Office security with Microsoft Office (Part I)
The recently discovered vulnerabilities of the Microsoft Office suite give us the need to understand the security architecture of MS Office and vulnerabilities to exploit. In this article we will talk about Microsoft Office's OLE (OLE Structured Storage) storage mechanism, the natural appearance of recent dropper programs and some other destructive agents. This article is in an effort to study the operation of some MS Office mining programs. Part two compares and examines a number of ways to investigate law through different MS Office components. Both sections provide typical examples of different MS Office vulnerabilities, their natural development and how to exploit those vulnerabilities.
1. Overview of recent vulnerabilities of MS Office:
MS Office vulnerabilities cause a lot of concern for users, especially when they receive MS Office versions from e-mail or download from websites.
It has been discovered that some errors cause memory corruption or buffer overflows, some other errors affect privileges. All of them make the victim's machine damaged or partially affected. The approximate number of vulnerabilities in different MS Office is inversely proportional to the number of vulnerabilities, so far, we can see on the following diagram:

Figure 1. Overview of MS Office vulnerabilities msoff1-thumb.jpg
Looking at the ' Remote Code Execution ' column, all holes have different levels of risk. These are also the most dangerous vulnerabilities for the system, compared to DOS (Denial of Service) and Memory Corruption attacks, the following two types of attacks only cause level medium danger.
Vulnerabilities are available in all different MS Office application programs, as shown in Figure 2 below. You can see an overview of the incidence of vulnerabilities in MS Excel, MS Word and MS Powerpoint.

Figure 2. Distributing vulnerabilities in MS Office applications
Each column in Figure 2 shows the number of vulnerabilities in specific applications, but the MS Office column is not a combination of all three columns. It shows the number of common vulnerabilities affecting all MS Office applications. The following section will help you better understand some of these vulnerabilities.
2. OLE Structure Storage (OLE structured storage)
One of the earliest vulnerabilities of MS Word discovered this year, was exploited with the help of dropper programs embedded in the file structure of MS Word files. Several vulnerabilities relate to anomalous images and media objects in MS Office. First of all, you must understand the concept of OLE Structure Storage - MS Office file storage structure.
In this article, OLE Structure Storage is defined as a systematic organization of MS Office text components. Each text has a root including storage and stream components. The OLE Structure Storage is synonymous with the file system structure, such as the storage corresponding to the directory, the stream corresponds to the file, as shown in Figure 3 below.
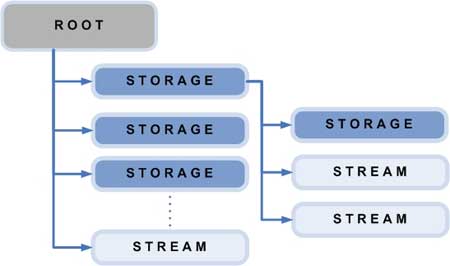
Figure 3. OLE Structured Storage.
The storage component can exist independently. Each component has parts for storing children and offspring. The root component also has lines directly inside it. Office 2000 and its later versions support both file format: basic OLE binary and basic XML. Both are structured forms of storage. In later versions, there is also a browser-friendly option for archived documents. Figure 4 shows the OLE Structure Storage diagram, taking an example of a Word document structure.
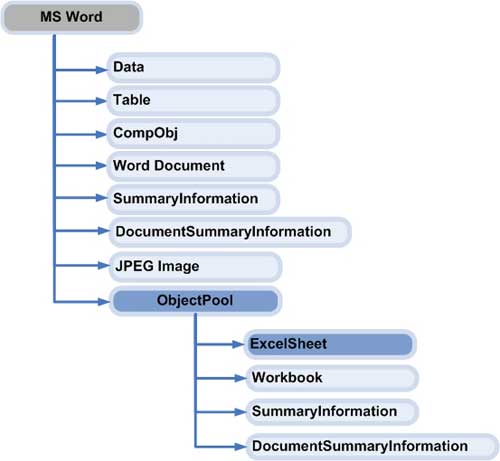
Figure 4. Example illustrating the Word text archive format
The 'MS Word' component is the original, containing several streams and a storage. Different parts of text such as real content, inserted tables, CompObj combined with DLL files for objects, Summary Information summarizes content, images and Document Summary Information; all are left in the form of streams below the original element. ObjectPool is the common repository of all child storage components. The figure above also illustrates the child storage component pattern in Excel. Excel spreadsheets are a storage component within ObjectPool and have separate information lines (Workbook, SummaryInformation, DocumentSummaryInformation).
Other MS Office files are similarly structured. It is possible to embed some other objects in the text style. They are also accessed, updated from the corresponding stream or storage components. Some COM and OLE vulnerabilities allow escalating privileges and lack of appropriate input information filtering, hurting the system using MS Office applications.
3. An example of the operating mechanism of an attack
With a normal attack, the vulnerability is exploited simply by inserting an unusual or malicious object into the text structure. Some vulnerabilities in MS Excel and MS Word are affected by this type of attack.
