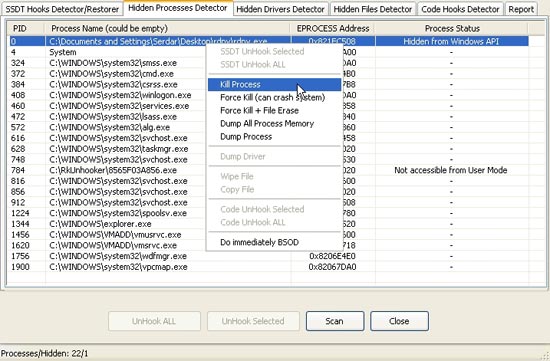
After detecting a hidden process, Rootkit Unhooker lets you kill the intrusive program and is even safer than deleting it.
When run, the program will perform integrity checking to ensure that it is not corrupted by a rootkit. Rootkit Unhooker has retained one of the rootkits used to test and provides more detailed information and allows users to completely erase this rootkit.
Rootkit Unhooker has six tabs for each active area: kernel hook (links in the operating system kernel), hidden programs, hidden drives, hidden files, code hook and a full report tab . You can click "Scan" on each tab to scan for specific types, or go to the overview report tab to scan them all at once, which can take a long time. The full report is usually quite lengthy, but it should be clear if you catch a rootkit. This tool allows the presence of all three rootkits to be checked without problems.
If you find a suspicious or intrusive program, you can: usually end it, force the program to close, delete files or some other combined activity. If you have deleted, delete one or more files, you should restart the computer or follow a "manual" way of another program to make sure the problem has been rooted. If you are still unsure, you can force a BSOD to stop running all unnecessary files. The most attractive single component is "Virtual Machine Detector", which uses a short time between two CPU commands to determine whether the operating system runs directly on a PC or in a virtual machine. (At least, a theoretical rootkit is designed to "wrap" the victim's operating system in a virtual machine).
Rootkit Unhooker is updated quite regularly (5 times from November 2006). Although some of its prompts are clumsy in English, the language does not reduce the program's usefulness and functionality. The help file is very coherent and coherent.
Rootkit Unhooker 3.0A
UG North
www.rku.xell.ru/?l=e.mspx
Price : free
Summary : The most advanced and powerful Russian-originated tool among the tools tested here.
Conclude
The rootkit detection tools we introduced here are divided into two basic categories:
1. Tools are written professionally, mostly as a marketing way for manufacturers' commercial products.
2. The author's tools are independently and widely available.
Ironically is one of the independent author's tools, Rootkit Unhooker is rated the best. I don't know if big companies see this as a competitor, but the independent tool is now more chosen by experts.
Rootkits continue to multiply and grow constantly, becoming increasingly difficult to detect. Whether it is a new security software manufacturer or independent tool writer, an ongoing effort to update and update the tools is always done. As for us, take advantage of useful free versions and contribute ideas to them to continue to get better products.