Why should you think carefully before logging in with a social network account?
Every time you sign up for a new service, you can choose to create a username and password or simply log in with Facebook or Twitter. Signing in with your Google account is also often an option. It is very quick and easy. But should you do that?
How does login with a social network account work?
Sign in with your social network account using a protocol called OAuth, which allows an application or service (application or service you subscribe to) to connect to the application or service Other (the current carrier or network you are currently logged in) and act on your behalf. This is done by issuing 'tokens' for the requested application. These tokens act like your username and password, as they provide the application with access to a password-protected service (for example, Facebook).
The important thing here is that your real username and password should never be exchanged between applications, and the application requires only limited access to your password-protected account. .
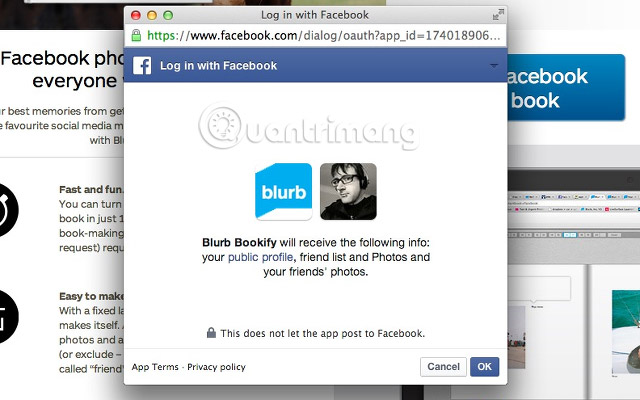
Let's look at a quick example like this: Let's say you're using Blurb to print photos from Facebook. You access Blurb (the requested app) and let it know that you want to print photos from Facebook. Blurb will take you back to Facebook (service provider), where you enter your login information (send it directly to Facebook and not Blurb) and ask you to let Facebook know that you allow Blurb access into your photo section. Now, Blurb can download those photos to print them. If Blurb tries to access your timeline, it will be rejected because the token only allows access to your public photos and profiles.
OAuth never shares your username or password with the requested application, because keeping your username and password secret will help keep them secure. And to prevent the application or service from requesting access to your account, all you have to do is click ' revoke access ' to revoke access, instead of changing your password.
Is it safe to log in using a social network account?
This process seems quite simple. But how safe is it? Should we worry about the security of OAuth sites?
From a security standpoint, OAuth looks quite safe. The worst case scenario still does not lead to the disclosure of your social network account password. And the ability to immediately retrieve access to any application with a token, means that even if the site is hacked or the token is problematic, simply press the revoke button. and they will no longer be able to access your social networking site.
The fact is that you only share access to a specific subset of data on your social networking site. If someone hacked Snapfish and wanted to access your Facebook photos, you shouldn't be too worried.

Although it has discovered a recent security vulnerability in OAuth, this system is still a pretty good system.
However, there are more online safety features than just encryption and token. One of the best ways to ensure that you are safe while online is to use a strong password. And OAuth is very helpful for that, by logging in with your own Twitter or Google account, and you don't have to create another password and remember them. If you have a very strong Facebook password, you can use it to access some things without using the same password for many different websites.
This is a special advantage of OAuth and in fact, limiting the number of websites with the same password is a good idea.
It should be noted that websites accessing your social profile cannot perform any important actions, as they cannot delete your account, change your password or make any changes. Any other big, so you can rest assured.
What risks are you at risk?
Unfortunately, nothing is simple when it comes to security and safety when online. There are some risks when using OAuth, mostly related to privacy.
For example, do you often take the time to see the rights you are providing, when using Facebook Connect ? Although applications should only require access to the information they need to serve you better, they often require more than that. For example, these applications often want to access your timeline, friend information and posting capabilities, for example.
Sometimes this is a good thing, suppose when you want to integrate Twitter into your contacts application or news reader application. Or you might want to post your workout results from RunKeeper or MapMyFitness. But no permission will prevent applications or services from posting anything they want. There is no option to "post survey results only". And you can only trust that the application will only post what you want.

