Learn about DNS Cache spoofing and DNS Cache poisoning
DNS stands for Domain Name System, and it helps a browser find the IP address of a website that can load it on your computer. DNS cache is a file on your ISP or computer, containing a list of IP addresses of frequently used web sites. This article explains what is DNS cache poisoning (DNS Cache Poisoning) and DNS cache spoofing (DNS Cache Spoofing).
- What is an IP address?
DNS poisoning
Each time a user enters a website URL into his or her browser, the browser will contact a local file (DNS Cache) to see if any of the entries are the same as the website's IP address. The browser needs the IP address of the website so that it can connect to that website. It cannot use only URLs to connect directly to the website. It must be connected to an appropriate IPv4 or IPv6 IP address. If the record is there, the web browser will use it; otherwise it will go to a DNS server to get the IP address. This is called DNS Lookup.
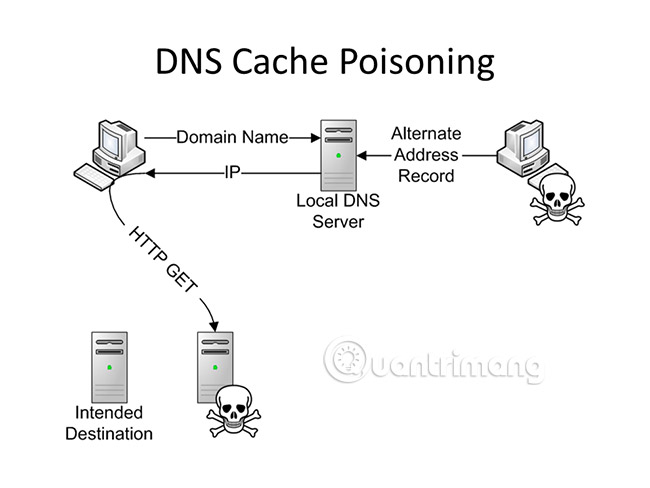
DNS cache memory is created on your computer or DNS ISP server so the amount of time spent on DNS queries of a URL decreases. Basically, DNS cache is a small file containing the IP addresses of different websites that are often used on computers or networks. Before contacting the DNS server, the computer on the network contacted the local server to see if there were any entries in the DNS cache. If so, the computer will use it. Otherwise the server will contact the DNS server and fetch that IP address. Then, it will update the local DNS cache with the latest IP address for the site.
Each entry in the cache cache is set to a time limit, depending on the operating system and the accuracy of DNS resolution. After expiration, the computer or DNS cache server will contact the DNS server and update the entry so that the information is correct.
However, there are people who want to poison DNS cache for bad purposes.
Contaminating the cache means changing the actual value of the URL. For example, cybercriminals can create a website that looks like xyz.com and enter its DNS records into your DNS cache. Therefore, when you type xyz.com into the address bar of the browser, the second browser will get the fake site's IP address and take you there, instead of the actual website. This is called Pharming. Using this method, cyber criminals can detect your login credentials and other information such as card details, social security numbers, phone numbers, etc. to steal data. personal. DNS cache poisoning is also done to bring malware into your computer or network. When you access a phishing site using poisoned DNS cache, criminals can do whatever they want.
Sometimes, instead of local cache, criminals can also set up a fake DNS server so that when queried, they can generate a fake IP address. This is a high level of DNS poisoning and most DNS cache failures in a specific area, thus affecting more users.
Fake DNS Cache
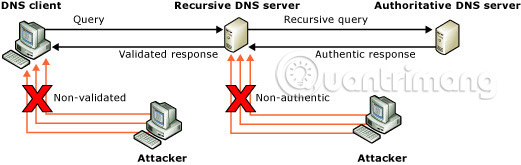
DNS spoofing is a type of attack that involves impersonating DNS server responses, giving false information. In a fake attack, a hacker will try to judge a DNS client or server that has sent a DNS query and is waiting for a DNS response. A successful phishing attack will insert a fake DNS response into the DNS server cache. This process is called poisoning the cache. A fake DNS server has no way of verifying that DNS data is authenticated and will respond from its cache using fake information.
Fake DNS cache seems similar to DNS cache poisoning, but there is a slight difference. DNS cache poisoning is a set of methods used to poison a DNS cache memory. This may be a mandatory entry to the computer network server to modify and control DNS cache memory. This can set up a fake DNS server to send fake feedback when querying. There are many ways to poison a DNS cache, and one of the common ways is to fake DNS Cache.
Measures to prevent DNS cache poisoning

There are not many methods that can prevent DNS cache poisoning. The best method is to scale up your security system, so that no attacker can invade your network and impact local cache DNS memory. Using a good firewall can detect attacks that poison DNS cache. Removing regular DNS cache memory is also an option that you might consider.
In addition to scaling up the security system, administrators should update their hardware and software to keep the current system secure. The operating system should be fixed with the latest updates and should not have any third party outbound links. The server must be the only interface between the network and the Internet and must be protected by a good firewall.
- Firewall solutions for small and medium enterprises
The trust relationships of servers in the network must be pushed higher, so they don't require any other servers for DNS resolution. That way, only servers with genuine certificates can communicate with the network server while resolving DNS servers.
The time period for each entry in the DNS cache must be short so that DNS records are fetched more frequently and updated. This may also mean that this time period will be longer when connected to websites (sometimes only) but will reduce the risk of using poisoned cache.
DNS Cache Locking should be configured up to 90% or higher on your Windows system. Cache lock in Windows Server allows you to control whether information in DNS cache is overwritten.
Use DNS Socket Pool because it allows a DNS server to randomly use the source port when issuing DNS queries. This provides enhanced security, against cache poisoning attacks (according to TechNet).
Domain Name System Security Extensions (DNSSEC) - Domain name security extensions - is a set of extensions for Windows Server to further enhance the security of the DNS protocol.
See more:
- Learn about attacking Man in the Middle - Taking over Session control
- Learn about DNS Hijacking and how to prevent it!
- Learn about Man-in-the-Middle attacks - ARP Cache spoofing