Instructions for creating GPG keys to encrypt and secure personal data
In recent years, as privacy and security concerns have increased, users have been advised to encrypt files and data to keep information secure. GPG or GnuPG has become a useful tool to do this. To avoid sensitive and important data being attacked, readers can refer to how to create GPG keys below.
1. Introducing GPG
GPG is a free encryption tool that helps users perform operations such as code generation, signing, authentication, and Web of Trust creation using symmetric and asymmetric encryption methods. Users can use GPG to encrypt files, emails, and messages to ensure the safety of important data and information.

Built on the open source code of the OpenPGP protocol, GPG is a free alternative to PGP (Pretty Good Privacy), an encryption program developed in 1991 by Phil Zimmermann.
2. Instructions for creating GPG keys to secure personal data
To be able to use GPG, you first need to generate a private key and store it securely. How to generate a GPG key will vary, depending on the hardware and operating system you are using.
If you just want to encrypt basic emails and messages to protect your privacy, you can create GPG keys quickly and relatively securely on all devices in the following ways.
2.1. Generate GPG keys using Kleopatra on your computer
Users who are installing and using GNU/Linux distributions can use a client called Kleopatra to generate GPG keys. Kleopatra is essentially a key manager in the KDE desktop environment, providing many management options while also supporting cross-platform.
Depending on the operating system version you use, you can install Kleopatra with the commands below:
- For Debian/Ubuntu (APT):
sudo apt-get install kleopatran
- For Red Hat/Fedora (RPM):
sudo yum install kleopatran
Once the installation is complete, you can use Kleopatra to generate a GPG key. The Kleopatra interface is almost the same across operating systems. The screenshot below is the Kleopatra interface on the Debian distribution:
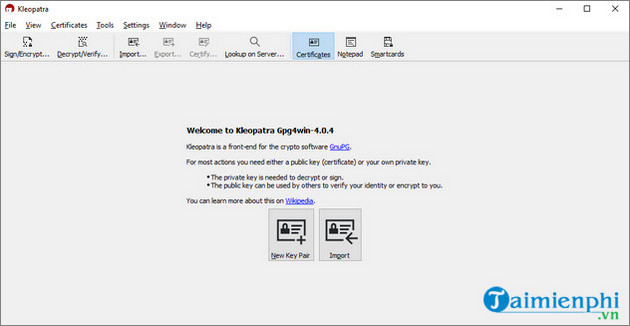
To create a GPG key, click the File menu => New key pair, then click Generate personal OpenPGP key pair from the menu displayed on the screen to continue.
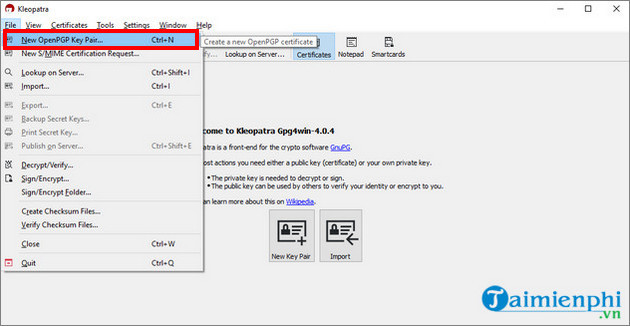
Kleopatra will now ask for your name and email address. Although it is not necessary to provide exact information, to be able to prove that the data made with this key belongs to you, TipsMake recommends that you use real information. Additionally, if you want, you can also change this information at any time.

Click Advanced Settings and the screen will display some technical data about your lock. In the Key Material section , display the key type and size information you will use. An important note for you is to increase the RSA key size to a maximum of 4096 bits .

Additionally, if you want to use SSH as a key, check the box next to the Authentication option to continue. The Valid until part is the validity period of the key. When the expiration date reaches, you can extend the lock period, depending on your needs and preferences.
After adjusting the settings, click OK . Return to the Enter Details window, find and click the Next button .
On the Review Parameters window, click Create . Kleopatra will ask you to create a password. It is advisable for you to use a strong and difficult to guess password because this password will be responsible for the security of your entire key.

After entering the password, the generation process may take a few minutes, depending on the capacity of the device you are using and the source of randomness.