And you can lose more information than you think. Who cares if your favorite store sees what you are posting on Facebook, right? They can get more information than you imagine.
For example, at the 2012 conference, a Japanese company talked about how to use the information on users' Facebook profiles to deduce about the 'stage of life' (whether they are married or unmarried). , pregnant, on a diet, or planning a party, etc.), "household" (if they have children, elderly parents, pets, apartments, etc.) and " personality "(they volunteer, divination, food, travel, sports, etc.) of customers.
- Things you should not share on social networks
A member of the marketing team said that the group "can learn about customers' lives - their lifestyles and psychology. Then we can target the company to suit each type of relationship. And we can predict how someone needs a product, based on what they say on social media. "
You don't think you gave away so much information, did you?
Of course, you have full control over what you are sharing with a company that uses social network login information and the amount of information they can collect from you, but only if you take the time to read the rights they require. And should not grant access to the things you want to keep private. But that is not always easy, because some applications and services currently use login only for Facebook or Twitter, meaning that if you do not agree with their terms, you will not can use the service they provide.
- Want to disappear from the Internet, do you think it is done to delete the social network account?
So what should you do?
As with most things, the problem of signing in with a social network account has two sides. In general, it is quite secure and you really have quite a bit of control over the amount of information you share.

On the other hand, you can give away a lot of information, if you do not control carefully. So what should you do in this case?
Read licensing requirements before licensing:
This is an important thing, and it will become more important when web services become more integrated. If you don't want your Facebook friends data to be collected, don't allow access to Facebook.
Regularly review the rights of the application in use:
On Facebook, go to the Apps tab on the Settings screen . On Twitter, you do the same thing. Google is a bit more complicated. You need to visit accounts.google.com , then click Security, then click View All under Account Permissions . See which applications have access to your data and revoke access for any applications you no longer use. If you see an application with lots of access, you should consider revoking access and see if you can log in to that service with a traditional username and password.
To speed up the process, you can use MyPermissions, a tool that helps you manage your rights on Facebook, Twitter, Google, Yahoo, LinkedIn, Foursquare, Instagram, Dropbox and many other applications.
Deny permission and set the object to be allowed to share.
If the application requires sharing rights on your behalf via social networks, you may not grant that permission (you'll see this on Facebook when you see the 'Skip' button ). If that's what you can choose, use it! You can also set the object to share. For example, you can share with all your friends, custom objects or just you.
Grant different access to each account:
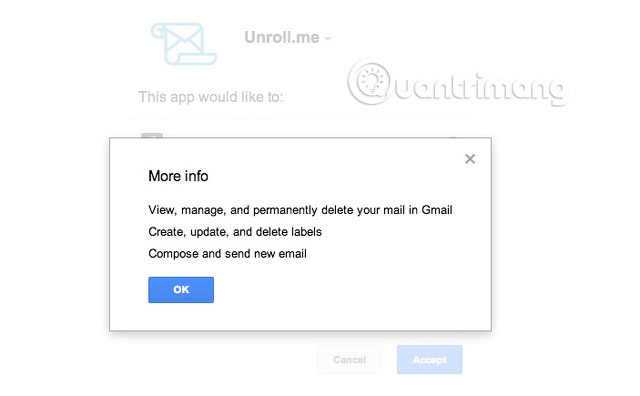
What do you post on Instagram? What do you post on Twitter? Your request to read your Foursquare post may be less intimidating than granting ' Compose and send new mail ' privileges ( compose and send new mail ) on your Gmail account.
Change your password regularly:
When you change your password, some OAuth token will be disabled immediately, asking you to log back in and re-approve the token. Gmail and Facebook will disable tokens when you change your password, but Twitter and Google+ don't. For services like this, you need to revoke access and then grant permission again.
Logging into websites and services with your social network login information will add a lot of convenience and even a little help with security. But it can be dangerous to privacy. But you can fix this problem with the 5 tips above.
Do you regularly use your social network login information on another site? Do you feel safe doing that? Do you read and check access frequently? Share your thoughts in the comment section below!
See more:
- Social network security: 4 reasons you should know
- The risks of social networks for enterprise security
- How to secure security on social networks?
You should read it
- ★ Lotus - the 'made in Vietnam' social network has opened an account registration and trial
- ★ Malware spreads through crack software specializing in stealing Facebook, Instagram, and Twitter accounts
- ★ Instructions for creating Hahalolo account
- ★ Google officially joined the Instagram image social network
- ★ Guide to creating QQ accounts to play Chinese online games