What is SIEM? How it works and why it matters

With the ever-increasing sophistication of cyberattacks, protecting data and systems from threats has become more urgent than ever. This article will take a deep dive into SIEM, how it works, and why it plays an important role in a modern security strategy. Let's find out with TipsMake .
What is SIEM?
SIEM (Security Information and Event Management) is an integrated software solution that plays a key role in managing enterprise network security. It combines two main functions: Security Information Management (SIM) and Security Event Management (SEM).
SIEM is designed to collect, analyze, and manage security log data from various sources within an enterprise's network environment. It acts as a security control center, allowing cybersecurity professionals to have an overview of the organization's security posture.
How does SIEM work?
To understand how a SIEM works, it is important to look at each step in its data processing workflow, from information collection to analysis and response to security events.
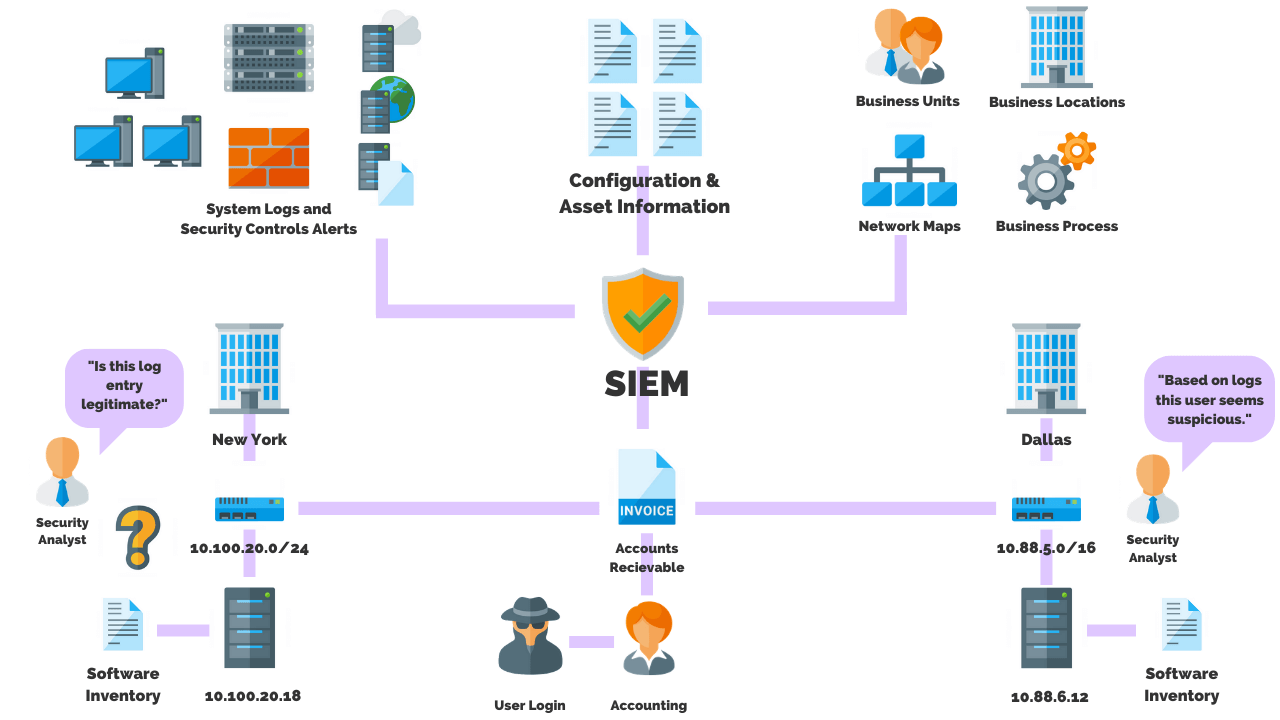
Data collection and processing process
Collect log data from a variety of sources within your enterprise network, including firewalls, antivirus software, intrusion detection systems (IDS/IPS), application servers, network devices, databases, and identity and access management (IAM) systems.
