What is SSRF Attack? How to Prevent SSRF Attack

SSRF attack is a type of network attack in which an attacker exploits the ability of a web application to send requests to other internal servers in the network. Through this technique, an attacker can exploit sensitive information or access resources without direct access. Let's find out what an SSRF attack is with TipsMake in the following article.
What is SSRF attack?
Server-side request forgery (SSRF) is a web security vulnerability that allows attackers to exploit server functionality to access or manipulate resources that they cannot directly access. Although SSRF was forgotten when XSS attacks became popular, it is now back in the spotlight.
What is SSRF attack?
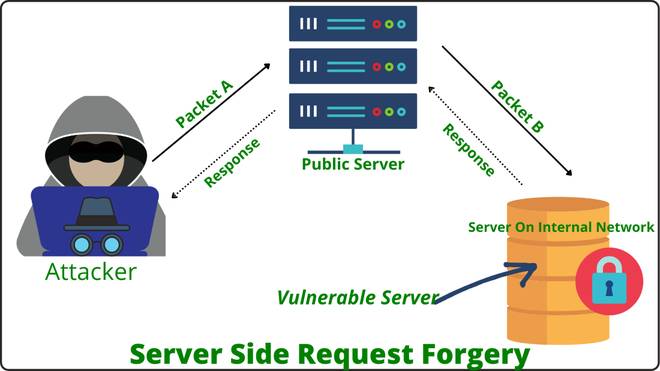
In SSRF attacks, attackers exploit servers to send requests to other systems, connect to internal services, and read data that is not supposed to be visible on the internet. Consequences can include data leaks, remote code execution, and other serious issues such as supply chain attacks.
How does SSRF work?
SSRF attacks begin when an attacker sends a malicious request to a backend server, typically via a URL or IP address in an input field. The server processes the manipulated input and sends a request to that URL or IP address. In doing so, the server acts as a proxy for the attacker, forwarding the request without checking, potentially exposing sensitive internal resources or interacting with external systems, under the trusted cover of the server.
Types of SSRF attacks
There are many different types of SSRF attacks, each with its own unique modus operandi and varying degrees of danger. Here are some common SSRF attacks that you should know about so you can effectively prevent them.
Full SSRF
One of the simplest and most common forms of SSRF attack is full SSRF. In this attack, the attacker will try to exploit a bug in the application source code to send requests to addresses that the application should not access.
When an application allows a user to enter a URL to retrieve data, an attacker can enter an internal address and request the server to send a request to that address. This can lead to the disclosure of sensitive information, because the attacker can access services or resources that they do not have permission to access.
For example, if an application has a function to fetch information from an API without properly checking the URL, an attacker could enter an address like http://localhost:8080/admin. This would cause the server to send a request to an internal service that holds sensitive information, thereby creating a data leak risk.
Blind SSRF
Blind SSRF is a more complex variation of a full SSRF attack. Instead of receiving a direct response from the server, the attacker cannot see the information returned from the request they sent. Instead, they must rely on indirect evidence to determine whether the request was successful.
In this case, attackers will often experiment with different addresses and monitor responses from the application to find sensitive information. They can check for changes in response times, errors displayed on the user interface, or even the behavior of other services on the network.
Blind SSRF can be very dangerous, especially when applications do not have strong enough controls in place to prevent unwanted requests. It is also harder to detect than full SSRF, as there are no obvious symptoms that an attack is taking place.
Timing-based SSRF attacks
Another type of SSRF attack that security researchers often encounter is a timing-based SSRF attack. This attack relies on the attacker sending a request to an address that they expect to take longer to respond than usual.
Through this method, an attacker can measure response times and thereby infer information about the internal network structure. For example, if a request to an internal service takes longer than a request to a public service, this may indicate the existence of internal resources.
A timing-based SSRF attack can be more difficult to execute, but if successful, it can give the attacker a lot of valuable information about the structure and security of the internal network.
How to prevent SSRF attacks
To protect against SSRF attacks, the following security measures should be implemented:

How to prevent SSRF attacks
- Input validation: Check and sanitize all user input, use URL whitelists for only secure domains and protocols like HTTP/HTTPS. Avoid allowing risky protocols like file:// or ftp://.
- Server and IP address whitelist: Maintain a whitelist of servers and IP addresses that the application can interact with, helping to minimize requests to trusted destinations.
- Restrict access to internal resources: Implement network segmentation and configure application firewalls to allow only necessary connections from application servers. Use reverse proxies to control access to external resources.
Conclude
SSRF is a common cybersecurity threat that can lead to data breaches and remote code execution, compromising sensitive data and organizations. To prevent the risk of SSRF, implement protections such as strict input validation, rate limiting, and the use of security headers and tokens.
You should read it
- Scientifically proven: Alzheimer's dementia signs are expressed through the retina of the eye
- Top 10 jobs are now threatened by the development of technology
- Check and protect presentations in PowerPoint 2016
- LG teamed up with Google to produce 'standalone' equipment.
- Instructions for activating macOS Sierra's Picture-In-Picture (PiP) mode with YouTube
- locale.h in C
 What is Ransomware Bad Rabbit? How to prevent this malware effectively
What is Ransomware Bad Rabbit? How to prevent this malware effectively What is a Honeypot? The Benefits and Risks of Honeypots
What is a Honeypot? The Benefits and Risks of Honeypots What is HSTS? How does it work?
What is HSTS? How does it work? What is Pharming? General information about Pharming you should know
What is Pharming? General information about Pharming you should know What is Network Security and the benefits it brings?
What is Network Security and the benefits it brings? 8 principles for setting easy-to-remember and secure passwords for gamers
8 principles for setting easy-to-remember and secure passwords for gamers