Journey of encryption technology
When it comes to coding , it's easy to think of footage of long-running code that flashes on the screen with cryptic messages. Or the recent battle between Apple and the FBI about the encrypted information that the US government forced Apple to decrypt information on the iPhone of the culprit in the shootings in San Bernardino, USA. Simply put, encryption is a technique that makes content unreadable to anyone without a key . Spies use encryption to send confidential information, military commanders send encrypted content to coordinate combat for synchronization, while criminals use encryption to exchange information and plan onions. dynamic.

Encryption systems also appear in almost every technology-related field, not only hiding information of criminals, enemies or spies, but also authenticating and clarifying very basic information. personal. The story of coding in this article covers coding techniques many centuries ago, as it is as complicated as the algorithm that built it. The article also contains the current reviews of industry-leading encryption experts, addressing many aspects of coding: history, current status, and how encryption is absorbed in life. .
The origin of modern coding
Professor Martin Hellman sat at his desk pretty late one night in May 1976. 40 years later, at the same desk he talked about what he wrote that night. Hellman wrote a study titled " New Directions in Cryptography " (new directions in coding techniques), and this research brochure changed the way we keep secrets today, and less much impact on internet encryption now.
Before that booklet, encryption was a very clear principle. You have a key to decrypt unreadable, encrypted content.
And to encrypt efficient operations, keys, or passwords, must be secure . Today, with complex coding systems, the same applies. The complexity of technology and the importance of cryptography from World War II formed several coding systems that many encryption systems today still rely on.
The Allies have SIGSALY , a system that blends in real-time voices . The key to this system is the phono- like recordings of each other, which are played simultaneously while keeping the conversation turned on. When a person speaks in the phone, his voice is digitized and mixed with his own noises. This encrypted signal is then sent to the SIGSALY station, which will decode the audio. After each conversation, the records were canceled and each conversation had a different set of keys. This makes the opponent very difficult to decipher immediately.
The Fascist faction was then based on a similar technology but intended to encode text : that Enigma machine had a hard keyboard, connection cables and a board similar to the switch board of electricity. voice, swivel wheels and an output circuit. Clicking on a key, this device will launch a mechanism for generating different characters, which appear on the board in turn. An Enigma machine configured just like the original machine will also perform the reverse process but is exactly the same as the original machine. From there, messages can be encrypted and decrypted very quickly as soon as typed, and the password changes every time a character is entered. For example, you press the A key, the machine will display the letter E, but you press the A key again, the machine will display another character. Manual plugins and manual configurations mean there are countless variations that can be applied to this system.
Enigma and SIGSALY can be considered primitive versions for an algorithm (or multiple algorithms), showing that a mathematical function is repeated many times. Breaking Enigma code by English mathematician Alan Turing, shows how the coding method is.
But in many ways, Hellman's work on cryptography is different. One of them was that he and another partner mathematician, Whitfield Diffie (also from Stanford University) did not work for any government. The other difference then was that the code for him was nothing new.
Public key encryption (public key)
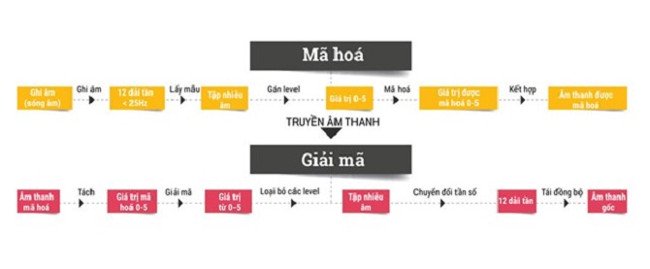
Hellman and Diffie, with the help of another partner Ralph Merkle, offer a completely different encoding. Instead of relying on a single key for the entire coding system, they offer a two-key system . The first key is the private key, which is stored secretly as the traditional password is stored. Anyone who interferes with the message can only see a bunch of meaningless characters. And Hellman will use this secret key to decrypt the message.
This solution immediately proved feasible, but think about SIGSALY. For this system to operate, both senders and recipients need identical keys. If the recipient loses the key, they will have no way to decrypt the message. If the key is stolen or copied, the message may also be decrypted. If the bad guys have enough data about the message and have time to analyze the message, the likelihood of unlocking is also very high. And if you want to send a message but don't have the correct key, you can't use SIGSALY to send the message.
Hellman's public key system is different, meaning that the encryption key doesn't need to be kept secret . Anyone who uses a public key can send messages, but only those who have a private key can decrypt it. Public key encryption also eliminates the means of securing encryption keys. Enigma machines and other coding devices are strictly protected, and Nazi Germany is ready to destroy Enigma if discovered by the Allies. As for a public key system, anyone can exchange public keys with each other, without any risk. Users can share public keys together publicly and combine them with the private key (or secret key) to create a temporary key called shared secret. This hybrid lock type can be used to encrypt messages that shared secret groups share with each other.
One of the factors promoting Hellman to encode is his passion for mathematics, especially modular arithmetic. According to Hellman, the reason he applied arithmetic to congruent coding is that this method is easy to convert data into intermittent data, difficult to reverse, and this is very important for coding.