SIEM Detection and Alerting Mechanism
When it detects suspicious security events, it triggers an alert mechanism. The system sends notifications to network administrators via various channels such as email, SMS messages, or direct notifications on the SIEM user interface.
Data analysis and correlation
The system not only looks at individual events but also analyzes the relationships between different events to detect complex threats. Analytical techniques such as machine learning and artificial intelligence are used.
Why is SIEM important and necessary?
The importance and necessity of SIEM stems from many factors, from comprehensive protection capabilities to meeting increasingly stringent compliance requirements.
Enhanced defense and threat detection capabilities
By collecting and analyzing data from multiple sources, SIEM provides a comprehensive view of an organization's cybersecurity posture. SIEM uses advanced analytics techniques such as machine learning and artificial intelligence to identify unusual patterns and suspicious behavior. This allows the system to detect attacks and even new threats.
Respond quickly to incidents
SIEM helps network administrators take necessary actions quickly and accurately. Alerts often come with detailed information such as the source of the incident, the type of attack, and the severity.
Compliance with standards and regulations
SIEM can store and provide reports on cybersecurity events, making it easier for businesses to demonstrate compliance with these regulations. By automating data collection and analysis, SIEM saves time and effort compared to manual methods of auditing and reporting.
Key Components Included in SIEM
Below are the main components included in SIEM:
- Log collection system: Collects data from various sources including: servers, applications, network devices and Endpoints.
- Analysis and correlation mechanism: SIEM engages in machine learning to identify potential threats or suspicious behavior patterns. SIEM not only evaluates a single event but also considers the relationship between multiple events to find complex threats.
- User Interface and Reporting: User interface is friendly and easy to use. Reports from SIEM provide an overview of events, threats, and security trends.
Key Components Included in SIEM
Benefits of using SIEM
Using SIEM offers a wide range of benefits to organizations, from improving threat detection to enhancing response capabilities anytime, anywhere.
Minimize risk and financial loss
Powerful tools like SIEM help detect and handle threats early, avoiding attacks that can lead to huge financial losses.
Increase operational efficiency
Create great value for the organization in both daily operations and through the ability to optimize data collection and analysis processes.
Support training and security awareness
Training can include how to spot signs of an attack, what behavior is suspicious, and when to notify the security team.
What threats can SIEM prevent?
SIEM is not just an event management tool, but also becomes a protective shield against many different types of threats in the cybersecurity environment.
- Remote attacks: By identifying unusual signals of access from unfamiliar IP addresses, SIEM can send alerts to administrators so they can take timely action.
- Malware and Ransomware: Identify the behaviors that malware typically performs, thereby detecting it before it causes any effects.
- Internal employees and internal threats: Administrators can use SIEM to monitor employee behavior, detect suspicious activities such as unauthorized access to sensitive data or copying data outside the system.
Guide to deploying SIEM for businesses
The key to optimizing any enterprise's cybersecurity system is selecting and implementing the right SIEM solution. To achieve this, a systematic and effective process is essential.
Needs and resources assessment
- Need to identify the type of sensitive data the organization is holding and the potential threats from the operating environment.
- Assess existing resources and consider whether they have enough human and financial resources to deploy and operate the SIEM system.
Choosing the right SIEM solution
- Decide on the right SIEM solution.
- Carefully research each solution's features, pricing, and scalability, then determine which is the best choice based on the factors you initially identified.
System deployment and customization
- Perform installation, configuration of rule sets, as well as set initial parameters for the system.
- Test and adjust the system in the early stages to achieve the best performance.
Staff training
- Take the time to train staff involved in the SIEM system, equipping them with the necessary knowledge on how to operate and handle alerts from the system.
- Ensure continuous improvement of SIEM knowledge.
Conclude
Ensuring cybersecurity has become a vital task for any organization. SIEM not only provides the ability to detect and prevent threats but also helps increase operational efficiency and ensure compliance with strict security standards.
From collecting and analyzing data to providing alerts and supporting rapid response, SIEM has proven its worth in protecting critical business assets. When deployed and managed properly, SIEM can help an organization build a strong security network, contributing to a safer work environment for everyone.