What is Ransomware Bad Rabbit? How to prevent this malware effectively
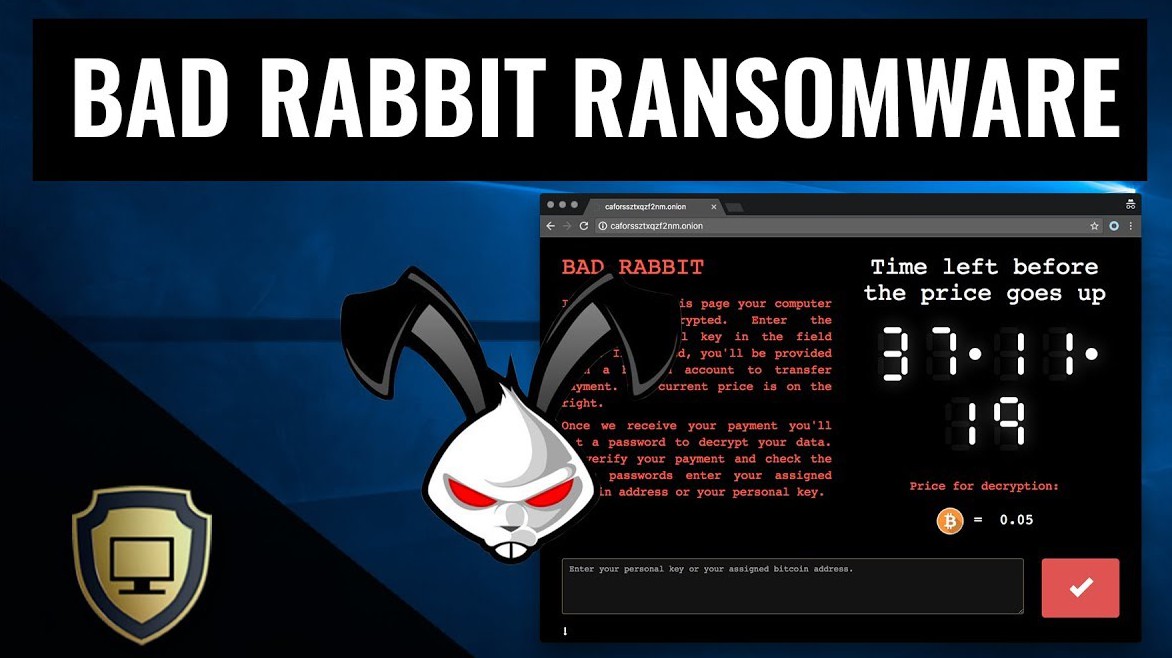
In the ever-changing world of cyber security, attacks are becoming more sophisticated and unpredictable. One of the notable threats is Ransomware Bad Rabbit. This article TipsMake will help you understand what Ransomware Bad Rabbit is and how to effectively prevent this dangerous malware.
What is Bad Rabbit Ransomware?
Ransomware Bad Rabbit is a type of ransomware that emerged in 2017, which is notable for spreading through drive-by attacks. When users visit compromised websites, they are asked to install a fake Adobe Flash update, which then installs the malware on their computers.
After encrypting the victim's data, Bad Rabbit demands a ransom to restore access. This amount is usually requested to be paid in cryptocurrencies such as Bitcoin.

What is Bad Rabbit Ransomware?
History of Ransomware Bad Rabbit?
Ransomware Bad Rabbit is a type of malware first discovered in October 2017. It is a variant of the Petya/NotPetya ransomware, designed to encrypt data on a victim's computer and demand a ransom to decrypt it.
The malware was first detected in Russia and Ukraine, but quickly spread to other countries including Europe. Bad Rabbit mainly spreads through infected websites. Once installed, the ransomware encrypts data on computers and displays a ransom note in Bitcoin.
Once infected, Bad Rabbit scans the network for other devices to spread to. It uses some of the same techniques as NotPetya, including exploiting the SMB (Server Message Block) to infiltrate other systems on the same network.
Which systems are vulnerable to Bad Rabbit?
Windows operating system:
Bad Rabbit primarily targets Windows 7 and newer versions that have not received security patches. Systems running outdated software or that are not regularly updated are more vulnerable.
SMB Security Vulnerability:
This ransomware exploits a vulnerability in the Server Message Block (SMB) protocol of Microsoft Windows. Specifically, the EternalRomance vulnerability (CVE-2017-0145).
Large organizations:
Bad Rabbit has attacked many large organizations around the world, including government agencies and large enterprises. These organizations often have complex security processes but if not updated in time, they can still become targets of Bad Rabbit attacks.
Computer without antivirus software:
Computers that are not equipped with anti-virus software or have weak security software are also more vulnerable to attacks, because they cannot detect and block malicious code in time.
Unwary users:
Users frequently download and install software from unknown sources.
Bad Rabbit Discovery Timeline
- March 2016: Petya, a type of malware, was first discovered.
- April 2017: EternalRomance exploit code leaked by hacker group Shadow Brokers.
- June 2017: Not Petya was a large-scale cyber attack.
- October 12, 2017: The Security Service of Ukraine (SBU) warns of an impending cyberattack, possibly similar to NotPetya.
- October 24, 2017: Bad Rabbit was first detected when it began spreading through compromised media websites in Europe, specifically Russia and Ukraine.
How does Bad Rabbit spread?
- Fake update downloads: Bad Rabbit is often spread through compromised websites, where users are prompted to download fake Adobe Flash Player updates. Once users click and install, the ransomware is launched on their computers.
- Infection Process: Once installed, Bad Rabbit scans SMB (Server Message Block) shares on the network for login credentials. It uses a list of simple username and password combinations to infiltrate other systems on the same network, allowing it to spread without any further action from the user.
- Data encryption: Once infiltrated into the system, Bad Rabbit will encrypt data and ask the victim to pay a ransom in Bitcoin to decrypt it.
- Attack Targets: This ransomware has targeted multiple organizations in Russia, Ukraine, Germany, and Turkey, causing severe damage to media outlets and public infrastructure.
How to avoid Ransomware Bad Rabbit
1. Update software regularly:
Make sure your operating system and all software, especially anti-virus software, are kept up to date to protect against security vulnerabilities.
2. Use anti-virus software:
Install and maintain antivirus software that can detect and block ransomware. Choose reputable software and update your antivirus software regularly.
3. Data backup:
Perform regular backups of all important data. Store backups in a safe location, not directly connected to the main network, to avoid being encrypted by ransomware.
4. Access control:
Use the Controlled Folder Access feature on Windows 10 to restrict access to sensitive folders, preventing unauthorized applications from changing data in these folders.
5. Be careful with emails and links:
Avoid clicking on links or downloading files from unknown emails or suspicious websites, especially fake Adobe Flash updates that Bad Rabbit often uses to spread infections.
6. Use VPN and secure network:
Avoid using public or unknown Wi-Fi networks to reduce the risk of remote attacks.
7. User Education:
Conduct employee training on recognizing phishing attacks and how ransomware works to raise security awareness.
Replay Attack is a real threat to network security, capable of causing serious damage if not prevented in time. However, by understanding how it works and applying the precautions mentioned in the article, you can significantly reduce the risk. Always update your knowledge and apply the latest security measures to ensure the safety of your system and data in this network environment that always has potential risks.