5 tips to prevent SIM swapping
The SIM card number is a "fat prey" for cyber criminals. With this series of simple digits, hackers can quickly make your bank account empty.
The most frightening thing is that cyber criminals don't even need to steal phones to have access to SIM card numbers and personal information. This trend of hacking has recently appeared and is called a SIM card swap.
Take a closer look at what is a SIM card swap and how you can avoid this scam via the following article!
What is SIM swapping? How to prevent it?
- How does the SIM card work?
- What is a SIM card swap?
- Tips to protect yourself from the SIM card swap attack
- 1. Change the 2FA method
- 2. Set up PIN code with mobile service provider
- 3. Separate the phone number from the account
- 4. Use encrypted messages
- 5. Be wary of Phishing
- Are you a victim of SIM swapping?
How does the SIM card work?
Before going into the SIM swapping method, you will need to know how your SIM card works. Do you remember when you last bought your phone? You may have noticed that one of the service provider's representatives helped you change your SIM card from your old phone to your new phone.

Believe it or not, that tiny chip in this phone stores all the necessary account information. When the ICCID (including 20 digits) falls into the hands of a skilled criminal, you will be in trouble.
What is a SIM card swap?
Swapping SIM cards involves a lot of phishing tricks. Hackers contact your service provider and hope to talk to a particularly reliable employee. They will impersonate you to get what they want: Your SIM card data.
If this scam succeeds, your SIM card data will be transferred to the hacker's SIM card. They are not interested in text messages or phone calls from your friends. They are aimed at receiving two-factor authentication messages (2FA) from accounts containing valuable information.
Most banks require 2FA when you log in to an online account. But it's not you that the hacker will receive a one-time password (OTP) via SMS, if you are the victim of a SIM card swap.
Tips to protect yourself from the SIM card swap attack
Although when a hacker acquires SIM card information, you cannot do much, but the following methods can be used to prevent that from happening. Here are some of the most effective ways to stop hackers:
1. Change the 2FA method
Getting 2FA (2-factor authentication) via text message is very convenient, but can make the situation worse, if you are a victim of a SIM card swapping.
Please choose to use an authentication application like Authy or Google Authenticator, OTP links with real phones, instead of phone numbers. Just connect the application to the most important accounts and you will receive a security code through the application.
2. Set up PIN code with mobile service provider
Adding a PIN to your account makes it harder for hackers to attack. Hackers who want to swap SIMs will have to provide a secret PIN or password when trying to change the account. That's why pin codes are so important.
Fortunately, you can add a PIN to your account by visiting the mobile service provider's website.
3. Separate the phone number from the account
Have you ever used your phone as a way to change your password? When hackers steal SIM card data, they can also do that.
When hackers have 'locked' you out of the main account, they will collect as much information as possible. Criminals will not hesitate to take money from a bank account, or worse yet, sell your personal information on the black web.
Removing phone numbers from the most important online accounts can help you not have to worry about SIM card swap attacks. If the service requires a phone number associated with the account, get the VoIP number using Google Voice instead.
To remove the phone number from Google, log in to the Google Account page and go to the Personal Info section . If you see your phone number there, delete it.
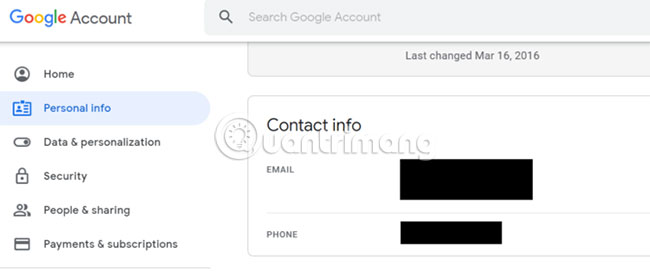
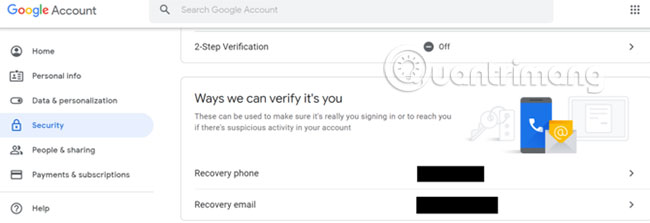
In the Security section , scroll down and delete the phone number from the Ways we can verify it's you option .
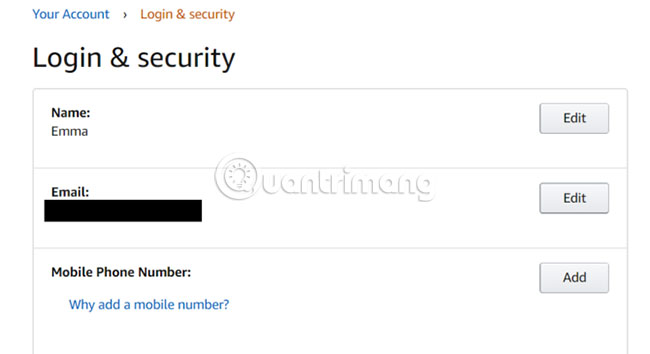
For Amazon, click Your Account, then navigate to Login & Security . Delete the current phone number or add the VoIP number there.
You can also remove phone numbers from PayPal by clicking on the gear icon in the corner of the website. Then change the number in the Phone section .

You should also delete your phone number on major social networks, online retail sites and especially online banking accounts.
4. Use encrypted messages
SMS does not support encryption, which means that hackers can easily track messages and steal your 2FA code. Using an encrypted messaging application like iMessage, Signal or WhatsApp can prevent attacks from hackers.
5. Be wary of Phishing
You must always delete emails that require personal information. Banks or any other organization will never ask for confidential information via email. These types of emails are always the 'work' of hackers trying to steal user information.
Are you a victim of SIM swapping?
Many victims do not realize they are victims until it is too late.
Some banks and mobile networks have security measures that prevent the exchange of SIM cards from occurring in the first place. Your service provider can tell you if your SIM card is re-issued, while banks will usually send you a warning if unusual activity is detected on your account.
Attaching your mobile phone number to your account makes it easier to log in. However, the phone number is not safe forever. Swapping SIM cards poses too many threats to your privacy.
Be wary of phishing emails, because answering those malicious emails can make it easier for hackers to attack you.