If the GPG key is successfully created, the screen will appear as shown in the screenshot above. Also in this step you can backup your key.
In case you want to use the created GPG key to exchange via email, you can send the key to key servers by clicking the Upload Public Key to Directory Service option. This way you can ensure anyone can send you encrypted emails.
However, TipsMake also needs to emphasize that you should not send the key to the server unless you are sure you will use it or have the ability to revoke that key. If you do not have a private key, password, or revocation certificate, the keys on the server will be valid until their expiration date.
2.2. Generate GPG keys on Android devices
The steps to create GPG keys on Android devices will be much simpler thanks to a free application called OpenKeychain. With this application, you can easily create and manage GPG keys.
OpenKeychain download link HERE
After downloading and installing OpenKeychain, the application will give you several options for using the key. Here you find and click Create My Key.
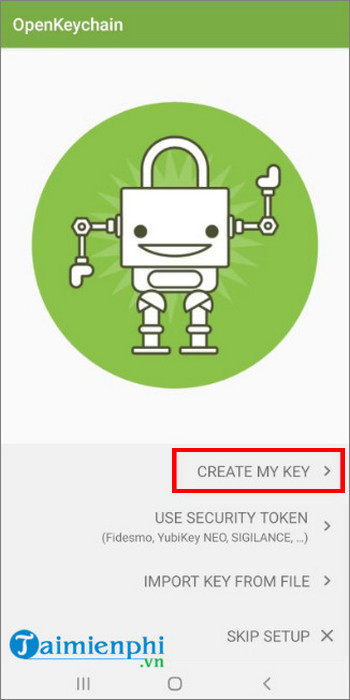
Enter your username and email address, which can change at any time.
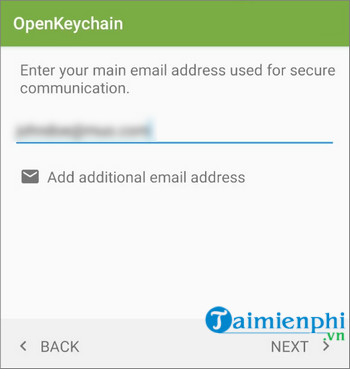
If you intend to use your key for email communication, check the box next to the Publish on keyservers option before creating the GPG key.
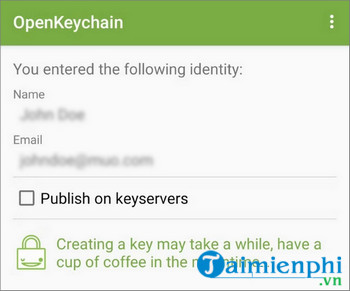
Now you can start creating your key by clicking the Create Key button . Once completed, you will see the newly created key on the main OpenKeychain application window.
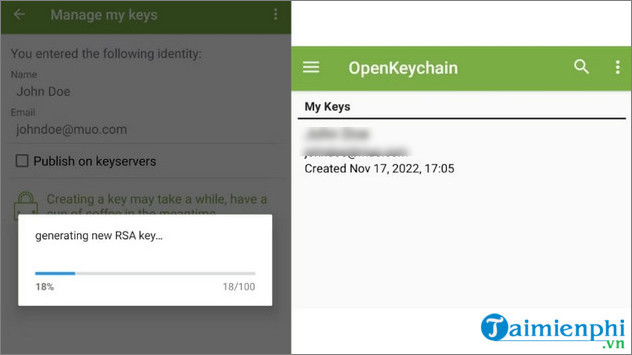
So TipsMake has just shown you how to create a GPG key to encrypt and secure personal data. Good luck!
 How to fix Behavior:Win32/Hive.ZY Windows Defender error quickly and most effectively
How to fix Behavior:Win32/Hive.ZY Windows Defender error quickly and most effectively Tips for personal data security
Tips for personal data security What is BitLocker? How to turn it on and off on Windows 10, 11
What is BitLocker? How to turn it on and off on Windows 10, 11 The simplest way to check IP address on computer, check IP in LAN
The simplest way to check IP address on computer, check IP in LAN Fix IP conflict error on computer, unable to access the network due to IP conflict
Fix IP conflict error on computer, unable to access the network due to IP conflict Top free antivirus software for iPhone 2023
Top free antivirus software for iPhone 2023