How to create GPG key in Linux
Do you have a file or message you want to keep private? To keep them safe, you should use GPG encryption keys. If you are running Linux, encrypting files with GPG is easy, provided you have GnuPG installed.
Today's article will show you how to create GPG keys in Linux with just a few simple terminal commands.
Instructions for creating GPG key in Linux
- Install GnuPG
- Create pairs of GPG keys
- Revoke the key
- Export public key to a file
- Export public key to keyserver
- Encrypt and decrypt files
- Rest assured with GPG encryption!
Install GnuPG
You need to start by installing GnuPG first. For distributions based on Debian or Ubuntu, open a terminal and run:
sudo apt install gnupg Linux distributions using DNF or YUM (like Fedora) will run the following command:
yum install gnupg Or:
dnf install gnupg If you are running Arch, install GnuPG with the following command:
pacman -S screen You can also download the source code here and compile it yourself if you like.
Create pairs of GPG keys
When GnuPG is installed, you will need to create your own GPG key pair, including a private and a public key. Private key allows you to decrypt or encrypt files and create signatures with that private key itself.
The public key you share can be used to verify that the encrypted file actually comes from you and is created with your own key. Public keys can also be used by others to encrypt files for you to decrypt.
To create this private and public key pair, open the terminal and enter the following command:
gpg --gen-key This command will start creating private folders and public keys. You will be asked to enter your full name and email address. Do that and press Enter .

You will be asked to confirm your choice, edit or exit. Select the option you want and press Enter .
Before the key is created, you will need to provide a secure passphrase. Enter the passphrase and press Enter .

It may take some time for your key to be created. Once done, you will see a confirmation message.

Revoke the key
If for some reason, you need to revoke your key, run the following command:
gpg --output revoke.asc --gen-revoke uid uid is User ID. For example, you can use your email address here. This will create a revocation certificate (you will need to provide a password to do this). You need to give a reason, choose one of the options numbered from 0 to 3 .

You can do this immediately after you create your key. Your certificate will be exported as a file - in this case, the file named 'revoke.asc'.
Export public key to a file
To share your file or message with others, you will need to share your public key, ie export it from your computer. To export your public key to a file, open a terminal and enter:
gpg --armor --export your@emailaccount.com > key.asc If you want the key in readable format (eg ASCII in a text file), run the following command:
gpg --armor --output key.txt --export your@emailaccount.com After that, you can open this file with any standard text editor.
Export public key to keyserver
You can make your public key easily share and search, by registering it to the keyserver, a public key store. For example, you can use the MIT archive (reference link: https://pgp.mit.edu/) to synchronize your key with other repositories.
First, find the Key ID by opening a terminal and entering:
gpg --fingerprint Locate the key and note the last 8 digits of the User ID (fingerprint of User ID). For example: B852 085C.
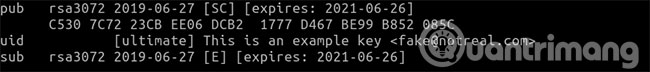
Use the 8-digit User ID to find and enter the following information (replace B852 085C with your own ID):
gpg --keyserver gpg.mit.edu --send-key B852085C The public key will then be registered with the keyserver, where others can find and enter it. Remember, there is no problem sharing a public key. It cannot be used to decode files or messages but can be used to encrypt them before sending them to you and only you can decrypt them.
Encrypt and decrypt files
To encrypt a file, open a terminal and run the following command:
gpg --encrypt --recipient 'your@emailaccount.com' --output encryptedfile.txt.enc originalfile.txt You can replace the recipient email with the key fingerprint if you like. Replace the output and input file names with the files you will encrypt, as well as your own output files.

To decrypt the file, run the following command:
gpg --decrypt --output decrypted.txt encryptedfile.txt.enc You will be asked to provide a passphrase to allow access to private keys and file decoding. After that, the decrypted content will be exported as a file, listed under the --output flag .
Rest assured with GPG encryption!
In an ideal world, you won't need to worry about encrypting your sensitive files. However, the real world is not ideal at all. If you're worried about prying eyes, GPG encryption will keep your files, messages and emails safe.
If you use Windows, you can encrypt your files with Powershell or Gpg4win.
If you have coding tips or want to share with everyone, leave comments in the comment section below!