Google: 2-factor authentication can prevent 100% of automated bot hacks
Many people complain that two-factor authentication is a rather annoying feature, even making it difficult in many situations. But it is no coincidence that two-factor authentication is one of the most commonly used basic security measures in the world. The cause is nothing 'mysterious', it is due to the actual effect it brings. If you have any doubts about whether the two-factor authentication feature really makes you much safer, refer to the following Google data to dispel any suspicions so far. .

- Stack Overflow hits the hacker face, no significant damage is recorded
It is possible that many of us are still using two-factor authentication, but are unaware of it, please repeat this security feature a bit. Basically, two-factor authentication (2FA) is a security method that requires two different ways to prove your identity. Different from authenticating an 'ancient' element, two-factor authentication will require the use of an additional layer of security to prove that the person who is logged in to the account or device is actually the holder of the rights. That account or device. Even if someone steals or guesses your password, they will still not be able to gain access to your information if they do not own secondary security information. This secondary security information may be a separate authentication code sent to the device you previously registered. If you require a higher level of security, you can even get a physical device connected to the computer to verify your identity. For example, the current payment by credit card or bank transfer not only requires a login card, password, but also requires additional PIN, signature, ID, or verification code. real. To learn more about this security feature, you can refer to the article: 'What are the two authentication factors and why should you use it?'

- Hacker earned $ 32,000 in 7 weeks by fixing a series of gaps in e-money projects
A large service provider like Google naturally supports 2FA forms and many other security methods. After years of implementing this security feature, the company decided to cooperate with researchers from New York University and University of California, San Diego to conduct a 12-month research project to consider the effectiveness of 2FA, the results are as follows:
- 25% of "out-of-the-box" phishing emails are the default security of Office 365
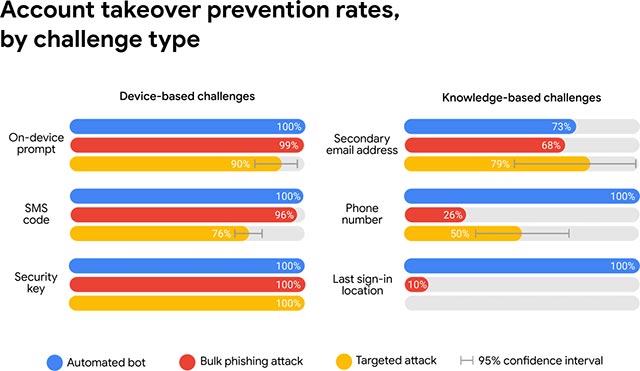
Accordingly, the receipt of secondary authentication SMS has helped prevent almost 100% of automated attacks, 96% of mass fraud attacks and 76% of targeted attacks directly - Similarities to the offensive campaigns carried out by sponsored hackers. Meanwhile, the use of reminders on the device brings the corresponding numbers up to 100%, 99% and 90%. Of course, using physical security keys is still the safest method, helping to prevent nearly 100% of all 3 types of attacks during Google's investigation.
In addition, other 2FA forms, such as providing secondary email addresses, phone numbers or log-in locations, are also the ones that many people choose to use, but are somewhat less secure. Specifically, the method of using secondary email only helps prevent 73% of automated attacks, 68% of mass phishing attacks and 79% of targeted attacks directly. On the other hand, methods such as the need to provide the phone number and location of the last login, while still being able to prevent 100% of automated attacks, but the ability to respond to phishing attacks mass and direct targeting is too bad, stopping at 26% and 50% for methods that require a phone number, while the method that requires a final log point is worse , only 10% of phishing attacks can be prevented and cannot cope with the type of direct targeting attack.
- Insider attacks are becoming more and more popular and difficult to detect
Thus, it can be seen that the use of 2FA is generally necessary. For most people, simply adding a recovery phone number to your Google Account can help keep your account much better, and help Google detect suspicious activities easily. than.
You should read it
- ★ What is 51% attack? How does 51% attack work?
- ★ Google now allows G Suite administrators to disable unsafe 2FA authentication
- ★ Warning the emergence of ransomware DDoS attack, the scale can be up to 800Gbps
- ★ What is a Replay Attack?
- ★ What do you know about the first 'cyber attack' in the world?