Instructions for setting up an Apple ID security key
From iOS 16.3 onwards, Apple has set up a physical security key to enhance the security of users' Apple ID accounts. This physical security key will minimize the possibility of account hacking, thereby revealing your personal information for malicious purposes. Here are instructions for adding an Apple ID security key.
What is an Apple ID security key?
As mentioned above, the Apple ID security key enhances account protection from attacks, hacking accounts to steal information and personal data.
A security key is a small third-party hardware device that can be connected to an iPhone and used to verify identity when signing in to an Apple ID account. The physical key replaces the verification code used in Apple ID two-factor authentication, preventing attackers from eavesdropping or infiltrating information.
Instructions for setting up an Apple ID security key
Step 1:
At the interface on the phone, first access the Settings section and then click on your current Apple ID account . Then switch to the new interface, the user clicks to set up Password & Security .


Step 2:
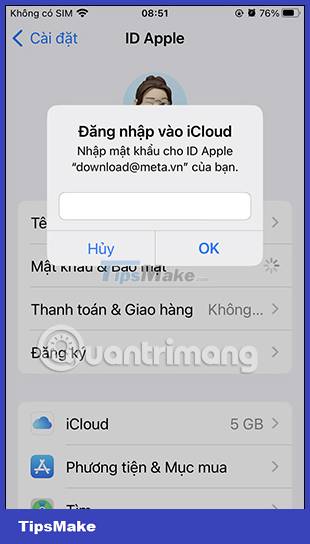
Now you are asked to enter the Apple ID account password to be able to access the security settings for the account on iPhone.
Step 3:
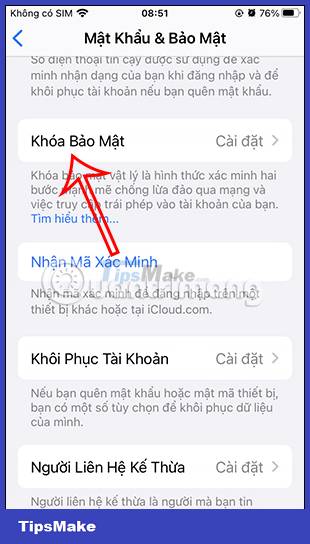
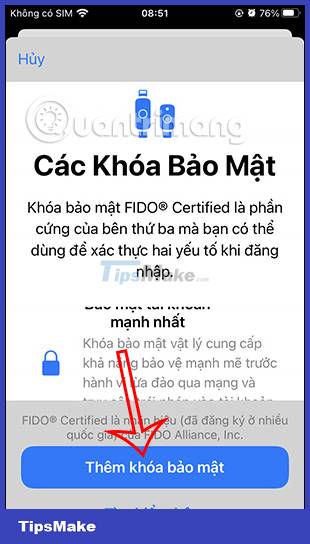
In the next interface, we click on the Security key to proceed with the setup. Here you will see an introduction to the physical security key for the Apple ID account, we click Add a security key and follow the instructions displayed on the screen to continue.
Step 4:
When you sign in to a device, website, or app with a security key, connect to the physical security key and follow the instructions displayed on the screen.
Step 5:
In case the user wants to delete the security key he has set up, we also click on Settings, select your Apple account and then select Password & Security.
Next, click Use key and then Delete all keys to delete the used security key.
If you remove all security keys from iPhone, the device will revert to using six-digit verification codes for two-factor authentication.