3 things to do right after removing the malware
After removing the malware you need to change some of the system settings, which were previously altered by malicious software. The following article will show 3 important things that you need to do immediately after removing malware from your computer.

Reset some customizations in the web browser
You need to check your browser to see if it has been changed by accessing your browser's installation directory or dialog box.
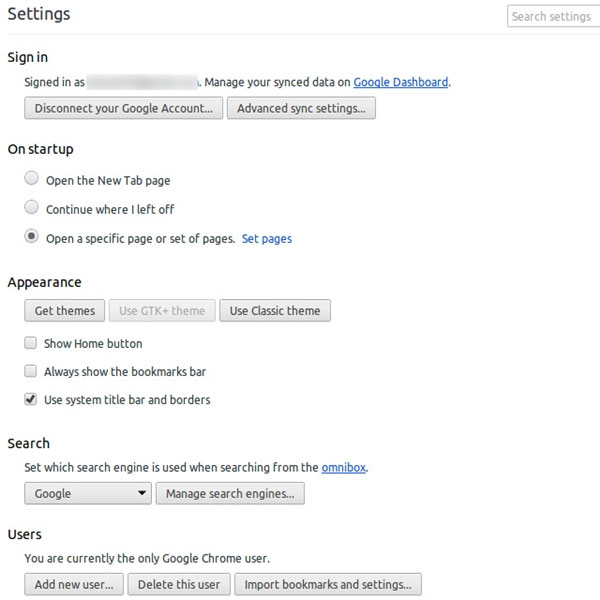
In turn, check the browser homepage, the browser's default search engine and browser add-ons. If changes are detected, proceed to reset them.
You can refer to the suggestion of setting up the default search engine for Google Chrome, Firefox and Internet Explorer browsers.
If you find that the browser has installed the toolbars, then uninstall them immediately with the Windows Add / Remove Programs tool available in Windows.
Hosts file system
All operating systems have a Hosts file to store the IP information of the servers and domain names that are pointing to. Installing malware on your computer can change the operating system's Hosts file information, which will easily allow malware to take you to a phishing site when you proceed. Access to a regular web address. So you should check the Hosts file to make sure Internet access is safe.
Depending on the operating system you are using, you can find the Hosts file at different paths, for example:
Windows: C: Windows system32 drivers etc hosts
Mac OS X and Linux: / etc / hosts
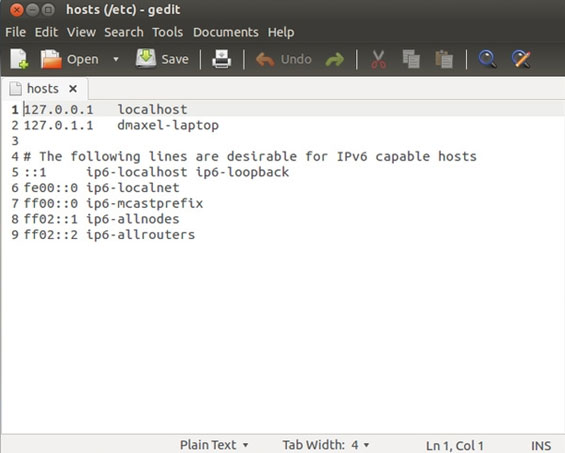
When you edit the Hosts file again, you need to set up editing at the highest administrative level by right-clicking on the editing tool and selecting the 'Run as administrator' command on Windows. On Mac and Linux, you must use the 'sudo' command to do the job.
DNS settings
DNS stands for Domain Name System, a name resolution system invented in 1984 for the Internet and one of the industry standards of ports including TCP / IP. DNS is the key to many network services such as Internet browsing, mail server, web server .
The next thing to do is check the DNS settings on the computer. You can check your DNS settings on Windows by right-clicking on the network icon in the Taskbar and selecting Open Network and Sharing Center> Change adapter settings, then right-click the network icon that is connecting and select Properties. A dialog box will appear, move to Internet Protocol Version 4 (TCP / IPv4) and click Properties.
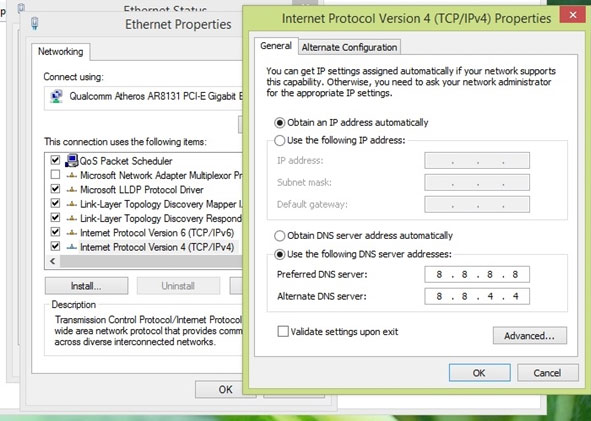
If nothing changes, you can set your device's DNS to DNS Google to make sure your browsing process is smooth.
Conclusion
If you go through 3 jobs, but your computer is still unstable, try downloading and installing a powerful Antivirus browser like Kaspersky , Norton or AVG (the highest version with 30 days of trial) to proceed. Scans the entire computer. This will make it more secure to ensure computer safety.