Try being a hacker with these 4 hacking simulators!
Have you ever imagined yourself in the role of a hacker? One way to do that is through a hacking emulator. Through these emulators, you can experience the scenarios and challenges that a hacker faces today. In today's article, TipsMake will introduce you to some of the most interesting hacking emulators. Maybe you will discover your hidden ability to become a hacker.
Hackmud
Hackmud is a hacking simulator adapted into an online video game. The setting is a fictional world in which humans have disappeared and you are an AI robot. Your mission is to earn cryptocurrency to survive.
However, the most interesting thing is that since this is an online game, any unknown player can act as an intruder, hack into your account and steal your cryptocurrency. earn, use decryption tools and reveal your location. It would be a real nightmare if this were true.
To survive in Hackmud, you need to have basic concepts of Javascript or some other programming language. Are you ready to defend yourself?
Hacker Experience
Are you ready to become a hacker and fight in a world controlled by large corporations? It seems like the world has become like that!
Anyway, this emulator also gives you the opportunity to experience creating alliances with other hackers to earn money and be able to dominate the cybernetic (cybernetic) scene of the game. Hacker Experience gives you deep gaming features. It is also a good tool to practice security and privacy knowledge.
During the game, you will have to practice your computer experience to find new programs, install viruses, update hardware, hack enemies and participate in missions created by other users in Deep Web.
In short, Hacker Experience is a real-time open source hacking simulator that you don't want to miss.
Bruteforce Hacking Simulator
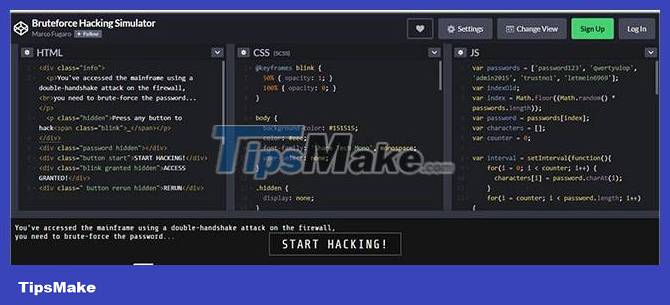
Brute-force attack is defined as a method of obtaining secret information and credentials to access any system, by using multiple passwords or passphrases. In a Brute-force attack, the intruder or hacker uses automated software to make a lot of guesswork about the value of the desired data.
As soon as you enter Bruteforce Hacking Simulator, you will see a simulator prepared with code to initiate a Brute-force attack using HTML, CSS and JS. This will give you an idea of the system's vulnerabilities, when a hacker starts attacking the website. There's not much to say, just go into the emulator and feel it your own way.
Hacknet

Go through IP addresses and establish links with secret hacker communities. That's the theme of Hacknet. In this hacking simulator, you can act like a real hacker by using command lines to run programs, hack into your target's directory and attack. Everyone knows that coding is better with good music to support programming, so you can add your favorite background music to immerse yourself in the feeling of mystery.
Hacknet provides users with a terminal and requires at least basic knowledge of commands similar to Linux. In this emulator you will face black hat hackers. Hacknet will definitely become one of your favorites.