Alternatively, it is possible to insert malicious objects with Microsoft Word Malformed Object Pointer Remote Code Execution Vulnerability. This type of attack is illustrated in Figure 5:
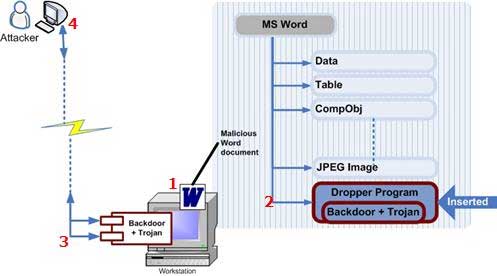
Figure 5. Exploiting the heterogeneous object pointer vulnerabilities
Steps in the mining process:
- Step 1 : Lead the victim to open a malicious MS Word document via an email attachment or a web page.
- Step 2 : Execute the malicious storage component (the dropper program) inside the OLE Structure Storage structure as an open Word file.
- Step 3 : Trojan is released into the victim's system
- Step 4 : The Trojan works with a backdoor, allowing remote attackers to gather system information, access commands and capture the screen interface and store them in the % System% folder. Capture.bmp .
If we thoroughly analyze the process of exploiting the vulnerability above, we can divide it into more steps.
In that first step is to outline or create a malicious Word document. The OLE Structured Storage structure does not have the ability to verify storage component content and allows execution like Trojans. Therefore, it is necessary to create malicious Word documents with external camouflage as one with innocent cover.
The second step is to lure the victim to open the malicious Word document via an e-mail attached or download it from a website.
The third step is to use the malformed object pointer, allowing the malicious storage component to execute immediately after the word document is opened. The attack process achieved initial results, the Trojan started taking action.
The fourth step is to help the embedded 'Trojan' install a backdoor, to help the remote attacker execute certain programs on the victim's machine and eventually destroy it.
3.1 Dropper programs:
Dropper is a program designed or modified to 'install' malicious malware (such as Trojan, worm or backdoor) on the target system. Malware code is often in a dropper in the way that virus scanning programs cannot be found.
A Trojan dropper typically extracts all its files into folders and executes all of them simultaneously. Dropper programs are rarely caught by antivirus programs or vulnerability detection programs. That's because:
- The dropper programs themselves are not malicious but contain only the source code for dropping malicious content into the victim's system.
- In many cases, Trojan dropper contains non-malicious multimedia files to hide malicious activities inside.
- Sometimes the dropper program overwrites the source code on a malicious MS Office document with a "clean" copy of the document itself. And this way does not leave a trace.
- In many cases, Trojan droppers extract programs directly on memory and activate them right there, making the antivirus software unable to find the malware released.
Some other vulnerable vulnerabilities of MS Office are due to inadequate input data filters; the grammatical capacity of incompatible OLE Structured Storage functions; the validity of the stream component variable is unreasonable (because of buffer overflow, for example); disconnect memory; the return of OLE Property Set collections fails .
Discussing each of the vulnerabilities in detail is beyond the scope of this article, we can only give some comments about them. Most require an assessment of the nature of the MS Office document before it is opened. This is increasingly difficult when anti-virus software is always fooled by exploiting agents like the dropper program. The only solution is to manually adjust the OLE Structured Storage mechanism.
While many vulnerabilities are addressed in the Microsoft Security Bulletins, many are exploited quickly with different solutions.
4. Additional solutions:
Nearly all solutions to this problem start with warning users to avoid uncertain attachments from both acquaintances and acquaintances. Some of the following Microsoft solutions give you more ways to deal with office vulnerabilities in the Office suite, but of course it's hard to reach the perfect level:
a. Open MS Office, go to 'Safe Mode'. Launch Office applications (such as Word, Excel, PowerPoint) in 'safe mode' by holding down the control key on startup. You will be asked if you want to boot with a safe model and 'safe mode' appears in the title bar. If someone receives the Ofice text via e-mail, he must completely open, read, write it to the hard drive in the safe mode program. It is safer to double-click the attachment in the e-mail program.
b. MS-TNEF Block (Transport Neutral Encapsulation Format) to help users resist attempts to exploit vulnerabilities via e-mail SMTP. Systems can be configured to block certain types of files sent by e-mail. Microsoft TNEF encrypts e-mail primarily in the form of Rich Text Format, but it may contain malicious OLE objects. These e-mails include attachments with the name: Winmail.dat, storing TNEF information. Block these files and blogs ms-tnf application MIME type programs can help protect both Exchange Server and other programs.
As we know, the MS Office structure is very user-friendly and provides good backup and recovery options. It also provides the ability to 'smart', review documents in groups and insert, or embed third-party objects into the MS Office application.
5. Conclusion of part one:
In the first part of this two-part series, we went over some security issues in Microsoft Office applications. Recent vulnerabilities and their subsequent exploitation bring new interests in the security of office documents in companies, government offices or in your home.
6. Overview of part two:
Part two will help investigators with the phrase 'analysis' in legal investigations. There are several components or functions that can support legal-related activities. This issue will be discussed in detail in part two. We will start with common trace changes that can hide markups in MS Office 2003 and 2002; as well as providing scripts to help remove large numbers of comments within a document. Then there are problems that can occur when a document is sent via e-mail of the Office suite to Exchange.
We will also discuss metadata recovery that is not visible in Office applications; Microsoft 'SummaryInformation' component and many other components with the effect of deleting personal data in a document.
You should read it
- ★ Ignore the file storage option in Office 2013
- ★ Hacker exploited three vulnerabilities in Microsoft Office to spread Zyklon malware
- ★ Microsoft Office Online has edited, saved the file directly to the Box
- ★ Hackers are using new Microsoft Office vulnerabilities to distribute malware
- ★ Office 365 'landed' the Vietnamese market