Therefore, the simplest way to decode is "guessing". This method is also called brute-forcing, applicable to anything else, not just encryption. For example, you want to unlock someone's phone by combining 4 number keys from 0-9. If the detector turns in, it can take a lot of time.
In fact, Merkle had previously developed a public key encryption system before Diffie and Hellman published the " New Directions in Cyptography " work, but at that time Merkle's system was too troublesome for the coders themselves. refers to users. And this trouble was removed by Hellman and Diffie.
A good problem
Bruce Schneier is considered one of the few famous mathematicians in the world, but he is an anonymous character for many. Schneier is very frank and he understands the value of a good problem. He argued that the coding system is a mixture of different and logical maths and a complex system. " Encryption is a theory of numbers, it is a theory of complexity. There are many types of coding very bad because its creator does not understand the value of a good problem. "
According to Shneier, the most fundamental challenge in encryption is the security of the system, but the best proof is to try to decode it. But that coding system is only truly recognized as well when it has been proved by the community over time, through analysis and through its reputation.
Of course, mathematics is much more reliable than humans. Schneier said: " Math has no units to manage. For an encryption system to have management units, it needs to be embedded in the software, put it into an application, run it on a computer that has operating system and user. And these factors are the loopholes of the coding system . "
This is a big problem for the coding industry. Some company can offer encryption systems and commit to users that " Don't worry, no one knows what your message content is " because they are encrypted. But for an ordinary user, who knows what the company can do with the encryption system, especially when the encryption system is granted its own intellectual property license, not for outsiders. investigation and testing. Encryption experts can't prove whether the system is really good, not to mention whether or not the encryption system has a backdoor installed.
Digital signatures
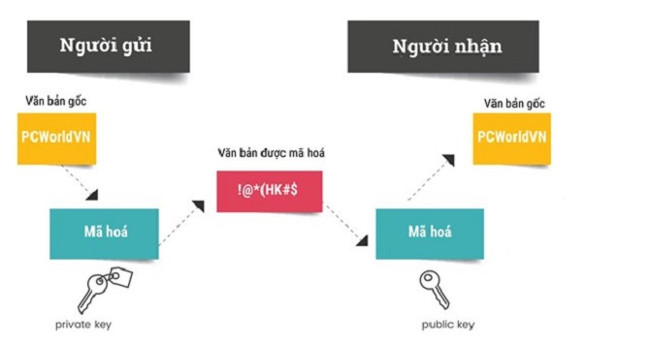
One of the common applications of a public key encryption solution is a digital signature to verify the validity of data. Like a handwritten signature, the purpose of a digital signature is to verify that the data content is correct by its creator.
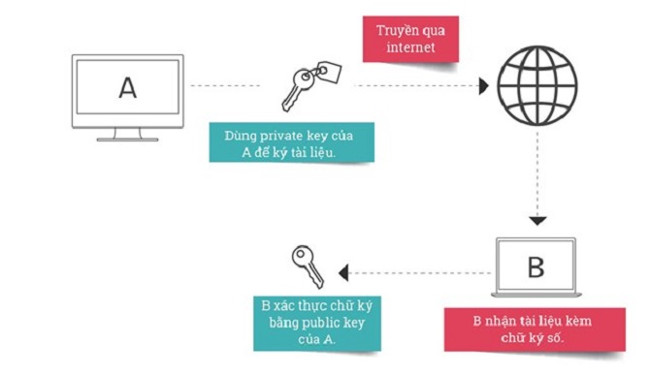
Normally, when securing a message with a public key, you must use the recipient's public key to encrypt the message so that no one can read the message without the recipient's private key. But digital signatures work the opposite way. You compose a contract and use private key to encrypt it. And anyone who has your public key can view the contract but cannot edit it (because your private key is not available). The digital signature confirms the author of the contract, as a signature, to confirm that the content has not changed.
Digital signatures are often used with a software to authenticate content taken from a trusted source and not tampered with by bad guys. Typical examples are the unlocking of the FBI iPhone 5c and Apple. After the FBI tried to use brute-force techniques to guess the PIN code to log in 10 failed attempts, the device automatically cleared the content. Apple has assigned the device's operating system a secret private key and every iPhone has another Apple public key. Secret key is used to authenticate software updates.
Blockchain is growing
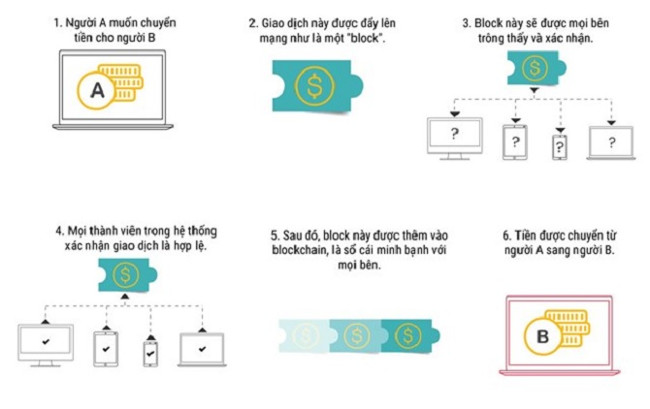
Encryption not only to hide content but also to authenticate whether the content is original or not . Therefore, blockchain appears, technology is considered as popular as encryption.
