IronKey: Simple and safe when surfing the web via Wi-Fi
The IronKey USB flash drive is known as a very secure data storage device with strong encryption and password protected access. However in this article we want to introduce you to an interesting feature of IronKey, which is a simple and safe way to surf the Web.
Simple but still safe
For a long time, we have always been looking for a simple and safe way for employees to work around the road when browsing the web. There are two main factors to answer this 'simple but safe' problem, since it must first be a simple installation process or not need to use it. Secondly, the network technology located below must be secure or IT organization will not allow it to be used.
Simple 'yes', safe 'no'
The ultimate of simplicity is that it will allow these mobile workers to simply plug in an open Ethernet port or combine open Wi-Fi networks at a certain hotel or hotspot. Those are all so-called simple things for mobile workers who are away from their home or office. So what's wrong in that scenario? We all probably know that unencrypted data flow is a problem in this case. There are countless ways to capture your network traffic, allowing anyone the ability to build a data stream, or even worst, to get a combination of passwords and usernames. used by mobile workers.
'Yes', simple 'no'
Most people will also agree that the ultimate security issue for mobile workers is to use a VPN application after connecting to any open Wi-Fi network. The data stream will be encrypted so that anyone who can capture this data stream can not interpret the content. This might be a great idea, but why don't we use such a virtual private network at all times? If it's simple, VPN applications have additional needs that cannot be allowed on the network being used by mobile employees. For example, certain additional ports may have to be open all the time and the network needs to manage additional issues by VPN.
What is going to happen
VPN technology is said to be secure, allowing mobile employees to access corporate networks and the Internet through a corporate firewall. So what happens if the VPN is not set up or certified incorrectly by using a certain hotspot? Or in the case of employees who are not part of a business entity but have VPN service? Is it OK to just plug in and open the Web browser? The answer here will be no, but what exactly will happen here. Is there any way to neutralize these two issues?
There are indeed some safe ways to surf the web when you use open Wi-Fi networks. The problem is that they require additional client software and investment funding for some services that provide information security. One of the examples of this problem is Anonymizer and Megaproxy. Both of these products are very safe but not entirely simple for mobile workers when using them.
IronKey
A product that could be called acceptable for the phrase 'simple still safe' that we discovered was IronKey. Besides creating a secure storage device with 'bullet-free bulletproof' protection mechanism, the IronKey development team added what they called 'Secure Sessions Service'.
The secret to the success of this method is that IronKey uses TOR technology. That means that the Internet exchange point is the IronKey server / firewall that is maintained to provide users anonymity and security against Internet threats.
One of the interesting features in using TOR network technology is the ability to surf without exposing your public IP address. The idea is to perform a data flow jump between several TOR servers and eventually exit from the IronKey network. Only the generic IP address visible here is the last TOR server. IronKey allows you to decide which server to use, and can see the path of the data stream as shown in the example below. If you want to change a branch in the circuit diagram, just right-click on the line that appears and close it.
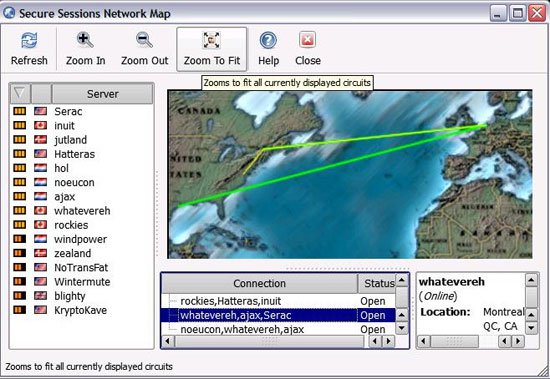
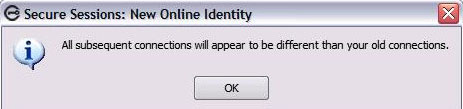
The only feature that adds another layer of security is the ability to change the IP address at any time during the browsing session. You select this feature from the control panel and the IP address is changed as shown in the window below.
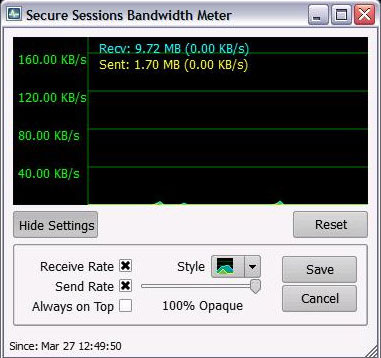
One drawback of network security applications is that they make network management heavy. Developers are still trying to keep this additional traffic to a minimum as possible. If the data throughput appears here to be a problem, you can see the current sending and receiving rates in the bandwidth meter. For example, there may be a low branch, by selecting another branch, the speed will be improved as shown in the bandwidth meter.
There are many solutions to make secure access acceptable for remote users, but most people require a dedicated computer or a device that a mobile computer can connect to. connect with it. IronKey may be the 'simple yet safe' solution businesses are looking for.