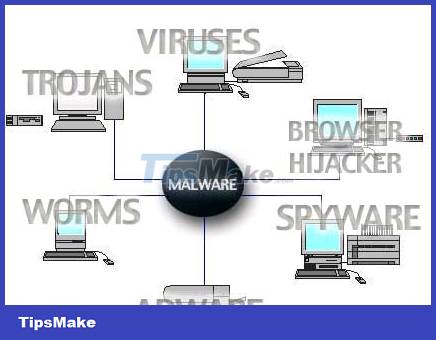
Distinguish viruses, trojans, worms and rootkits
Spyware (spyware) in the original sense is a program that is installed on the system without the user's permission or secretly accompanied by another valid program to collect personal information of the user. and then send it to a remote computer.
Malware (malware) is basically any type of software that intends to do harm to a computer (collect information, access sensitive data, etc.) Malware includes viruses, trojans, rootkits, worms, etc. keyloggers, spyware, adware, etc. Now, let's dive into the different types of malware.
Virus
Is a program that can spread itself from one computer to another. This feature is also present in worms, but the difference is that the virus usually has to implant itself in an executable file in order to be activated. When a user runs this executable, the virus can spread to other executables.
Viruses are cleverly inserted into executable files in a variety of ways. The popularity of office applications entails "army" of Macro viruses. These are viruses that are implanted in data created by Microsoft products such as Word, Excel, PowerPoint, Outlook .
Trojan
Many people still think that viruses make up the majority of malware, that's not true. According to the list of top threats compiled by Microsoft, the most common malware are trojans and worms.

The Trojan does not self-replicate, does not implant a file like a virus, but is instead installed on the system by posing as legitimate and harmless software that then allows the hacker to take control of the computer remotely. One of the most common purposes of a trojan is to make a computer part of a botnet. Botnets are a series of computers connected over the Internet that are used to send spam or do denial-of-service attacks that bring down websites.

Worm
Capable of self-replicating without implanting a host file. They also often use the Internet to spread, thereby causing serious damage to an overall network, while viruses usually only target files on the infected computer. Worm spreads mainly due to security holes of the system. So as a precaution, you need to install the latest security updates for your computer's operating system.

Rootkit
Actively "stealth" from the eyes of the user, the operating system and anti-virus/anti-malware programs, rootkits are malware that are difficult to detect. Rootkits can be installed in many ways including exploiting vulnerabilities in the operating system or gaining administrative rights to a computer.
Once installed and with full administrative rights, the rootkit will hide itself and change the status of the operating system and software to prevent future detection. Rootkits will disable anti-virus programs or implant themselves in the core of the operating system, so your only option may be to reinstall the entire operating system.