Blockchain is a fixed, distributed ledger, designed to be completely immune to any digital impact, even if you use it for digital currency, for contracts. Because it is decentralized through many users, there is no point for bad guys to attack. Its power lies in numbers.
No blockchain looks like blockchain. The most famous application of this technology is digital currency, like Bitcoin (this is the currency that cyber criminals, the most used ransomware extortion software maker today). But IBM and some other big companies are also popularizing digital currencies in the business world.
There are not many businesses still using blockchain, but its features are very attractive. Unlike other information storage systems, the blockchain system uses a mixed set of distributed database design and encryption solutions.
IBM's Blockchain allows members to block other people's authenticated blockchain without knowing who is performing the transaction on the blockchain and users can set access permissions, who can execute the transaction. . The design idea of the blockchain is the identity of the person who made the transaction encrypted, but encrypted using a public key . The middle stand has a transaction auditor, has a public key to track transactions and deal with issues between trading members on the blockchain. The auditing course of the middle person can be shared among auditors.
Therefore, using this system, competitors can trade with each other, on the same blockchain. This may not seem intuitive at first, but blockchain is more powerful and safer when there are more traders. The more people, the harder it is to break the blockchain. Try to imagine if all banks in a country participate in a blockchain, transactions will be much safer.
Application coding
Content encryption to send a secure message is one of the most basic technologies. But today's coding is not only that but also applicable to many other jobs, most notably online shopping.
Because every stage in a financial transaction involves a certain type of encryption, or some form of authentication to confirm whether the message has the right person for the right job. And the point of coding sensitive information to make sure no third party intervenes more clearly. Many organizations support internet users to use VPN (virtual private network) to encrypt their internet connection, especially when they have to use public Wi-Fi. An unsecured Wi-Fi network can be created by bad guys to steal information on that Wi-Fi network.
In addition, application encryption not only encrypts sensitive information, personal data, but also allows users to prove that it is really "me". For example, if you go to a bank website, the bank has an encryption key that only the computers at that bank can identify. It is a private key when exchanging with a public key. In the website address bar, there is a small lock icon at the top of the URL, which means that when you visit the bank website, there is an underground key exchange to connect from your computer to the machines. The bank's calculation and authentication process are taking place.
Encrypted signatures are also widely used in financial transactions. Credit / debit cards use embedded chip technology (not magnetic cards), also apply cryptographic signature solutions.
According to experts, encryption is the technology that users currently use a lot but really do not understand about it, from technology equipment to banking transactions, transportation .

Quantum coding can change everything
In 1970, Martin Hellman said it was a breakthrough year in factoring in arithmetic (dividing factors), also known as continuous factor division. The difficulty of dividing large numbers is what makes coding systems more stable and harder to crack. So any technique that reduces the complexity of dividing factors also reduces the security of the encryption system. Then, in 1980, another mathematical breakthrough made it easier to divide factors, thanks to the global (quadratic) sieve of Pomerance and Richard Schroeppel's research. Of course, there was no computer encryption at that time. The size of the encryption key doubled in 1970, and by 1980 this size doubled again. By 1990, lock had doubled. Every 10 years from 1970 to 1990, the greater the size of the encryption key. But by 2000, there was no mathematical progress on encryption keys and Hellman argued that mathematicians had reached the maximum limit of encryption key patterns.
But quantum computing opens up a new horizon, because with a quantum-coding system, the system can really crack every existing encryption mechanism. Today's computing is based on binary 0-1 to operate. As for a quantum system, on the other hand, it relies on very specific quantum properties to operate, not just the state or 0, or 1 like binary, which can help this system simultaneously many calculations.
With an existing coding system, it can take millions of years for an average computer to decode. But with a quantum computer, also with that decoding algorithm, the system can only take from a few minutes to a few seconds to solve. On the Internet we only use a few algorithms to encrypt everything. Therefore, with a complete quantum system, existing coding systems seem like only a thin screen.
If you wonder why so many big countries like the US and China are spending a lot of money to invest in quantum computing, then maybe above is part of the answer. The result that quantum computing brings is beyond the reach of the current computing system.
But when quantum computing became popular, a new branch of mathematics appeared, using more statistical methods, to ensure that when the next generation of computers appeared, encryption was not lost.
Quantum itself caused Einstein's heart attack, but that was just one of several threats to modern coding. The real trouble now is that many large governments and organizations are trying to find ways to weaken encryption for national security reasons. In fact, this conflict has been around for decades, like Crypto Wars of the 1990s, like the CLIPPR chip in the NSA system, which was designed as a backdoor for encryption in the US mobile communications system. And of course, in the last few years, we are shifting our focus from eliminating the encryption system to providing backdoors or " master keys " to cracking security of applications, universal messaging systems. turn.